When planning a public key infrastructure, the question naturally arises as to which key lengths should be selected for certification authority and end certificates.
The consideration of cryptographic procedures and their evaluation with regard to their usability can only ever be a snapshot at the time of publication of the article. The evaluation may well be outdated in the future, e.g., due to security incidents or technical progress.
It is also possible to sign certificates with Elliptic Curve Cryptography (ECC) keys. However, since this has hardly played a role in practice to date, the use of ECC has only been superficially included in the elaboration.
Key strength assessment
For a better understanding, it is worthwhile to compare the RSA key lengths with a well-known symmetric method such as AES. For this, elaborations can be found at the American National Institute for Standards and Technologies (NIST) and the German Federal Office for Information Security (BSI).
| Key length (RSA) | Key length (ECC) | Comparable symmetric key length |
|---|---|---|
| 1024 | 160 | 80 |
| 2048 | 224 | 112 |
| 3072 | 245 | 128 |
| 7680 | 384 | 192 |
| 15360 | 512 (521) | 256 |
Recommendations
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
- The U.S. National Institute for Standards and Technology (NIST) recommends RSA key lengths of 2048 bits if the keys and the data they protect are not to be used beyond 2030.
- The German Federal Office for Information Security (BSI) recommends RSA key lengths of 3000 (3072) bits if the keys and the data they protect are to be used beyond 2022.
- The current recommended maximum for RSA keys with a Microsoft Certificate Authority is 4096 bits.
Key length selection
The choice of key length depends on several factors:
- How long will the keys be in circulation?
- Can all my applications handle the selected key length?
- What is the computational cost of using the keys?
When selecting the key algorithm and length, the intended usage time must also be taken into account.
For example, an S/MIME certificate may have a validity period of only a few years, but perhaps the encrypted data protected with it should be kept secret for much longer.
RSA key lengths greater than 4096 bits can no longer be used sensibly in most cases because the computational effort increases disproportionately compared to the gain in key strength. Keys based on elliptic curves are clearly more efficient here, so these should be given preference.
What about application compatibility?
In 2020, most applications should be able to handle 4096-bit RSA keys. This does not necessarily have to be the case for longer key lengths.
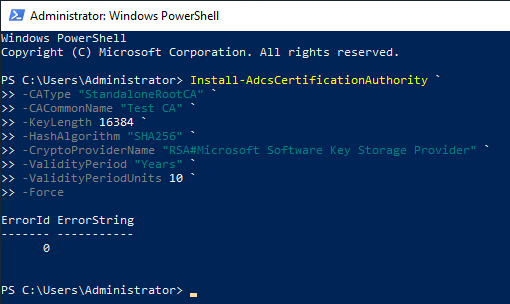
All Microsoft CSP and KSP can generate and use RSA keys up to 16384 bits. However, the Graphical Installation Routine for the Microsoft Certificate Authority will not allow key lengths above 4096 bits.
If necessary, longer keys can be generated by installing the certification authority via PowerShell. It should be noted, however, that the used Key Storage Provider (KSP) (for example, when using a hardware security module) must also support these key lengths.
It should also be noted that with RSA keys, the computational overhead increases extremely with increasing key size, and larger keys are therefore useful in very few cases - it will definitely have an impact on the performance of all applications that will use the certificates.
Summary
The following constellation turns out to be useful in many cases:
- RSA keys for certification authority certificates should have a key length of at least 3072 bits, but no more than 4096 bits, due to the expected long validity period of the certificates.
- Provided that compatibility is ensured, (efficient) higher bit security can be achieved by using ECC keys.
- RSA keys for end-entity certificates should have a key length of at least 2048 bits, but preferably 3072 bits.
Related links:
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
- List of certificate use cases for which compatibility with elliptic curve (ECC)-based keys is known
External sources
- Recommendation for Key Management, Part 1: General (National Institute for Standards and Technology)
- The Case for Elliptic Curve Cryptography (National Security Agency, archive link)
- Maximum key length for cryptographic provider in AD CS 2012R2 (Microsoft Technet Forums)
- BSI TR-02102 Cryptographic methods: Recommendations and key lengths (German Federal Office for Information Security)
- CNG Key Storage Providers (Microsoft)
6 thoughts on “Welche Schlüssellängen sollten für Zertifizierungsstellen und Zertifikate verwendet werden?”
Comments are closed.