Assume the following scenario:
- A Certification Authority will migrated to another server or restored from backup.
- A Thales (nCipher) hardware security module (HSM) is used to protect the private key of the certification authority certificate. Security World is configured with Operator Card Set (OCS) Protection.
- The Certification Authority certificate was successfully restored and associated with the private key stored on the HSM..
- When installing the certification authority role, the restored certification authority certificate cannot be selected.
Cause
Since Operator Card Set (OCS) Protection is enabled, a dialog for entering OCS PINs is invoked when the certificate's private key is accessed, but it is not displayed by the Server Manager.
This error seems to occur only with the Thales/nCipher Key Storage or Cryprographic Service Providers to appear. The Utimaco providers, on the other hand, seem to display the dialog correctly.
Solution
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
There are two ways around the problem:
- You can deactivate the Operator Card Set (OCS) Protection temporarily. For the implementation, please refer to the manufacturer-specific documentation.
- You can temporarily install the certificate authority role with a new certificate or certificate request and then overwrite the configuration with the original certificate.
Details: Installation with a new certificate and subsequent overwriting with the correct certificate
To work around the problem, a new certificate (for a root certification authority) or a new certificate request (for a subordinate certification authority) can be generated during role configuration for the certification authority.
The certificate or certificate request is directly discarded after the installation of the certification authority role and replaced with the correct one.
For this purpose, the option "Select an existing private key on this computer" is selected.
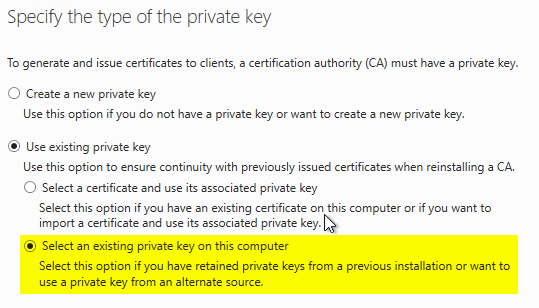
In the next dialog, the filter criterion is edited by selecting "Change..." so that the key storage provider of the HSM manufacturer is selected (in the example, that of Utimaco).
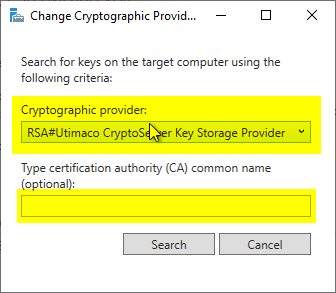
The filter on the common name of the certification authority must either be left blank or the exact common name of the certification authority must be entered.
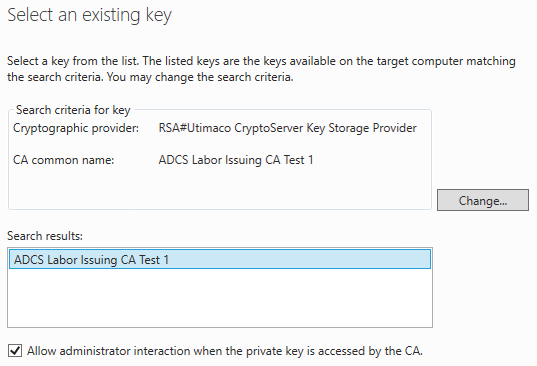
The available keys should now be displayed.
At this point, it is important that the option "Allow administrator interaction when the private key is accessed by the CA" is selected in order to be able to interact with the key storage provider later.
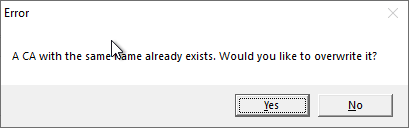
If the certificate authority to be restored is an Active Directory integrated (Enterprise CA), it is indicated that there is already a certificate authority with the same name in the network. We confirm that we want to proceed with "Yes".
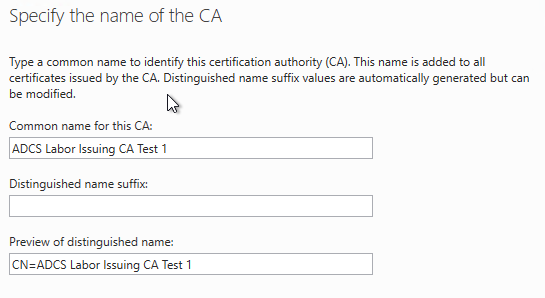
In the next dialog we specify the name of the certification authority.
The Common Name must be exactly the same as that of the certification authority to be restored. The distiguished name suffix, on the other hand, is irrelevant.
Now you can continue with the regular recovery process for the certification authority.
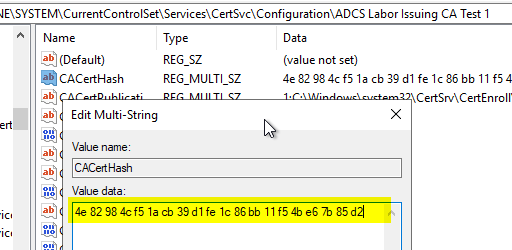
When restoring the certificate authority registry, the "CACertHash" registry value from the backup will be overwritten and thus point back to the correct certificate(s).
The certificate generated in the case of a root certificate authority during role configuration should still be deleted from the personal certificate store and from the certificate store for trusted root certificate authorities via the system account certificate management console (certlm.msc) afterwards.
Related links:
- Migration of an Active Directory integrated certification authority (Enterprise Certification Authority) to another server
- Restoration of a Certification Authority Certificate with Hardware Security Module (HSM)
- Removing old certification authority certificates from the configuration of a certification authority
External sources
- Restoring Standalone Root CA using existing key and associated certificate (Microsoft TechNet Forums)
One thought on “Bei der Wiederherstellung einer Zertifizierungsstelle ist das Zertifizierungsstellen-Zertifikat bei der Rollen-Installation nicht auswählbar”
Comments are closed.