Secure administration of Linux systems includes avoiding SSH logins by password and instead logging in with RSA keys.
The de facto standard for SSH connections on Windows is PuTTY. Here, logon with RSA keys is implemented, but only key files can be used, which has the disadvantage that they are almost unprotected in the file system.
Surely a great option would be to use RSA keys from the Windows world, and perhaps even stored on a physical or virtual smartcard.
A deliberate distinction is made here in the terminology between keys and certificates. The SSH server on the Linux system does not check the certificate because the trust status is mapped directly to the public key. The certificate used here should therefore be understood more as a vehicle for being able to use the Windows on-board resources for SSH logon via public key.
PuTTY itself does not support the use of certificates for SSH login. There is support with PuTTY-CAC but an open source fork which has implemented this functionality.
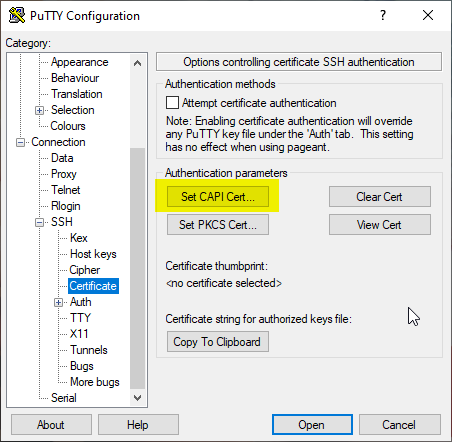
PuTTY-CAC adds a new option "Certificate" under Connection - SSH. Here you can select the option "Set CAPI Cert" to set a certificate on the Windows certificate store for the SSH login.
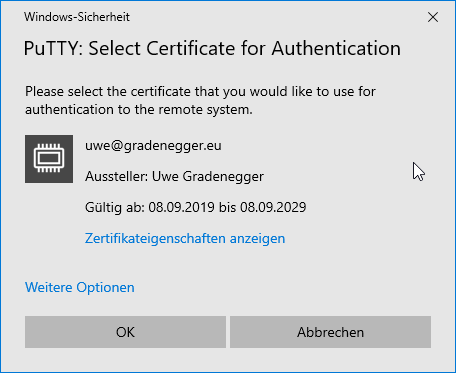
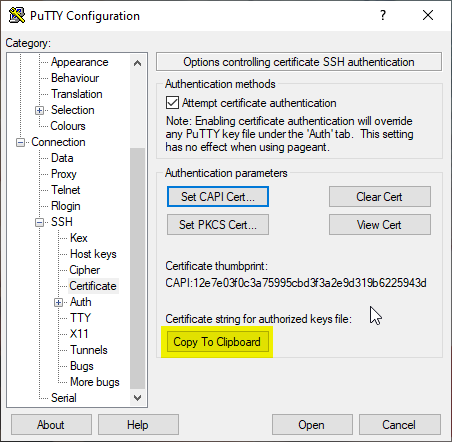
After the selection has been made, the corresponding public key must be made known to the respective system. For this purpose, there is the option "Copy to Clipboard", which copies the necessary information to the Windows clipboard.
On the target system, log in one last time in the traditional way and edit the file for the authorized keys. These can be:
- ~/.ssh/authorized_keys2 (Debian/Ubuntu)
- /etc/dropbear/authorized_keys (OpenWRT)
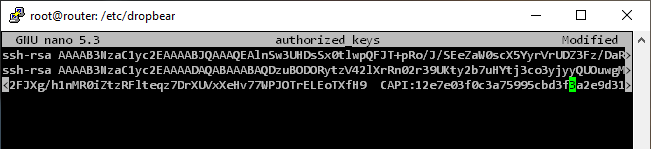
After the new value has been entered and the file has been saved, a logon with the previously selected certificate can now take place.
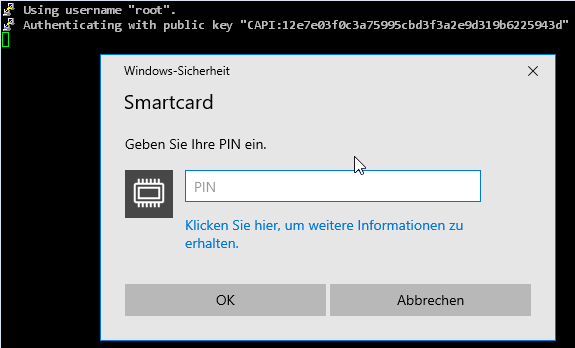
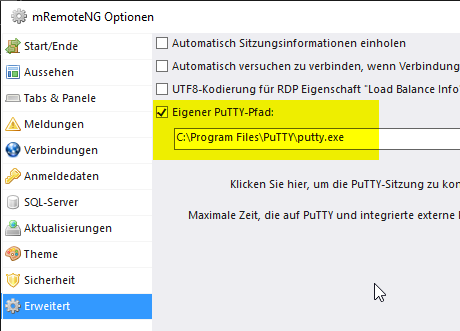
The popular remote desktop application mRemoteNG brings its own copy of PuTTY, but can be instructed to use the PuTTY-CAC file in the options under "Advanced".
Related links:
External sources
- NoMoreFood / putty-cac (GitHub)
- PuTTY-CAC