Assume the following scenario:
- A Windows role concerning Active Directory Certificate Services (Certification Authority, Network Device Enrollment Service (NDES), Certificate Authority Web Enrollment (CAWE), Certificate Enrollment Web Services (CEP, CES), or Online Certificate Service Provider (OCSP)) is to be installed or uninstalled.
- The installation or uninstallation fails with the following error message:
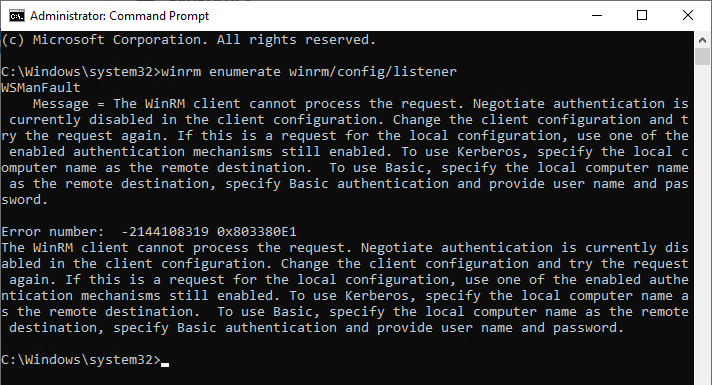
The status of the role services on the target machine cannot be determined. Please retry. The error is The WS-Management service cannot process the request. The service is configured to not accept any remote shell requests.
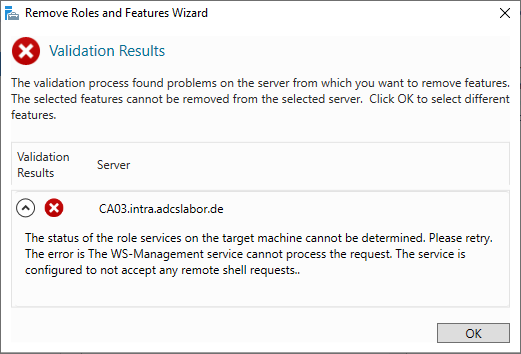
During an installation, the error only occurs if the Server Manager is used. In case of uninstallation, it does not matter whether it is done through Server Manager or Windows PowerShell.
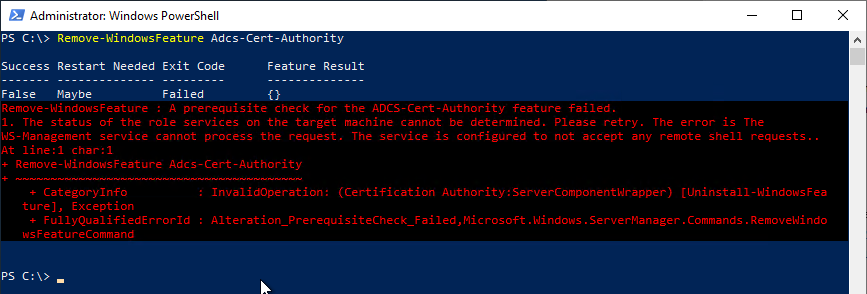
In the Server Manager, you can see that the status for "Remote Management" is set to "Unknown".
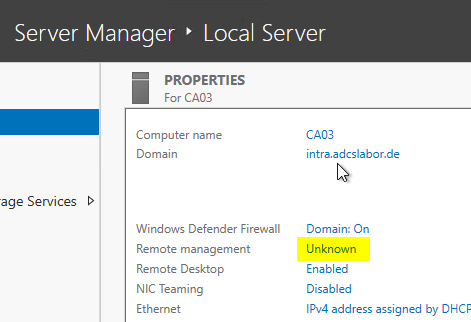
When you click on the status, you get an error message.
Via the command line, the error can be narrowed down with the following command:
winrm enumerate winrm/config/listener
Causes
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Often, the underlying cause is a hardening measure, which in this case shows undesirable side effects.
The error pattern may have the following causes:
- Remote shell connections are not accepted
- Negotiate authentication is disabled for the WinRM client
- Negotiate authentication is disabled for the WinRM server
Details: Remote shell connections are not accepted
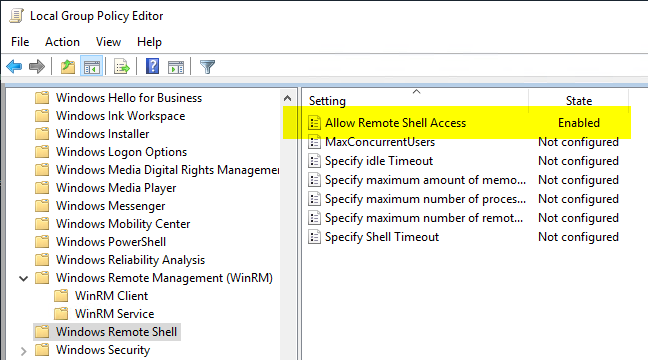
The setting can be set via group policies. It can be found under "Computer Configuration" - "Administrative Templates" - "Windows Components" - "Windows Remote Shell".
The "Allow Remote Shell Access" option must be set to "Enabled" (or "Not configured").
In the registry the setting is shown in the following path:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WinRM\Service\WinRS] "AllowRemoteShellAccess"=dword:00000001
Details: Negotiate authentication is disabled for WinRM client
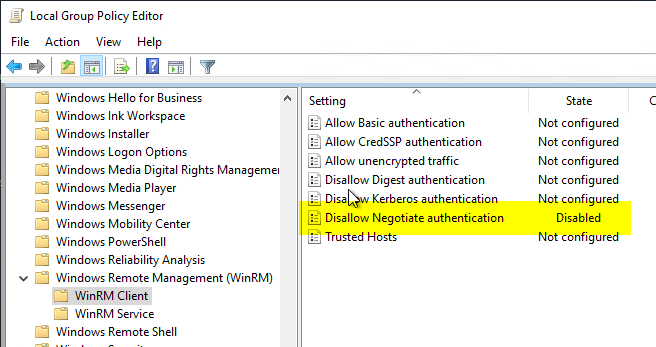
The setting can be set via group policies. It can be found under "Computer Configuration" - "Administrative Templates" - "Windows Components" - "Windows Remote Management (WinRM)" - "Client".
The Disallow Negotiate Authentication option must be set to Disabled (or Not configured).
In the registry the setting is shown in the following path:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WinRM\Client] "AllowNegotiate"=dword:00000001
Details: Negotiate authentication is disabled for WinRM service
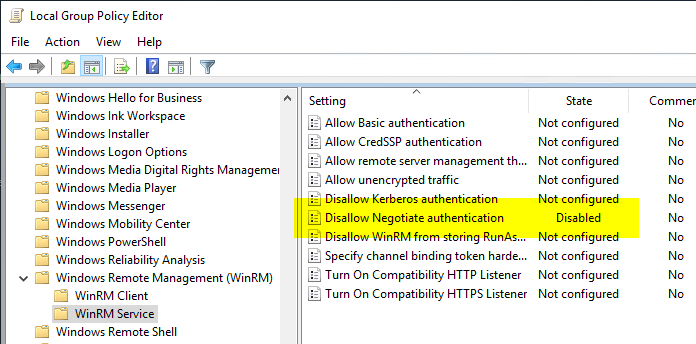
The setting can be set via group policies. It can be found under "Computer Configuration" - "Administrative Templates" - "Windows Components" - "Windows Remote Management (WinRM)" - "Service".
The Disallow Negotiate Authentication option must be set to Disabled (or Not configured).
In the registry the setting is shown in the following path:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WinRM\Service] "AllowNegotiate"=dword:00000001
After modification via registry a restart of the Windows Remote Management service is required.
Restart service WinRM