The following describes the effects on certification authority operation if the revocation information for one of the certification authority's certificates cannot be retrieved.
This case may also occur as planned, for example, when a previous certification authority hierarchy is to be decommissioned.
Possible scenarios
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Case 1: The current certification authority certificate is affected
The certification authority always uses the latest, i.e. most recently installed, certification authority certificate to issue its certificates. If this certificate is affected, the certification authority refuses to start the service, but this can be circumvented under certain circumstances. More information can be found in the article "The certification authority service does not start and throws the error message "The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)".„.
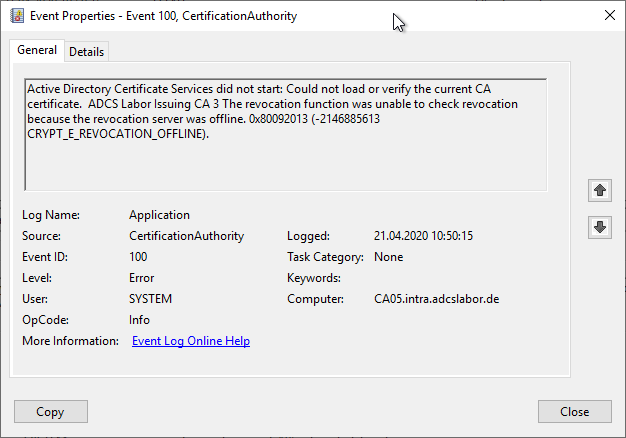
The Certification Authority will use the Event no. 100 log:
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
Case 2: A previous certification authority certificate is affected
If one of the previous certification authority certificates is affected, the certification authority service starts normally.
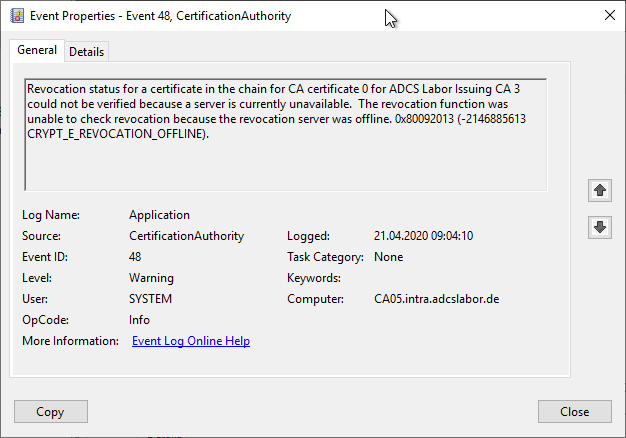
However, the Certification Authority will use the Event no. 48 log:
Revocation status for a certificate in the chain for CA certificate 2 for ADCS Labor Issuing CA 3 could not be verified because a server is currently unavailable. The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
Related links:
- The certification authority service does not start and throws the error message "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT)"
- The certificate authority service does not start and throws the error message "A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING)".
- The certificate authority service does not start and throws the error message "The certificate is revoked. 0x80092010 (-2146885616 CRYPT_E_REVOKED)".
- The certificate authority service does not start and throws the error message "0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)".
- What impact does the revocation of a certification authority certificate have on the certification authority?
- What impact does the revocation of the trust status of a root certification authority certificate have on the certification authority
2 thoughts on “Welchen Einfluss haben fehlerhafte Sperrinformationen eines Zertifizierungsstellen-Zertifikats auf die Zertifizierungsstelle?”
Comments are closed.