Was a Remote desktop certificate requested manuallyit must then be assigned to the Remote Desktop session host.
Procedure
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
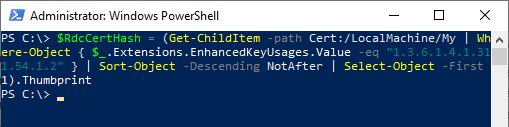
First, the SHA1 fingerprint of the (most recent) Remote Desktop certificate must be obtained. This can be done with the following Windows PowerShell command:
$RdcCertHash = (Get-ChildItem -path Cert:/LocalMachine/My | Where-Object { $_.Extensions.EnhancedKeyUsages.Value -eq "1.3.6.1.4.1.311.54.1.2" } | Sort-Object -Descending NotAfter | Select-Object -First 1).Thumbprint
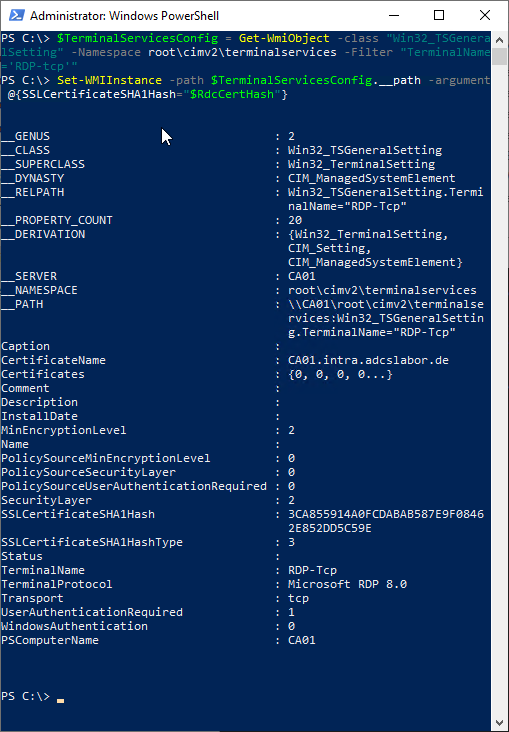
Then, the certificate can be assigned to the Remote Desktop session host using the following Windows PowerShell command via WMI.
$TerminalServicesConfig = Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -Filter "TerminalName='RDP-tcp'"
Set-WMIInstance -path $TerminalServicesConfig.__path -argument @{SSLCertificateSHA1Hash="$RdcCertHash"}
Related links:
- Manually requesting a Remote Desktop (RDP) certificate
- Identify the active Remote Desktop (RDP) certificate
- Configuring a Certificate Template for Remote Desktop (RDP) Certificates
- Configuring a Group Policy (GPO) for Remote Desktop (RDP) Certificates
One thought on “Manuelles Zuweisen eines Remotedesktop (RDP) Zertifikats”
Comments are closed.