After installing a Certificate Enrollment Policy Web Service (CEP), or after more extensive maintenance work, an extensive functional test should be performed to ensure that all components are working as desired.
The Certificate Enrollment Web Services (Certificate Enrollment Policy Web Service, CEP, and Certificate Enrollment Web Service, CES) enable the automatic request and renewal of certificates from a certification authority via a Web-based interface. This eliminates the need to contact the certification authority directly via Remote Procedure Call (RPC). For a more detailed description, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„.
Procedure
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
A functional test of the certificate request policy server includes the following steps:
- Ensure start of the certificate request policy server service
- Checking the Certificate Request Policy Server Event Viewer
- Verify connection to the certificate request policy server
- Create Certificate Enrollment policy
- Query certificate templates via the certificate request policy server
- Apply for a certificate with CEP
Details: Ensure the start of the certificate request policy server service.
Since the certificate request policy server is implemented as a module within the Internet Information Server (IIS) service, it is not possible to control the service startup via the services administration account (services.msc). Instead, a corresponding Event with no. 1 logged in the event display.
However, this is only generated the first time it is called up by a requester, so the "Check connection to certificate request policy server" step described below must be performed first for this purpose.
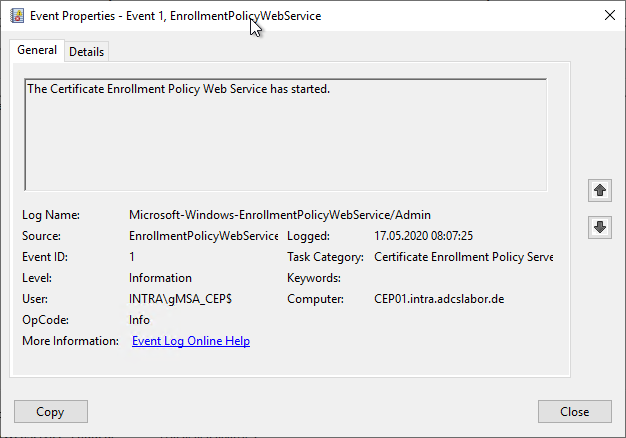
Details: Checking the Certificate Request Policy Server Event Viewer
See also article "Overview of Windows events generated by the Certificate Enrollment Policy (CEP) service„.
First, the Windows Event Viewer on the certificate request policy server should be examined for any relevant events that might indicate an error. For this purpose, there is a predefined view in the event viewer under "Custom Views" - "Server Roles" - "Active Directory Certificate Services", which has already defined the required filters on the event viewer.
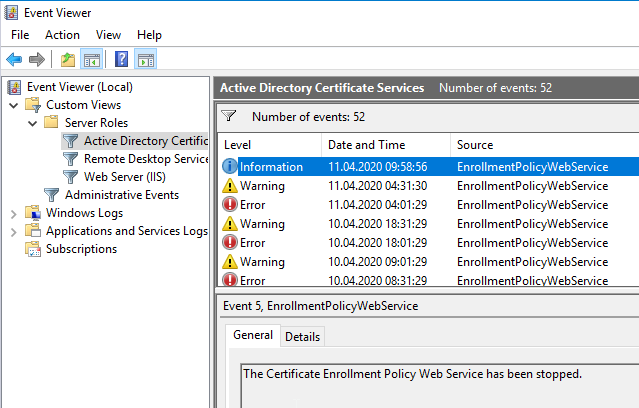
Details: Check connection to certificate request policy server
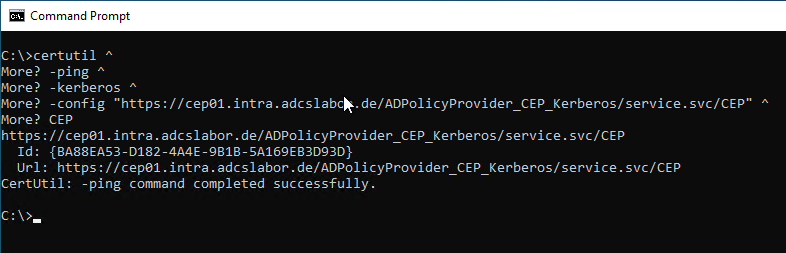
Kerberos authentication can be tested with the following command line command.
certutil -ping -kerberos -config "https://{Servername}/ADPolicyProvider_CEP_Kerberos/service.svc/CEP" CEP
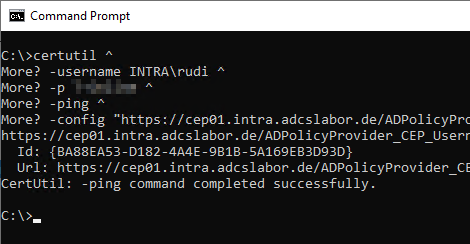
Authentication with username and password can be tested with the following command line command.
certutil -username {domain}\{username} -p {password} -ping -config "https://{Servername}/ADPolicyProvider_CEP_UsernamePassword/service.svc/CEP" CEP
Authentication with a client certificate can be tested with the following command line command.
certutil -ClientCertificate {Thumbprint} -ping -config "https://{ServerName}/ADPolicyProvider_CEP_Certificate/service.svc/CEP" CEP
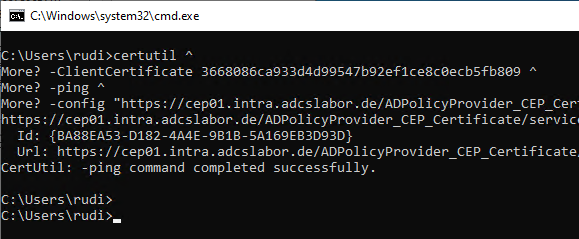
If you encounter problems with this step, the following articles may be helpful:
Details: Create certificate request policy
Now a certificate request policy can be configured. The procedure is described in the article "Configuration of a certificate request policy (enrollment policy) for the certificate request web services (CEP, CES)" described.
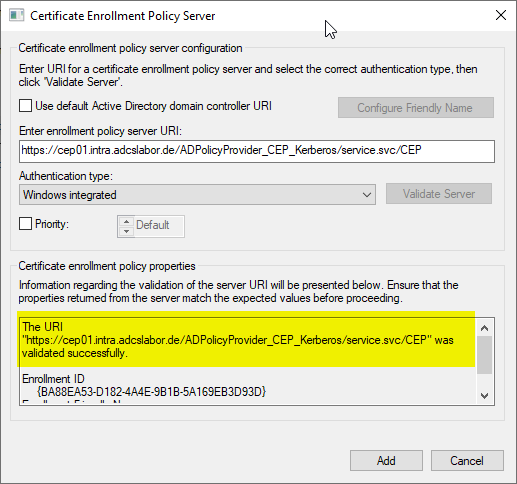
If you encounter problems with this step, the following articles may be helpful:
- The creation of a certificate enrollment policy for the Certificate Enrollment Policy Web Service (CEP) fails with the error message "This ID conflicts with an existing ID."
- Certificate Enrollment Policy creation for Certificate Enrollment Policy Web Service (CEP) fails with error code "WS_E_INVALID_FORMAT".
- Certificate Enrollment Policy creation for Certificate Enrollment Policy Web Service (CEP) fails with error code "WS_E_ENDPOINT_NOT_FOUND".
- Certificate enrollment policy check via Certificate Enrollment Policy (CEP) web service fails with error code "WS_E_ENDPOINT_FAULT_RECEIVED".
- Requesting a certificate fails with the error message "You cannot request a certificate at this time because no certificate types are available."
Details: Query certificate templates via the certificate request policy server
If a certificate request policy has been configured for the current user as described previously, this can now be used to query the certificate templates via the certificate request policy server.
certutil -template -policyserver *
This is cached information that is generated only after a query has been made with the Microsoft Management Consolem (MMC).
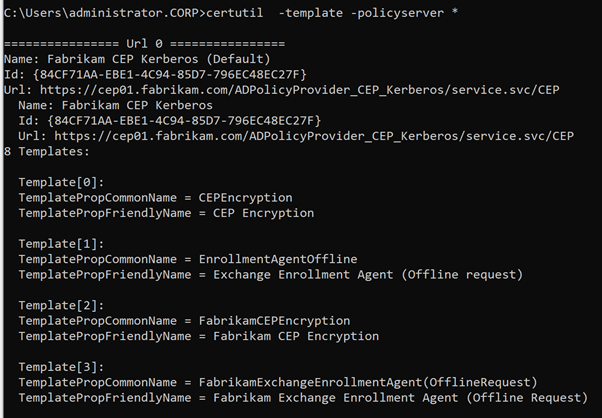
Apply for a certificate with CEP
For this, a Certificate Enrollment Web Service (CES) must also first be installed in the network. A description of the procedure can be found in the article "Installing a Certificate Enrollment Web Service (CES)„.
A certificate enrollment policy can then be set up and a certificate can be requested via Web Services.
If you encounter problems with this step, the following articles may be helpful:
- Requesting certificates via Certificate Enrollment Web Services fails with error message "Error: The remote endpoint is unable to process the request due to being overloaded. 0x803d0012 (-2143485934 WS_E_ENDPOINT_TOO_BUSY)".
- Requesting certificates via Certificate Enrollment Web Services fails with error message "Error: A message containing a fault was received from the remote endpoint. 0x803d0013 (-2143485933 WS_E_ENDPOINT_FAULT_RECEIVED)".
- Requesting certificates via Certificate Enrollment Web Services fails with error message "Error: The operation timed out 0x80072ee2 (WinHttp: 12002 ERROR_WINHTTP_TIMEOUT)".
- Requesting certificates via Certificate Enrollment Policy Web Service (CEP) fails with error message "ERROR_WINHTTP_CONNECTION_ERROR".
- Requesting certificates via Certificate Enrollment Policy Web Service (CEP) fails with error message "The requested certificate template is not supported by this CA."
- Requesting certificates via the Certificate Enrollment Policy Web Service (CEP) fails with error message "A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted."
- Requesting certificates via the Certificate Enrollment Policy Web Service (CEP) fails with error message "Error: Access was denied by the remote endpoint. 0x803d0005 -2143485947 WS_E_ENDPOINT_ACCESS_DENIED".
- Requesting certificates via Certificate Enrollment Web Service (CES) fails with error code "ERROR_WINHTTP_INVALID_CA".
Other possible errors that can occur at this point are causal in the Certificate Enrollment Web Service (CES) are described accordingly in the article "Perform functional test for Certificate Enrollment Web Service (CES)" described.
Rework
If a certificate request policy was set up manually for testing, it can now be removed again. The procedure for this is described in the article "Deleting a Manually Configured Certificate Request Policy (Enrollment Policy)" described.
4 thoughts on “Funktionstest durchführen für den Certificate Enrollment Policy Web Service (CEP)”
Comments are closed.