Assume the following scenario:
- A certification authority hierarchy is established in the network and the root certification authority is mapped in the configuration partition of the Active Directory forest.
- Domain members are configured to run the autoenrollment process to update trusted root certificate authorities from the Configuration partition.
- However, this process does not work for some clients. The root CA certificates are not automatically downloaded and entered into the local trust store.
- As a consequence certificate requests can failbecause, for example, the certification authority hierarchy is not trusted.
The physical certificate stores can be viewed by right-clicking on the certificate store and selecting "View" - "Options...".
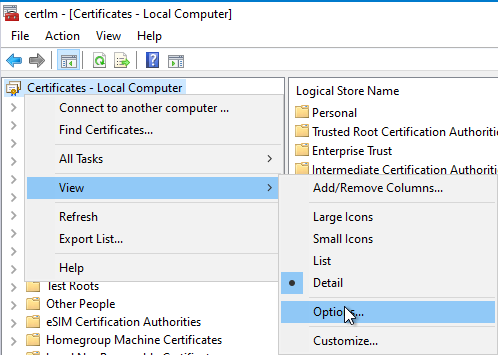
The "Physical certificate stores" option must be selected.
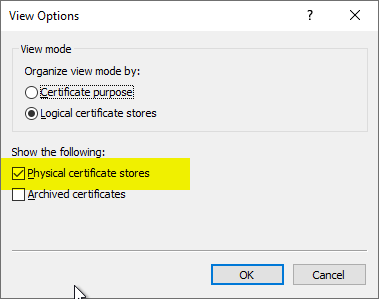
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The most probable cause is that the certificate was manually deleted from the certificate store.
If a certificate is deleted from a store managed by the autoenrollment process and there is no change on the directory service side, the local certificate store is not updated again.
The last synchronization state is cached locally in a registry key called "AEDirectoryCache", in which local deletions are not mapped. Accordingly, a deleted certificate is not restored by the autoenrollment process.
Solution
The following registry key must be deleted on affected clients:
For the machine context:
HKLM\SOFTWARE\Microsoft\Cryptography\AutoEnrollment\AEDirectoryCache
For the user context:
HKCU\SOFTWARE\Microsoft\Cryptography\AutoEnrollment\AEDirectoryCache
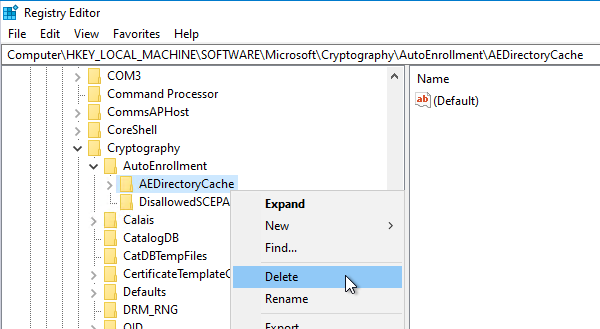
Subsequently, a new synchronization can be attempted.
certutil -pulse [-user]
Autoenrollment must be enabled with the minimum settings (Group Policy: "Not configured", AEPolicy: 0x0).
Related links:
External sources
- Certificate Autoenrollment in Windows Server 2016 (part 4) (Vadims Podans)
- Workstation "retrieving" certificates from AD Central Store (Microsoft TechNet Forums)
- How to Force a DC to Attempt Certificate Autoenrollment (David Ball)
3 thoughts on “Der lokale Zertifikatspeicher für vertrauenswürdige Stammzertifizierungsstellen wird nicht aus dem Active Directory synchronisiert”
Comments are closed.