Assume the following scenario:
- A certificate template is configured for automatic request and issuance (AutoEnrollment).
- Users or computers apply for new certificates at regular intervals and long before the defined renewal period.
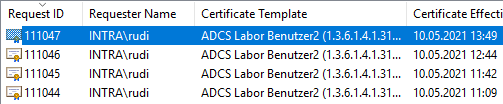
In the certificate store of the user or computer in question, it is noticeable that no information about certificate templates of the certificates in question is displayed.
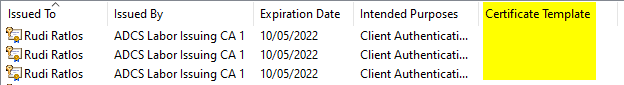
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
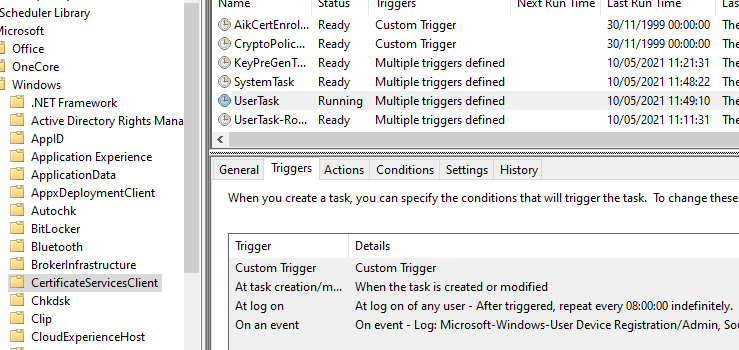
The triggers for an automatic certificate request through the autoenrollment process are:
- When the user logs in (for computers, when the computer account logs in, i.e. at system startup).
- By timer every 8 hours.
- When updating group policies, assuming there has been a change.
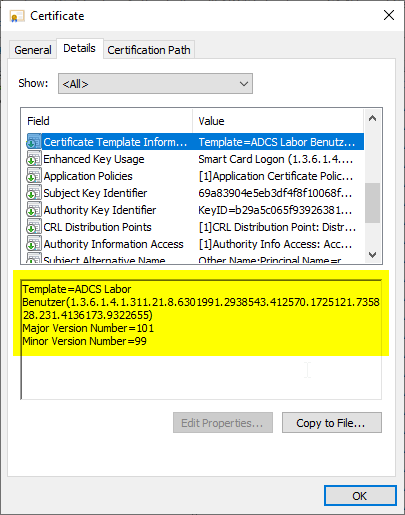
The certificates are reapplied for because they do not include the "Certificate Template Information" extension. This is provided by the Autoenrollment client to be able to determine whether a certificate already exists or whether a new one must be requested. If the extension does not exist, a new certificate request is made each time the autoenrollment process is called.
Most often, the cause can be found in the fact that the corresponding certificate extension has been disabled in the certificate authority's policy module.
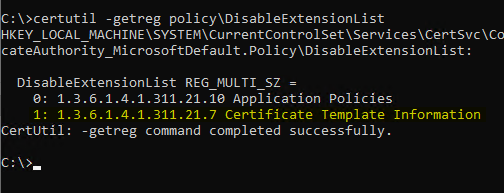
This can be determined with the following command line command.
certutil -getreg policy\DisableExtensionList
If the object identifier 1.3.6.1.4.1.311.21.7 (szOID_CERTIFICATE_TEMPLATE) appears in the list, it is not entered by the certification authority in issued certificates.
The entry can be removed with the following command line command.
certutil -setreg policy\DisableExtensionList -1.3.6.1.4.1.311.21.7
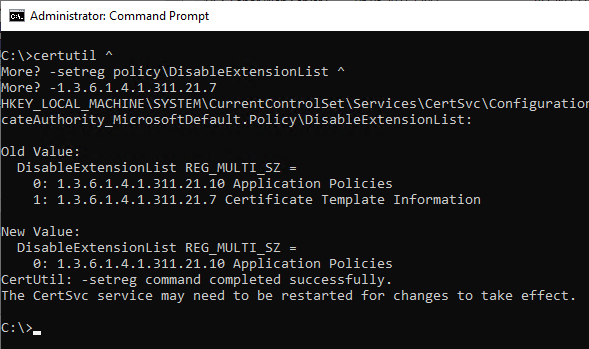
The certification authority service must then be restarted for the changes to take effect.
Now the certificate extension should be re-entered into issued certificates.
Related links:
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Have certificate holders automatically renew all certificates issued for a certificate template
- Removing ADCS-specific extensions from certificates
- The online responder (OCSP) requests new signature certificates every four hours
External sources:
- Object IDs associated with Microsoft cryptography (Microsoft, archive link)
- Request extension processing in Active Directory Certification Authority (PKI Solutions, Inc.)