Here's the scenario:
- Requesting a certificate for a domain controller fails.
- On the certification authority, the certificate request is logged in the failed requests. The error message reads:
The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_SERVER_UNAVAILABLE)
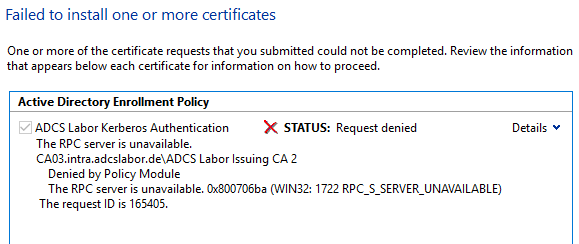
The error is also reported at the certification authority with Event no. 53 logged.
Active Directory Certificate Services denied request 165405 because The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE). The request was for INTRA\DC01$. Additional information: Denied by Policy Module
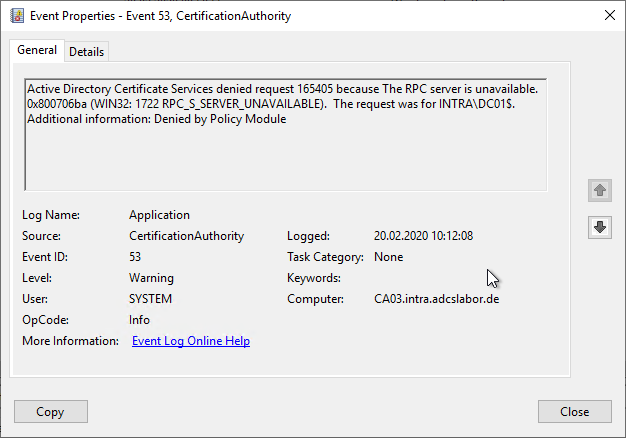
The certificate request is also entered in the list of failed requests in the certification authority, i.e. the transmission of the certificate request from the domain controller to the certification authority obviously worked, but cannot be processed by it.
Possible cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
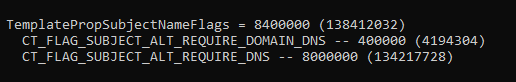
The Kerberos Authentication certificate template and derived certificate templates for domain controllers contain the flag CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS.
This flag causes the certification authority to enter the fully qualified domain name (FQDN) and the NETBIOS name of the requestor in the Subject Alternative Name (SAN) extension of the certificate and requires that the certification authority can talk to the requesting domain controller via NTLM.
This communication takes place via TCP port 445, which must be released accordingly in the firewall configuration of the network.
The error will also occur if NTLMv2 was disabled via group policy.
Testing
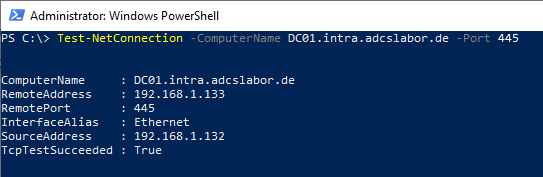
It is relatively easy to check whether this is the cause of the problem using the PowerShell command Test-NetConnection, which must be called from the certificate authority.
Test-NetConnection -ComputerName {name-of-requesting-DomainController} -Port 445
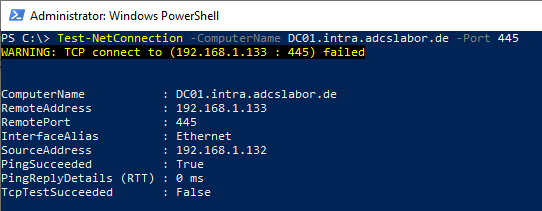
The command must return True for the RPC Named Pipes connection to work.
Trivia
The set flags for a certificate template can be viewed with the following command line command:
certutil -v -template {name-of-the-certificate-template}
Related links:
- Firewall rules required for Active Directory Certificate Services
- Certificates for domain controllers do not contain the domain name in the Subject Alternative Name (SAN)
- Overview of the different generations of domain controller certificates
- Domain Controller Certificate Templates and Smartcard Logon
- Manual application for a domain controller certificate
External sources
- msPKI certificate name flag attributes (Microsoft)
5 thoughts on “Die Beantragung eines Zertifikats für Domänencontroller schlägt fehl mit Fehlermeldung „The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE)“”
Comments are closed.