Starting with version 58, Google has decided to remove support for the Subject Distinguished Name of web server certificates in the Chrome browser and instead only accept certificates with Subject Alternative Name.
Since this moment, web server certificates without a subject alternative name in the form of a dNSName from Google Chrome and others Chromium-based browsers (i.e. also Microsoft Edge) was rejected. Other browser manufacturers quickly adopted this approach, so that this problem now affects all popular browsers.
The problem in the corporate environment
This behavior is fully compliant with the ITEF RFC 2818which dates back to the year 2000. Certificates for web servers must therefore use the Subject Alternative Name (SAN) in the form of a DNS name for their identity.
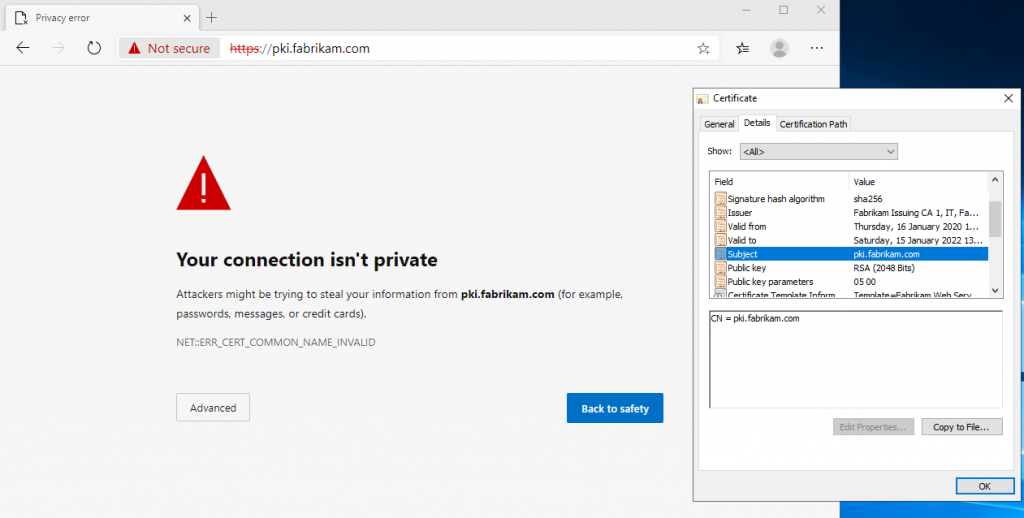
Unfortunately, there are still many products (e.g. firewalls, telephone systems, routers and other appliances) in use in companies that cannot create certificate requests with a SAN.
Workarounds are dangerous
With the supposedly good intention of making it possible to issue such certificate requirements with a SAN, guess unfortunately much at many Instructions to set the flag on the certification authority EDITF_ATTRIBUTESUBJECTALTNAME2 to activate.
However, this opens up a huge attack surface, as the certification authority accepts any SANs by the applicant for all published certificate templates - including those of malicious actors, which in the worst case can lead to a complete takeover of the Active Directory.
Workarounds are cumbersome
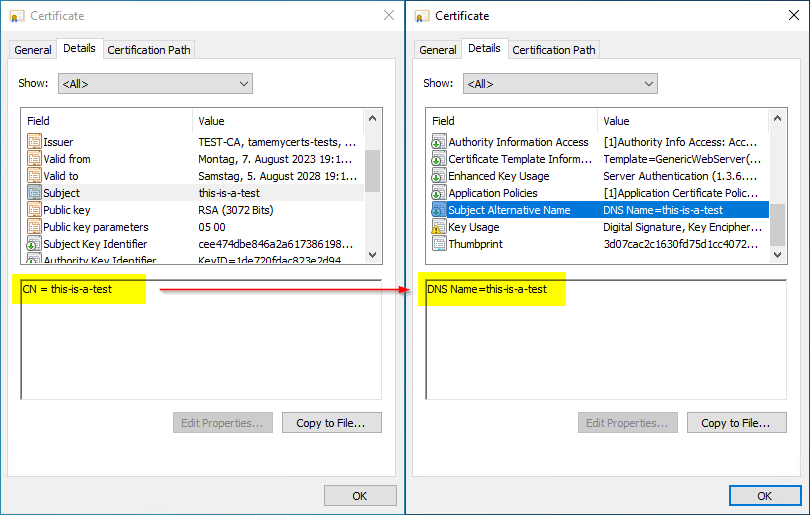
This means that a responsible PKI administrator previously only had the cumbersome, manual option, to subsequently add a SAN to a certificate request.
Fortunately, there are better ways to reach your destination.
The solution
With the TameMyCerts Policy Module for Microsoft Active Directory Certificate Services, there is now a way to securely and fully automatically correct corresponding certificate requests - without having to activate insecure settings on the certification authority.
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
TameMyCerts even recognizes whether corresponding insecure flags are set on the certification authority and rejects certificate applications that exploit the setting.
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
Related links:
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
- Change the Subject Alternative Name (SAN) of a certificate before it is issued - but do it securely!