When using Active Directory Certificates, it is noticeable that there are certain extensions in the certificates of the certification authorities and the certificates they issue that are not defined in the relevant RFCs and are specific to AD CS.
Which extensions are we talking about?
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
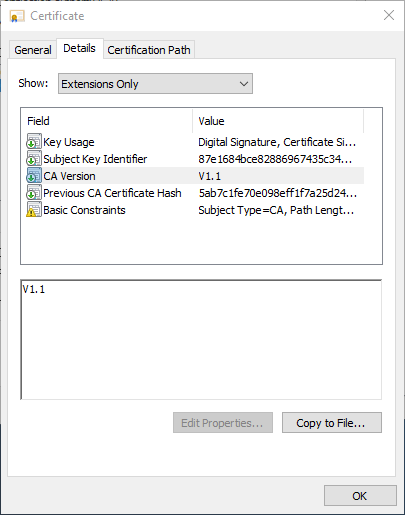
- CA version
- Previous CA Certificate Hash
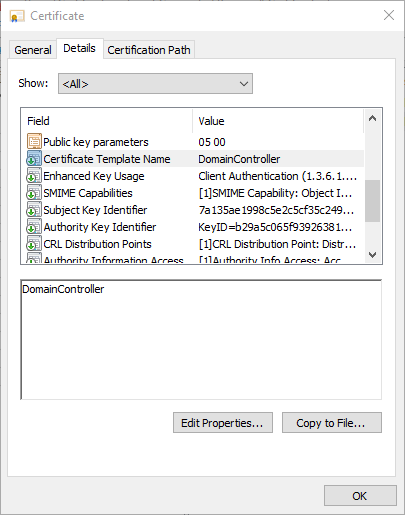
- Certificate Template Name
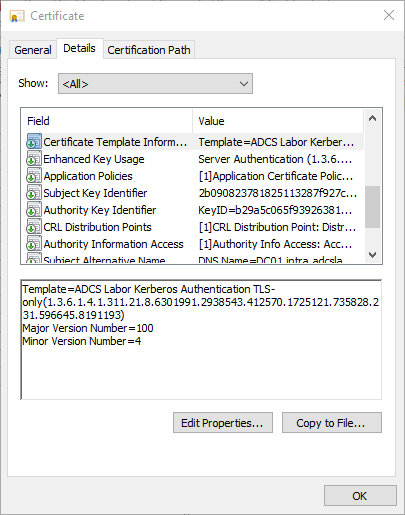
- Certificate Template Information
- Application Policies
The CA version extension describes the versions of the certification authority certificates as well as the private keys.
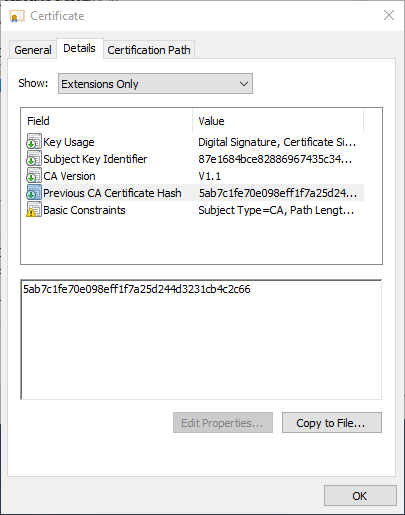
The "Previous CA Certificate Hash" certificate extension contains the SHA1 hash value of the previous certification authority certificate. Accordingly, this extension is also only present in renewed certification authority certificates.
Should these extensions be removed?
The enhancements are all marked as non-critical and should be implemented according to RFC5280 therefore have no negative effects during operation.
A non-critical extension MAY be ignored if it is not recognized, but MUST be processed if it is recognized.
Reasons for their removal could be:
- Applications that misinterpret the extensions despite being marked as non-critical
- Making it difficult to infer a Microsoft certificate authority from the certificates
What are the effects of removing the extensions?
Removing the "CA Version" and "Previous CA Certificate Hash" extensions for certification authority certificates has no negative effects during operation. Only if the Certification authority from a backup should be restored, the correct order of the Certification Authority certificates may not be correctly determined. This must then be checked manually and corrected if necessary.
The Certificate Template Name and Certificate Template Information extensions in end entity certificates are used by various applications (including autoenrollment, domain controllers, and the online responder) and should not be removed.
See also article "The online responder (OCSP) requests new signature certificates every four hours„.
How to remove the extensions?
Removing the extensions for root CA certificates
The configuration is done for the certificates of the root certification authority in its capolicy.inf file, located at C:\Windows\. The configuration must be done before issuing the CA certificate, i.e. either before installing the certification authority, or before renewing the CA certificate.
[Extensions]
1.3.6.1.4.1.311.21.1= ; szOID_CERTSRV_CA_VERSION
1.3.6.1.4.1.311.21.2= ; szOID_CERTSRV_PREVIOUS_CERT_HASH
Removing the extensions for subordinate CA certificates
The configuration is done in the registry of the respective parent certification authority (for example, the root certification authority). The configuration must take place before the CA certificate is issued, i.e. either before the issuing certification authority is installed or before the CA certificate is renewed.
The "CA Version" certificate extension can be removed with the following command:
certutil -setreg policy\DisableExtensionList +1.3.6.1.4.1.311.21.1
The "Previous CA Certificate Hash" certificate extension can be removed with the following command:
certutil -setreg policy\DisableExtensionList +1.3.6.1.4.1.311.21.2
The "Certificate Template Name" certificate extension can be removed with the following command:
certutil -setreg policy\DisableExtensionList +1.3.6.1.4.1.311.20.2
The certification authority service must then be restarted.
Removing the extensions for end-entity certificates
The following extensions should not be removed, because they are needed for some functions:
- The CA version extension should not appear in end entity certificates. However, if further CA certificates are issued under this certification authority, the extension can be removed in the same way as for sub-CA certificates.
- The same applies to the Previous CA Certificate Hash extension.
- Autoenrollment requires the Certificate Template Information extension to function correctly.
- The Online Responder requires the "Certificate Template Information" extension to function correctly.
The "Application Policies" certificate extension on the other hand, can be easily removed with the following command:
certutil -setreg policy\DisableExtensionList +1.3.6.1.4.1.311.21.10
Related links
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Description of the necessary configuration settings for the "Common PKI" certificate profile
- The Online Responder requests new signature certificates every four hours
- The "Application Policies" certificate extension
- Restoring a certification authority from backup
External sources
- Object IDs associated with Microsoft cryptography (Microsoft)
- RFC 5280 Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile / Certificate Extensions (Internet Engienering Task Force)
5 thoughts on “Entfernen der ADCS-spezifischen Erweiterungen aus Zertifikaten”
Comments are closed.