Assume the following scenario:
- The company would like to use smartcard logon.
- The domain controllers are with certificates that can be used for smartcard logon equipped.
- The users are equipped with certificates that can be used for smartcard logon.
- The login to the domain via smartcard fails with the following error message:
A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)
In German, the error message reads:
The certification chain was processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)
Possible causes
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The error code CERT_E_UNTRUSTEDCA indicates - as the corresponding description text implies - a lack of trust status.
Usually, the certificates involved (domain controller and user certificate) are checked by exporting them to a file and executing the following command:
certutil -verify -urlfetch {filename}.cer
However, you will notice that this command does not reveal any errors:
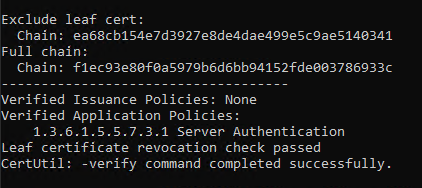
So apparently everything is fine with the certificates?
No.
In addition to the pure trust status for the issuing certification authority, there are other fine-grained statuses:
- If the certification authority is authorized to issue certificates with the corresponding extended key usages (Extended Key Usage, EKU) authorized? (Application Policies)
- Is the certification body authorized to issue certificates with the corresponding certificate guidelines? (Issuance Policies)
- Is the certification body authorized to issue certificates for a PKINIT application? (Membership of the NTAuthCertificates object)
While the first two criteria can still be recognized by the certutil command, this is not the case for NTAuthCertificates membership.
One way to check this is the following command:
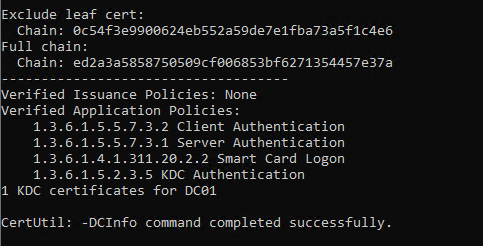
certutil -dcinfo verify
Please be sure to include the keyword "verify"!
Please also consider the following article if the error code "CRYPT_E_NOT_FOUND" appears: certutil -dcinfo fails with error message "KDC certificates: Cannot find object or property. 0x80092004 (-2146885628 CRYPT_E_NOT_FOUND)"
Here we encounter the previous error message again:
A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)
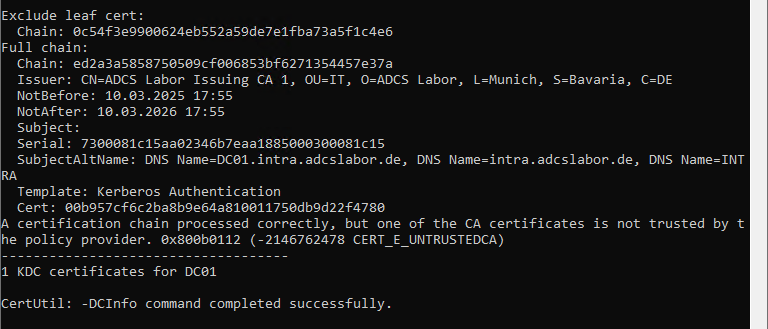
Then it's clear, isn't it? One of our certification authorities is not a member of NTAuthCertificates!
As a rule of thumb: The error code CERT_E_UNTRUSTEDCA always indicates a problem with the membership of a participating certification authority in NTAuthCertificates.
However, a check shows that the certification body is duly registered here:
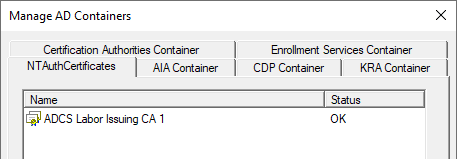
Then why is the certificate not considered usable for PKINIT?
It is important to know that it does not work directly against the data from the Active Directory configuration partition, but against a replica in the local registry of the respective system.
However, this is not automatically activated. So let's have a look:
certutil -v -getreg -GroupPolicy enroll\AEPolicy
See also article "Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM (MS-WCCE)„.
And here we notice that synchronization has apparently been deactivated:
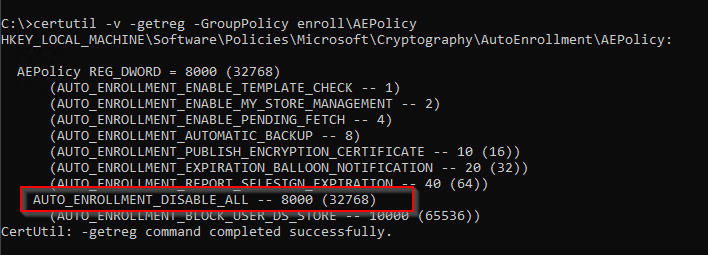
Of course, this is exactly what happens if nothing is configured.
For replication to take place, at least the "AUTO_ENROLLMENT_ENABLE_TEMPLATE_CHECK" flag must be activated. In the corresponding group policy known as "Update certificates that use certificate templates".
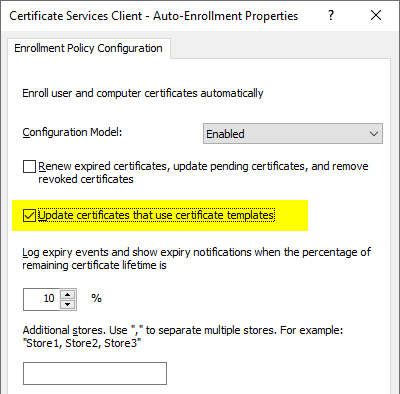
We then apply the group policy and start the synchronization process with the following commands.
For the computer context:
certutil -pulse
For the user context:
certutil -pulse -user
The verification of our domain controller certificates will then also be successful. You should now be able to log in without any problems.
Related links:
- Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM (MS-WCCE)
- Editing the NTAuthCertificates object in Active Directory
- certutil -dcinfo fails with error message "KDC certificates: Cannot find object or property. 0x80092004 (-2146885628 CRYPT_E_NOT_FOUND)"
- Basics of manual and automatic certificate requests via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM) with the MS-WCCE protocol
- Renewal of a certificate via the Network Device Enrollment Service (NDES) fails with error code CERT_E_UNTRUSTEDCA
- Requesting certificates via Enroll on Behalf of (EOBO) fails with the error message "A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)"
- Requesting a certificate fails with the error message "A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)".
- Configuring a Certificate Template for Domain Controllers
- Domain Controller Certificate Templates and Smartcard Logon