Sometimes it is necessary for a certificate issued by a certification authority to be withdrawn from circulation even before its expiration date. To make this possible, a certification authority keeps a revocation list. This is a signed file with a relatively short expiration date, which is used in combination with the certificate to check its validity.
In some cases (for example, with an offline certificate authority, or if non-standard LDAP revocation list distribution points have been configured), the certificate revocation list must be manually published to Active Directory.
Required permissions
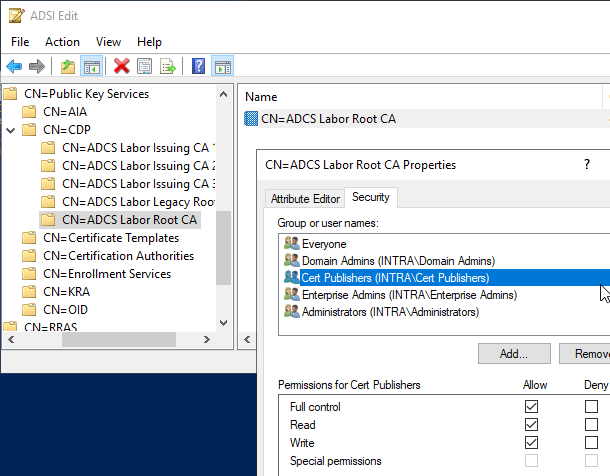
To publish the revocation list in Active Directory, you need write permissions on the corresponding cRLDistributionPoint object in the CDP path below the Public Key Services container in the Configuration partition of the Active Directory forest. This right has in the default setting:
- The Administrators security group of the root domain of the forest
- The Domain Admins security group of the root domain of the forest
- The Enterprise Admins security group of the forest
- The security group "Cert Publishers" of the root domain of the forest
Required configuration on the certification authority
In order for the revocation list to be manually written to Active Directory, a Published CRL Locations extension is required within the revocation list.
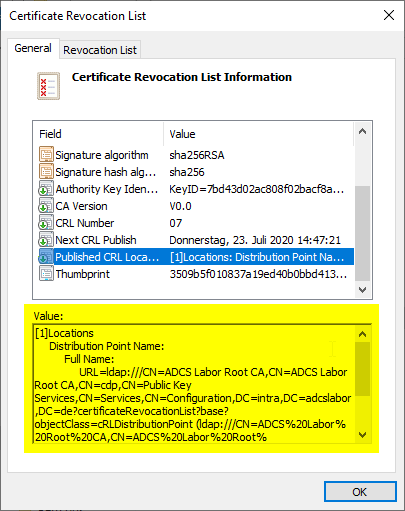
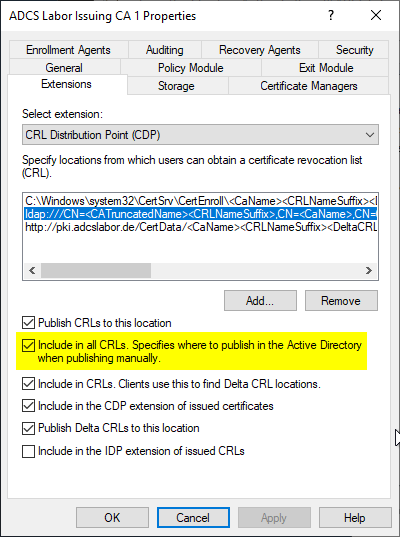
This extension is only written to the revocation list if the option "Include in all CRLs. Specifies where to publish in the Active Directory when publishing manually." has been set.
Create a certificate revocation list
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
If no current blacklist has been created yet, it must be created first. The procedure is described in the article "Create and publish a certificate revocation list" described.
Publish the certificate revocation list in Active Directory
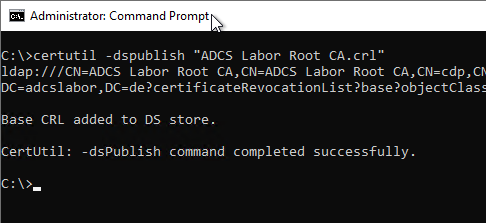
The publication of the certificate revocation list can be executed with the following command line command.
certutil -dspublish {filename}
As mentioned before, the executing user needs write permissions on the corresponding object.
If the object does not yet exist, it must first be created with the "-f" switch. This requires write permissions to the parent LDAP path.
Related links:
- Create and publish a certificate revocation list
- Publishing a certificate revocation list (CRL) fails with the error message "Directory object not found. 0x8007208d (WIN32: 8333 ERROR_DS_OBJ_NOT_FOUND)".
- Manual publishing of a certificate revocation list (CRL) to Active Directory fails with error 0x8007202b (WIN32: 8235 ERROR_DS_REFERRAL)
6 thoughts on “Veröffentlichen einer Zertifikatsperrliste (CRL) auf einem Active Directory Sperrlistenverteilungspunkt (CDP)”
Comments are closed.