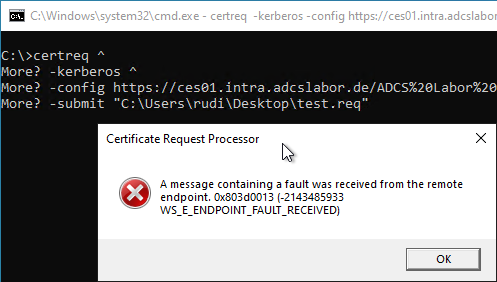
Assume the following scenario:
- A Certificate Enrollment Web Service (CES) is implemented in the network.
- A certificate request is sent to the CES.
- The certificate request fails with the following error message:
A message containing a fault was received from the remote endpoint. 0x803d0013 (-2143485933 WS_E_ENDPOINT_FAULT_RECEIVED)
The Certificate Enrollment Web Services (Certificate Enrollment Policy Web Service, CEP, and Certificate Enrollment Web Service, CES) enable the automatic request and renewal of certificates from a certification authority via a Web-based interface. This eliminates the need to contact the certification authority directly via Remote Procedure Call (RPC). For a more detailed description, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„.
Possible causes
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Cause (delegation of) Kerberos authentication
Most often, the WS_E_ENDPOINT_FAULT_RECEIVED error code means that Kerberos authentication has failed. Possible causes can be:
- The user account of the requesting user may not be delegated.
- The user account of the requesting user may not request certificates from the certification authority.
- The user account does not have the "Request Certificates" right on the target certificate authority (ensured by membership in "Authenticated Users" in the default setting).
- The CES server is not allowed to perform delegated authentication.
- The CES service account (usually represented by membership in the IIS_IUSRS security group) must have the Impersonate a client after authentication (SeImpersonatePrivacy) privilege.
- Credential Guard does not support Kerberos unconstrained delegation, so Kerberos delegation must be constrained.
Cause Key based Renewal
- If Key based Renewal is used, the error can also occur if the account under which the IIS application pool (WSEnrollmentServer) is running does not have read permission on the certificate authority. In this case, the CES will not read the Event #8 log.
- If Key based Renewal is used, the error can also occur if the certification authority has not set the EDITF_ENABLERENEWONBEHALFOF flag. In this case, the CES will use the Event #9 log.
Other causes
- The certificate request was successfully sent to the certification authority, but failed there. In this case, more details are displayed in the error message.
Details
The user account of the requesting user must not be delegated
If the user account has the attribute "Account is sensitive and cannot be delegated" (LDAP flag ADS_ON_NOT_DELEGATED) is set, delegated authentication cannot be performed.
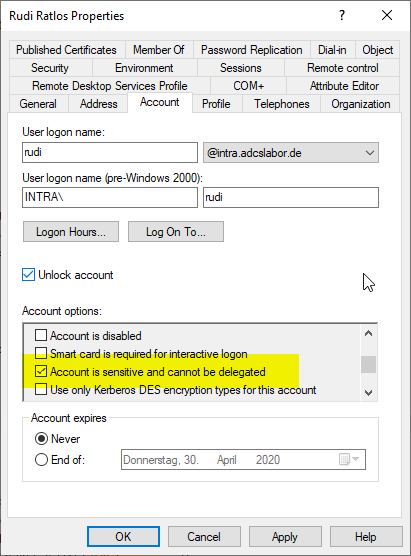
If the setting is changed on the user account, the requesting user must log in again once for the change to take effect.
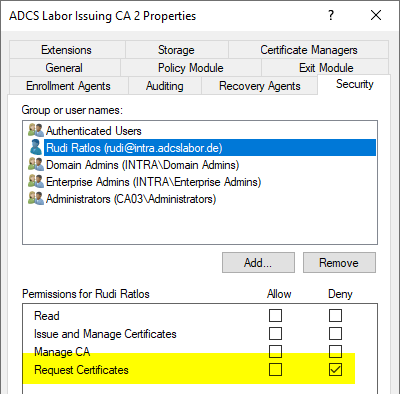
The user account of the requesting user may not request certificates from the certification authority
In this example, the user's "Request Certificates" permission on the certificate authority has been revoked. By default, the "Authenticated Users" have the "Request Certificates" permission.
The CES server is not allowed to perform delegated authentication
The delegation configuration depends on how the CES was set up. For details, see the article "Overview of the possible delegation settings for the Certificate Enrollment Web Service (CES)„.
The IIS_IUSRS security group must have the "Impersonate a client after authentication" permission.
The service account under which the CES service is operated (The identity of the IIS application pool) requires the "Impersonate a Client after Authentication" permission. For more details see the article "Required Windows security permissions for the Certificate Enrollment Web Service (CES)„.
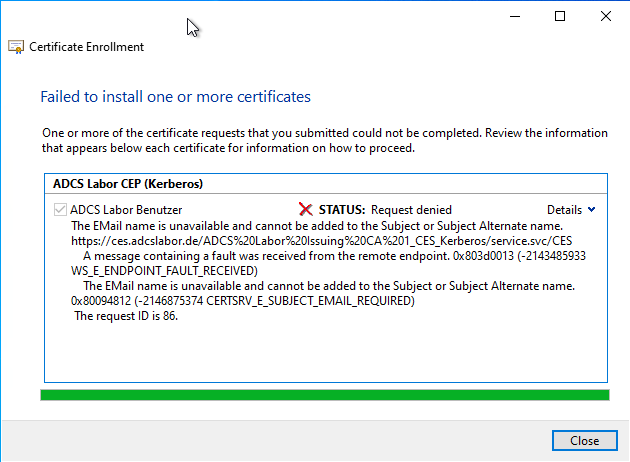
The certificate request was successfully sent to the certification authority, but failed there
The error message can also occur if the certificate request could be sent successfully to the certification authority - i.e. the CES works properly - but the certificate request fails on the certification authority. In this case, however, the WS_E_ENDPOINT_FAULT_RECEIVED error code occurs in combination with the failed certificate request error message.
In the example below, the certificate request fails because the user does not have an e-mail address, but this should be added to the issued certificate according to the settings in the certificate template. Accordingly, the error message 0x80094812 (-2146875374 CERTSRV_E_SUBJECT_EMAIL_REQUIRED) is also issued.
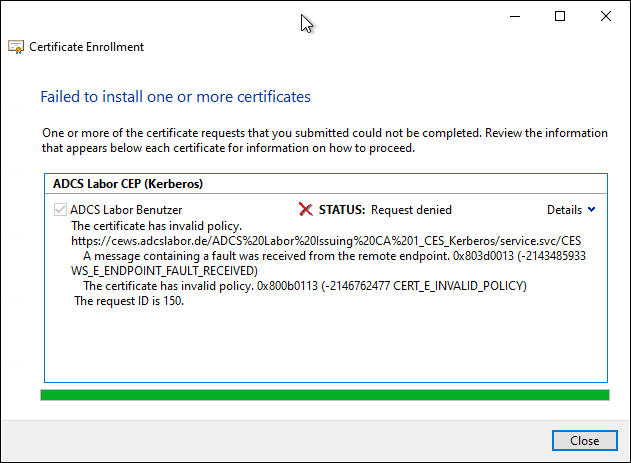
In the example below, the certificate request fails because the configured certificate template contains an invalid issuance policy. Accordingly, the error message 0x800b0113 (-2146762477 CERT_E_INVALID_POLICY) is also issued.
Related links:
- Certificate request basics via Certificate Enrollment Web Services (CEP, CES)
- Required Windows security permissions for the Certificate Enrollment Web Service (CES)
- Overview of the possible delegation settings for the Certificate Enrollment Web Service (CES)
- Basics and risk assessment Delegation settings
2 thoughts on “Die Beantragung eines Zertifikats über den Certificate Enrollment Web Service (CES) schlägt fehl mit dem Fehlercode „WS_E_ENDPOINT_FAULT_RECEIVED“”
Comments are closed.