Attacks on Microsoft certification authorities can be aimed at exploiting authorizations on certificate templates. In many cases, certificate templates must be configured to grant the applicant the right to apply for any identities. This can lead to the attacker taking over the identities of Active Directory accounts and subsequently to the elevation of rights. Attacks of this type are known in the security scene as "ESC1" is labeled.
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
ESC1 targets certificate templates that have the "Enrollee supplies subject" setting configured (also called an "offline" certificate template, as the identity in the issued certificate is determined by the requester, as opposed to the "online" certificate template, where it is formed from the Active Directory based on the requester's credentials).
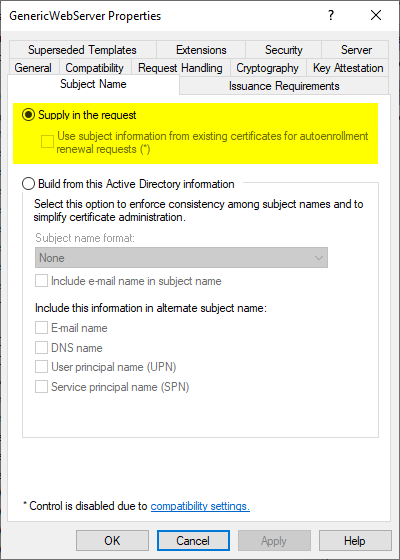
Once the attacker has located a certificate template that is configured accordingly and grants him "Enroll" authorizations, all he has to do is create a corresponding Certificate request with the desired identity to the certification authority.
TameMyCerts can either completely prevent attacks against ESC1 or drastically reduce the resulting damage:
- TameMyCerts can Enforce identity types and thus ensure that issued certificates only contain certain defined field types.
- TameMyCerts can Apply syntax rules to certificate requests and thus ensure that only certificate content that complies with the defined naming conventions is issued.
- TameMyCerts can be used in the certificate requested identities map backwards against the Active Directory and apply rules based on status, security group or organizational unit memberships and account attributes.
Without TameMyCerts, this fine-grained control over the certificate content is not possible with a Microsoft certification authority, so there is a large window for attacks, which in the worst case could allow an attacker to take over the entire Active Directory structure.
Rule violations are logged in the certification authority's event log and thus allow an alarm to be raised for rule violations.
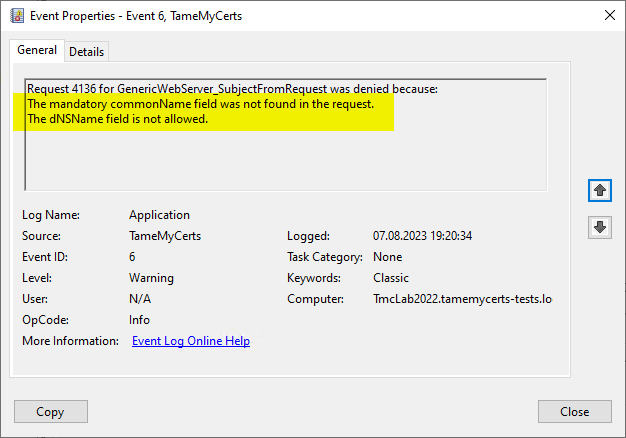
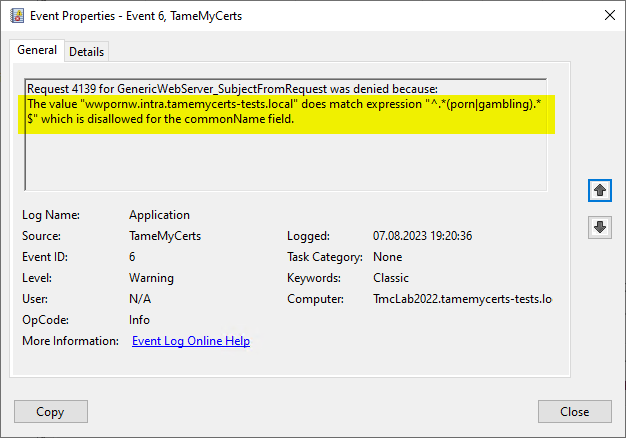
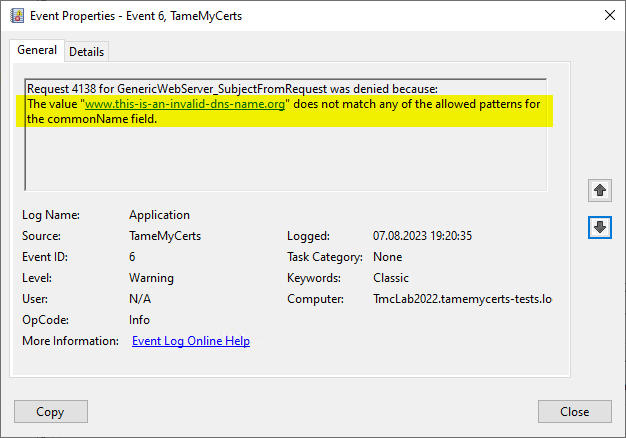
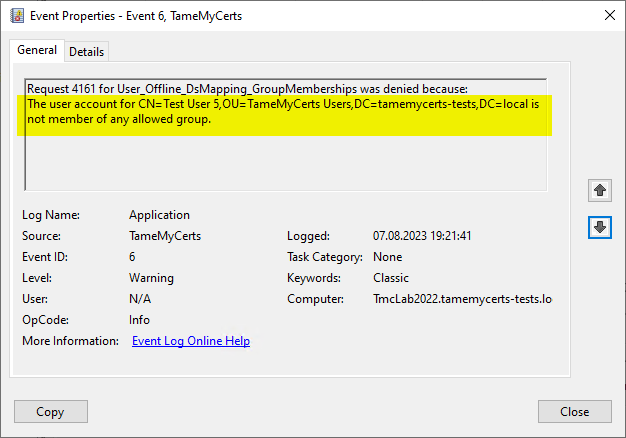
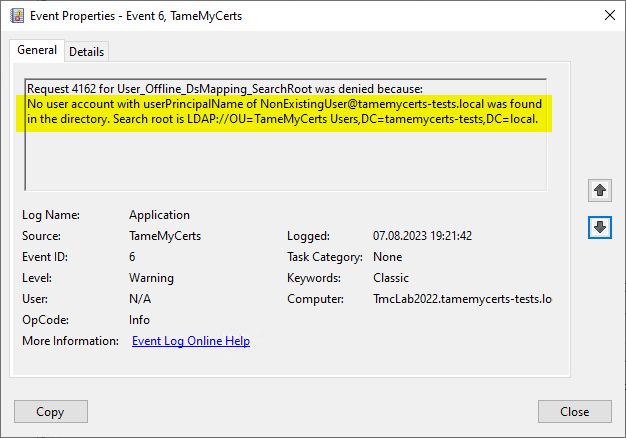
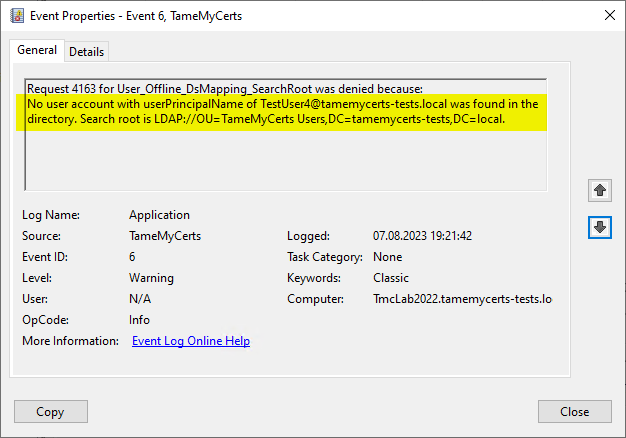
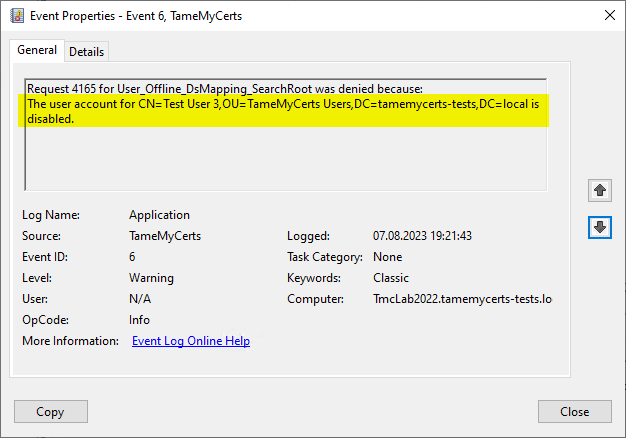
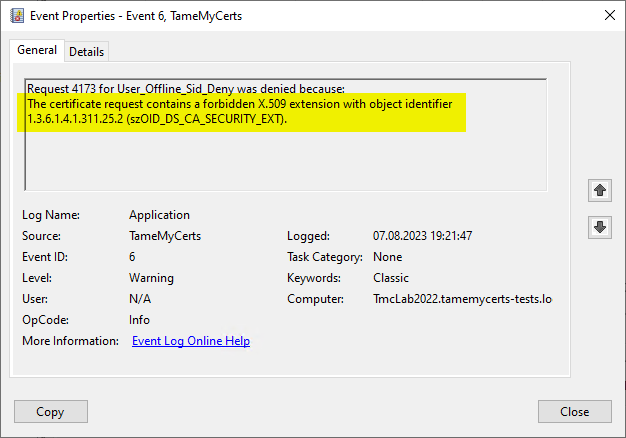
 A certificate request containing the identity of a deactivated account was rejected and logged by TameMyCerts
A certificate request containing the identity of a deactivated account was rejected and logged by TameMyCertsRelated links:
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- Attack vector on Active Directory directory service via smartcard logon mechanism