The purposes for which a digital certificate may be used are controlled via the certificate extensions "Key Usage" and "Extended Key Usage".
In the "Extended Key Usage" certificate extension, the extended key uses for which the certificate may be used.
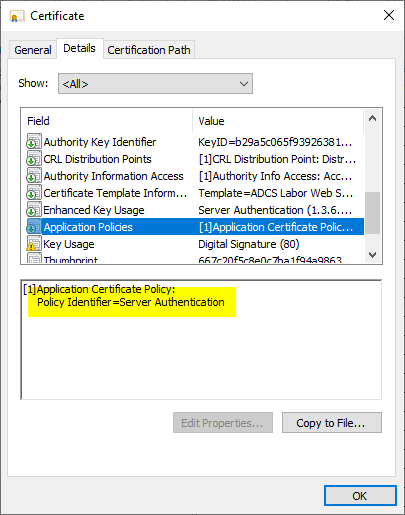
However, there is another certificate extension called "Application Policies" for certificates issued by a Microsoft Certification Authority, which also contains a list very similar to the Extended Key Usages extension.
There may be some confusion about the terminology, as extended key usages are sometimes also referred to as "application policies" (e.g. by certutil and the certificate shell dialog in Windows). Therefore, the discussion must distinguish between the term "Application Policies", which actually means "Enhanced/Extended Key Usages", and the "Application Policies" certificate extension in issued certificates.
Background
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The "Application Policies" certificate extension is a Microsoft proprietary relic from Windows 2000/2003 times.
Application policy is Microsoft specific and is treated much like Extended Key Usage.
Accordingly, the corresponding COM interface is also called IX509ExtensionMSApplicationPolicies, thus contains an abbreviation that indicates a proprietary extension.
The term "Extended Key Usage" is not completely clear-cut. The relevant RFC speaks of "Extended Key Usage", while the term "Enhanced Key Usage" is often used in the Microsoft PKI environment. However, both terms are exactly the same.
Applications that conform to the authoritative RFC 5280 usually do not know about this certificate extension and therefore do not use it. Likewise, they would abort certificate processing if this extension was marked as critical.
Other certification authority products do not include this extension in the certificates issued, so it cannot be assumed that this is supported by all common end-user applications.
The RFC-compliant certificate extension is the "Extended Key Usage" extension.
Since the certificate extension is marked as non-critical by default, it is ignored by applications which do not know it and cannot interpret it accordingly. Thus it effectively has no effect, even if it should be present in a certificate.
The "Application Policies" extension as a security problem
Justin Bollinger from TrustedSec has found outthat there are offline certificate requests against Schema version 1 certificate templates is possible (similar to the Security identifier extension) to send any application policies in the certificate request, which are adopted unchanged in the issued certificate and can then be used for an attack on the overall Active Directory structure (ESC15).
For this reason, it makes sense not to enter the extension in issued certificates.
In general, it is also advisable not to use version 1 certificate templates, but to always use self-defined templates that are derived from the version 2 and 3 certificate templates supplied.
Remove the "Application Policies" extension from issued certificates
By default, the Windows Default Policy module of the certification authority is responsible for writing this certificate extension to issued certificates.
The "Application Policies" certificate extension can be disabled with the following command line command on the certificate authority.
certutil -setreg policy\DisableExtensionList +1.3.6.1.4.1.311.21.10
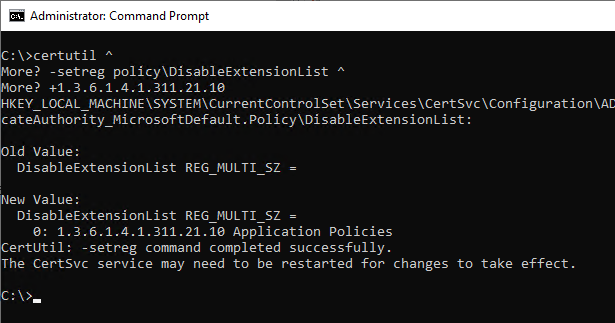
The certification authority service must then be restarted for the changes to take effect.
Certificates issued from this moment on only contain the "Extended Key Usage" extension, but not the "Application Policies" extension.
Related links:
External sources:
- Using Application Policies (Microsoft)
- Object IDs associated with Microsoft cryptography (Microsoft, archive link)
- Request extension processing in Active Directory Certification Authority (PKI Solutions, Inc.)
2 thoughts on “Die „Application Policies“ Zertifikaterweiterung”
Comments are closed.