Below is a description of where it is possible to view which symmetric algorithm was used to encrypt an email received, and which hash algorithm was used for a signed email.
Two approaches are described below:
- Determine via Outlook
- Determine via MFCMAPI and certutil
Determine via Outlook
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Does not work if the message was only encrypted but not signed. In this case the buttons are not available.
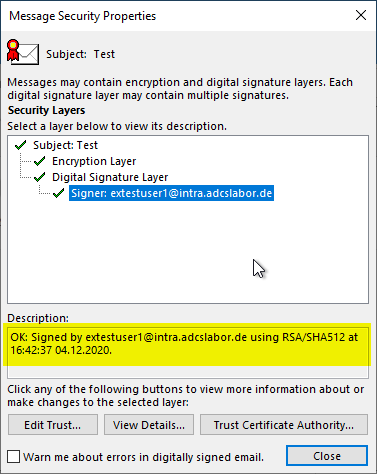
If an email has been received that is both signed and encrypted, two buttons will appear at the top right above the message body.
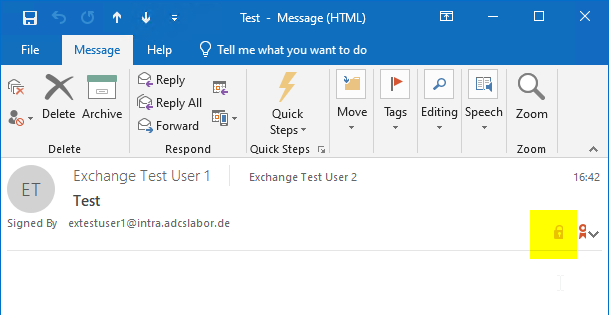
Both buttons will take you to the destination.
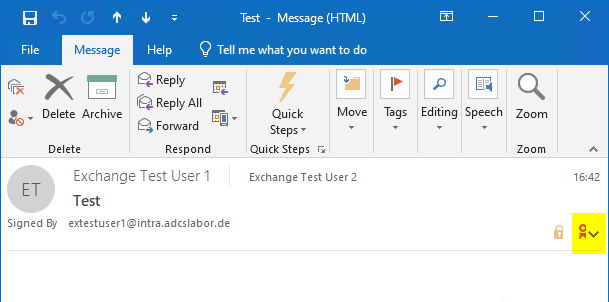
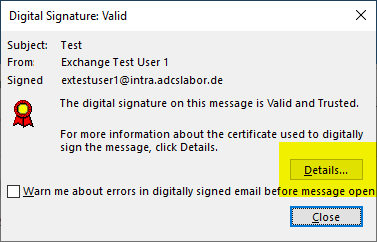
In the signature button, you must first click on "Details".
The information about the encryption algorithm can be found in the "Encryption Layer" section.
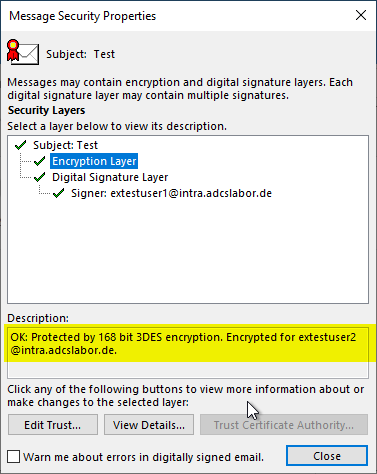
The information about the hash algorithm can be found in the "Signer" section.
Determine via MFCMAPI and certutil
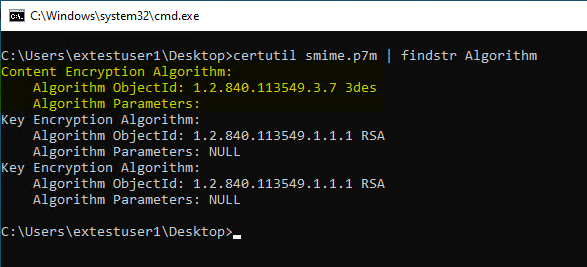
If you have encrypted an S/MIME message using the MFCMAPI exported, one can determine the algorithm with certutil:
certutil smime.p7m | findstr Algorithm
Related links:
External sources
- stephenegriffin / mfcmapi (GitHub)
- View certificates - Outlook (Microsoft)
2 thoughts on “Microsoft Outlook: Einsehen, welcher Algorithmus für eine S/MIME verschlüsselte oder signierte E-Mail verwendet wurde”
Comments are closed.