For the encryption of e-mail messages, companies usually use the Secure / Multipurpose Internet Message Extensions (S/MIME) standard and provide their users with appropriate certificates for this purpose.
An important aspect here is that the users' private keys should be secured centrally - in contrast to the signature certificates that are otherwise mostly used. Incoming messages are encrypted for a specific private key and can only be decrypted again by the same person. Thus a backup of these keys must absolutely be available - also for the Synchronization to mobile devices this is indispensable. For this purpose, the Microsoft Active Directory Certificate Services offer the function of the Private Key Archival.
But what if private key archiving has not been set up and users have already applied for corresponding certificates?
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Fortunately, it is possible to archive private keys - albeit with corresponding effort - even after the fact.
Prerequisite for this are:
- At least one valid Key Recovery Agent certificate has been set up on the corresponding certificate authority.
- The private keys were exported from the user profiles and are available as PKCS#12 (PFX) file including password.
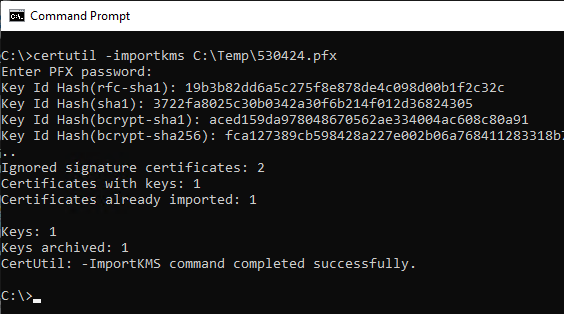
The import into the certification authority can then be done with the following command:
certutil [-p {password>] -importKMS {filename-PFX}
Related links:
External sources
- certutil (Microsoft Corporation)