Assume the following scenario:
- You use certutil.exe or the PowerShell commandlet Backup-CAService to back up your Active Directory Certificate Services database.
- In addition to a full backup, you also perform regular incremental backups of the CA database.
- The incremental backups fail with error message "The database missed a previous full backup before incremental backup".
Incremental database backup for...
Backing up Log files: 0%CertUtil: -backupDB command FAILED: 0xc8000230 (ESE: -560 JET_errMissingFullBackup)
CertUtil: The database missed a previous full backup before incremental backup
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The information about when a complete backup was last performed is stored in two places:
- In the registry database of the certification authority service under HKLM:\CurrentControlSet\Services\CertSvc\Configuration\ in the value "DBLastFullBackup".
- In the header data of the certification authority database.
The easiest way to get the information from the registration of the certification authority service is to execute the following command:
certutil -getreg DBLastFullBackup
Example:
certutil -getreg DBLastFullBackup
DBLastFullBackup REG_BINARY = 12/19/2018 20:00
From the certification authority database you get the information with an esentutl command, which prints the header information:
esentutl /mh {path-to-certification-body-database}.edb
Note that the certification authority service must be stopped for this, otherwise esentutl cannot access the database and terminates with the following error:
Operation terminated with error -1032 (JET_errFileAccessDenied, Cannot access file, the file is locked or in use) after 0.16 seconds.
If the command was executed successfully, we will see the "Previous Full Backup" section.
Example:
esentutl /mh "C:\Windows\System32\CertLog\ADCSLabor Root CA.edb"
Previous Full Backup:
Log Gen: 167-189 (0xa7-0xbd) - OSSnapshot
Mark: (0xBE,1,0)
Mark: 12/19/2018 22:16:49.142
In this case, you can see that the values from the registry and the certificate authority database are different. In the "Log Gen" area you can also see that the last full backup was made by an operating system snapshot (OSSnapshot). Corresponding entries could also be found in the machine's event viewer:
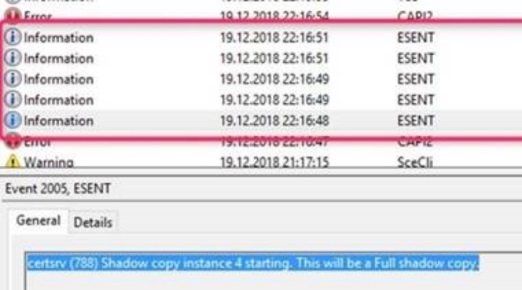
As it turned out, the certificate authority in question was installed on a virtual machine and was backed up not only by a scripted backup but also by a snapshot of the virtual machine.
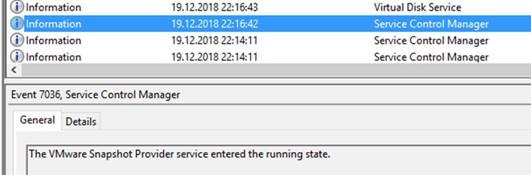
Since the CA database is informed by the operating system about volume shadow copies, this snapshot is saved as the last successful backup.
This is a function of the Extensible Storage Engine (ESE) database, but the certification authority service is not aware of it. This is why the two values now differ from each other. Certutil tries in vain to make an increment to the last scripted backup.
The solution is to align the two backup processes so that the scripted full backup of the certificate authority database always occurs after the virtual machine snapshot has already occurred, and that the incremental backups stop before the next snapshot occurs.
Typically, virtual machines are backed up one at a time, so it can never be guaranteed exactly when the CA will take its turn, so this window should be planned generously.