When troubleshooting, it can be very helpful to view encrypted SSL connections in order to inspect the messages within. There is a relatively simple way to do this with Wireshark.
Please note that TLS is intended for the confidential transmission of data. If you undermine the data security guaranteed by TLS, you may gain unauthorized knowledge of confidential information. The following instructions are only intended for learning purposes in test environments in which no confidential information is transmitted.
The data traffic can be recorded on the server or the connecting client. Both procedures are described below.
It is not mandatory to install Wireshark on these systems, as there is the possibility to analyze the traffic using Windows on-board tools and then convert it into a Wireshark-compatible format for analysis on a technician's computer. See article "Analyze network problems with Wireshark without installing software on production systems„.
Decrypting the TLS data traffic on the client
It is very practical to record the data processing on the client, as a connection can be established directly with the (pre)master key and Wireshark and can therefore be recorded "live". This method is also "minimally invasive"; no system-wide changes need to be made.
Unfortunately, this method only works with common browsers.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Save (Pre)Master Secret
Mozilla Firefox, Google Chrome and the Microsoft Edge (codenamed Anaheim) based on it are able to read an environment variable that instructs the browser to store the (pre)master secrets.
To do this, the computer's properties dialog must first be opened. In the "Advanced" tab, click on "Environment Variables".
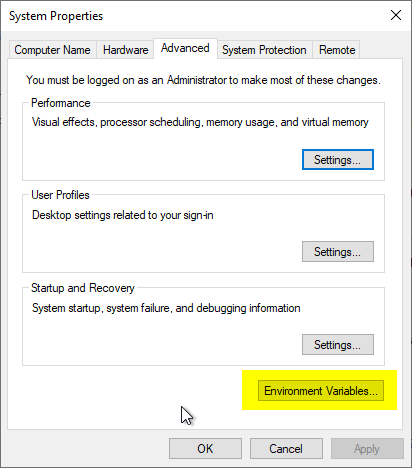
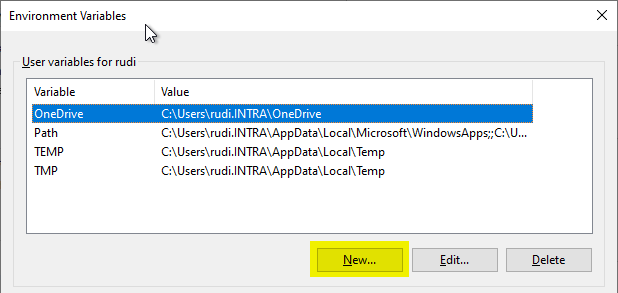
In the following dialog, a new environment variable is created for the current user by clicking on "New".
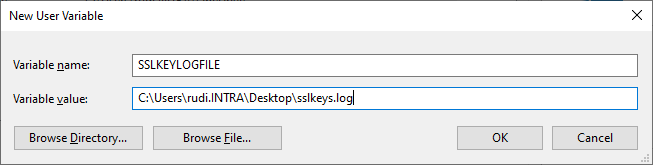
Now the variable "SSLKEYLOGFILE" is created and the path is defined in which the keys are to be stored.
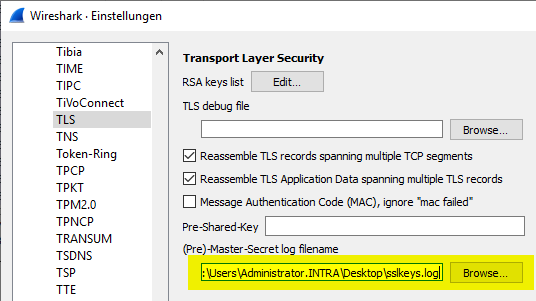
Configure Wireshark
In Wireshark's settings dialog, navigate to "Protocols" - "TLS" and store the previously defined path.
After that, the problem can be reproduced. You should now see that the messages are decrypted and thus the HTTP traffic transmitted in the SSL/TLS connection should be visible.
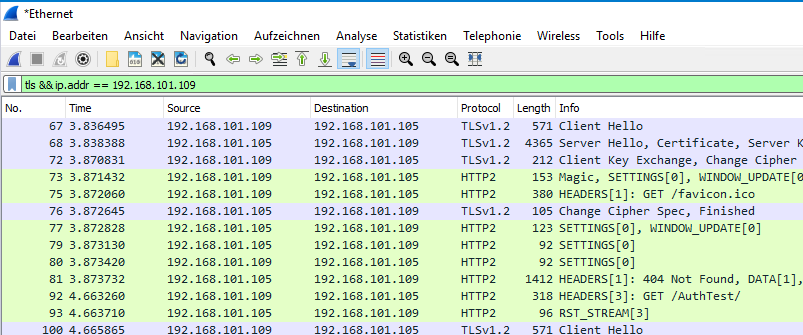
Do not use anymore: Decrypt using private key of the web server
In the past, it was usually also possible to decrypt SSL traffic by specifying the web server's private key.
However, with the widespread use of Perfect Forward Encryption (PFE), this is no longer possible, as PFE makes decryption with the server key impossible. This is a useful feature in terms of data protection, but now requires a new approach for troubleshooting.
If you try it anyway, you will find a corresponding error message in Wireshark's "TLS debug file":
ssl_decrypt_pre_master_secret: session uses Diffie-Hellman key exchange (cipher suite 0xC030 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) and cannot be decrypted using a RSA private key file. ssl_generate_pre_master_secret: can't decrypt pre-master secret
If it is really necessary to decrypt the TLS data traffic with the private key of the web server, the following describes how to deactivate forward encryption on the server side.
Decrypt TLS traffic on the server (Microsoft IIS)
Decrypting the TLS data traffic on the server is somewhat more complex and requires extensive changes to the system.
In the following, we reduce the security settings on the server in order to be able to analyze the data traffic. This should never be carried out on a production system. The changes made should be reversed after analysis and troubleshooting.
The process roughly consists of the following steps:
- Deactivate Diffie Hellman key exchange procedure
- Request and install an SSL certificate with an exportable key
- Deactivate TLS 1.3
- Recording data traffic
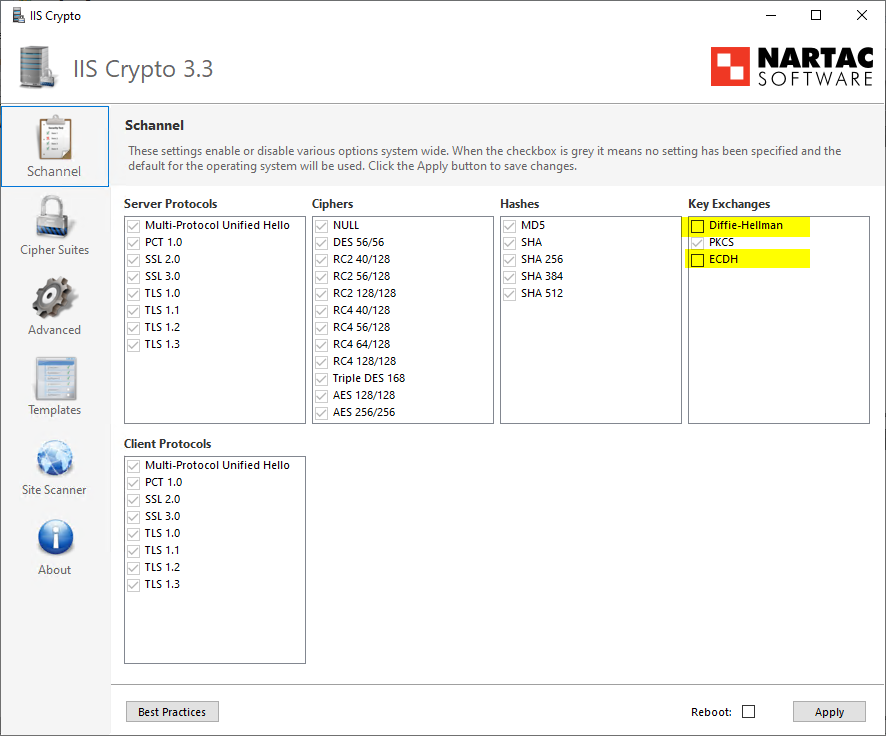
Deactivate Diffie Hellman key exchange procedure
In order to decrypt the TLS data traffic, we must deactivate all key exchange procedures that enable forward encryption. This is done system-wide on Windows systems. An easy-to-use tool is IIS Crypto of the company Nartac Software.
The "Diffie Hellman" and "ECDH" (Elliptic Curve Diffie Hellman) key exchange procedures are deactivated. A restart of the server operating system is then required.
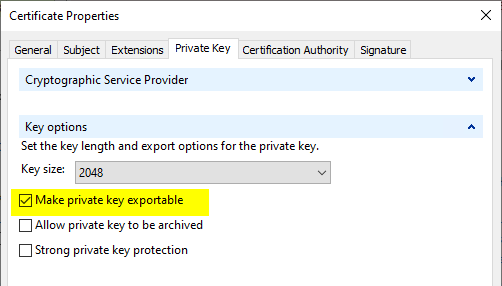
Request and install an SSL certificate with an exportable key
In order to decrypt the data traffic, Wireshark must have the private key of the web server. A TLS certificate with an exportable private key must therefore be available on the IIS web server.
If the currently installed web server certificate does not have an exportable key, a new certificate must be requested. When applying for the certificate, you can specify that the private key should be exportable.
See also article "How secure is the "Allow private key to be exported" setting in the certificate templates?„.
After the request, the web server certificate can now be exported to a PFX file together with the private key.
The new certificate can then be set up in the SSL binding on the web server.
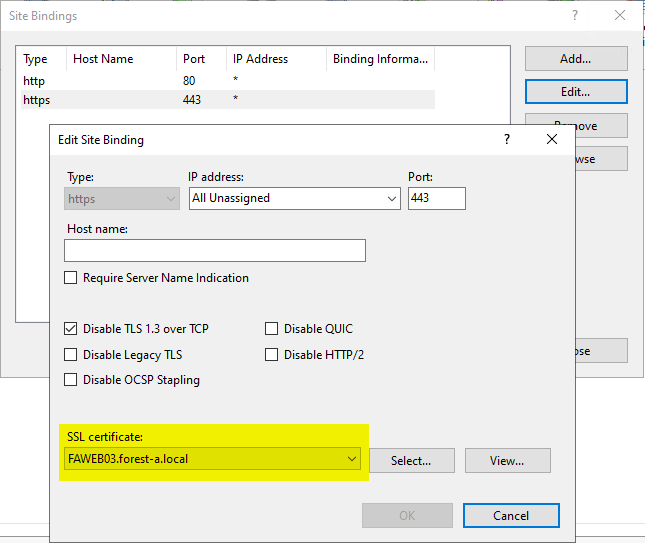
Deactivate TLS 1.3
If Windows Server 2022 or newer is used, TLS 1.3 is supported. In order to be able to decrypt the data traffic, we must deactivate this for the duration of the analysis. This is also done in the configuration of the SSL binding for our website.
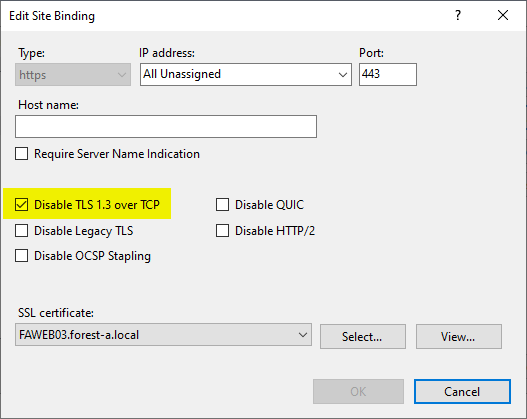
Recording data traffic
The previously created PFX file can now be integrated into Wireshark. This is done in the settings dialog under "Protocols" - "TLS".
The IP addresses can either be specified explicitly or applied to all recorded data traffic by specifying "any". It is essential to specify "http" as the protocol.
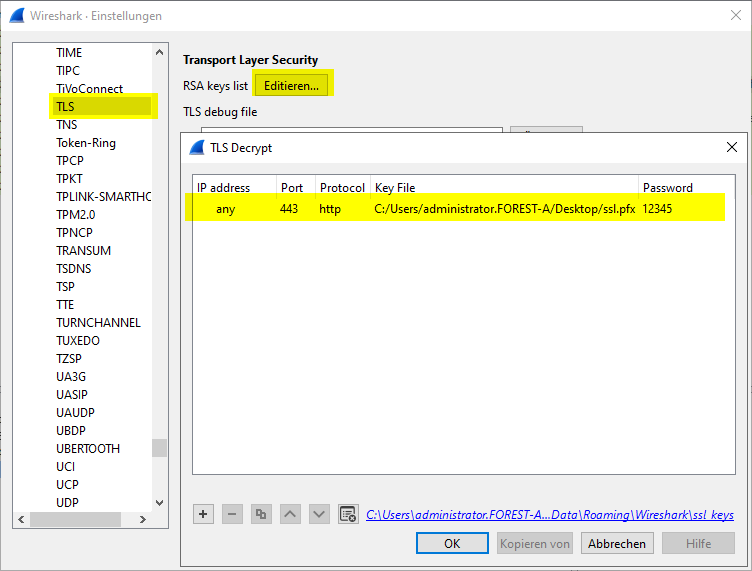
The TLS data traffic can now be recorded. The data traffic should now be visible in plain text.
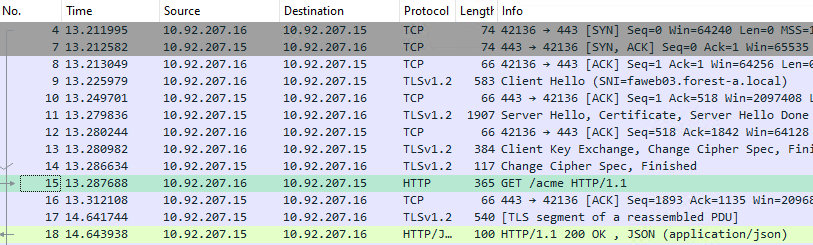
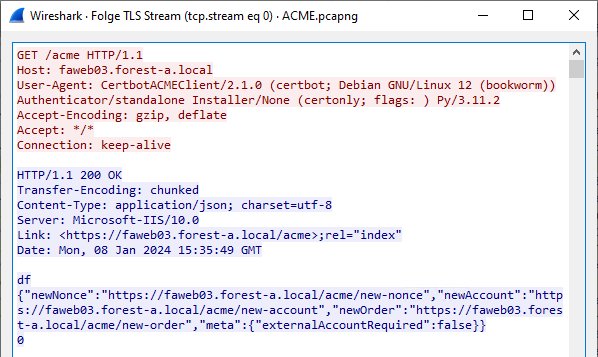
Related links:
External sources
- Decrypting SSL/TLS sessions with Wireshark - Reloaded (Microsoft)
- Transport Layer Security (TLS) (Wireshark]
- How to Decrypt SSL with Wireshark - HTTPS Decryption Guide (Comparitech)
- Browser SSL decrypted (Heise)
- NSS Key Log Format (Mozilla)
- Walkthrough: Decrypt SSL/TLS traffic (HTTPS and HTTP/2) in Wireshark (Sheng Jiang)
One thought on “TLS-Datenverkehr mit Wireshark inspizieren (HTTPS entschlüsseln)”
Comments are closed.