Over the generations of Windows operating systems, various certificate templates for domain controllers have been established. In a current Active Directory directory service, one will find three different templates for this purpose.
- Domain controller
- Domain Controller Authentication
- Kerberos Authentication
Below is a description of each template and a recommendation for configuring domain controller certificate templates.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Domain controller
The Domain Controller certificate template was introduced with Windows 2000 Server.
This is a version 1 certificate template due to Windows 2000 roots, which means it cannot be edited.
The certificate template includes the following Extended Key Usage (EKU):
- Server Authentication
- Client Authentication
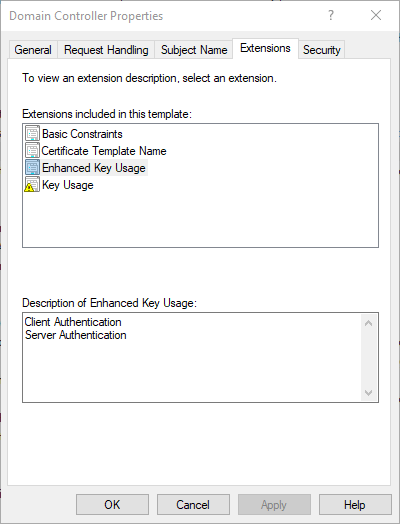
If this certificate template is published, domain controllers will in any case (even if AutoEnrollment is not enabled) request a certificate from this template. This is a legacy from Windows 2000 times, as there was no AutoEnrollment in the first generation of certificate templates.
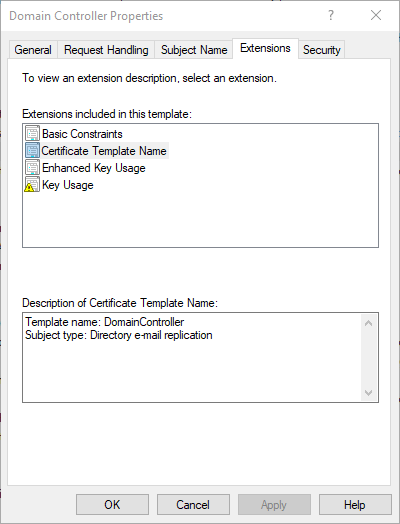
The domain controllers use the "Certificate Template Name" extension to recognize that the certificate can be used for smart card logon, and thus then also accept smart card logons. This is also a legacy from Windows 2000 times, since the Extended Key Usage "Smart Card Logon" was not defined at that time.
Domain Controller Authentication
The Domain Controller Authentication certificate template was introduced with Windows Server 2003.
This is a version 2 template, which were introduced with Windows Server 2003. These certificate templates can be edited.
Another significant innovation was the introduction of the "Smart Card Logon" Extended Key Usage. Previously, the smart card logon was mapped via the Extended Key Usage "Client Authentication" (on the user side) and "Server Authentication" (on the server side).
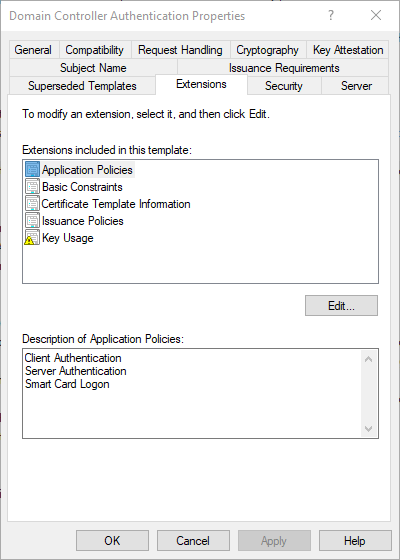
The certificate template includes the following Extended Key Usage (EKU):
- Server Authentication
- Client Authentication
- Smart Card Logon
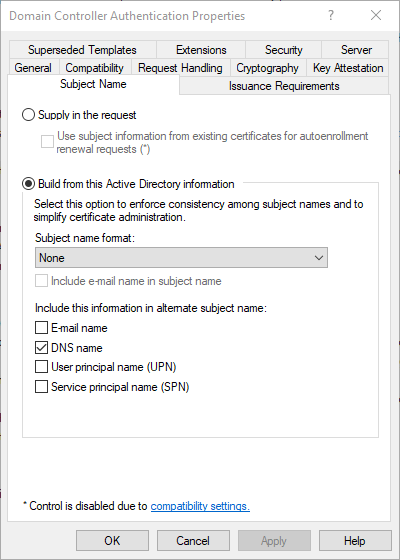
Since the template already includes the RFC 2818 the identity of the requester (the domain controller) is already formed via the Subject Alternative Name. The subject field is not filled according to RFC.
The "Certificate Template Name" extension is no longer present in version 2 certificate templates and newer - but it is also no longer necessary. The identification of the certificate template can be done using the "Certificate Template Information" extension. Smart card logon is activated by the presence of the "Smart Card Logon" Extended Key Usage. The application must be controlled via AutoEnrollment.
Kerberos Authentication
The Kerberos Authentication certificate template was introduced with Windows Server 2008.
A significant innovation is the "Kerberos Authentication" Extended Key Usage, which Strict KDC Validation is enabled. However, this function must be explicitly activated. Furthermore, a separation between the user-side ("Smart Card Logon" EKU) and server-side ("Kerberos Authentication" EKU) part for the smart card logon can be made.
The template includes the following Extended Key Usage (EKU):
- Server Authentication
- Client Authentication
- Smart Card Logon
- KDC Authentication
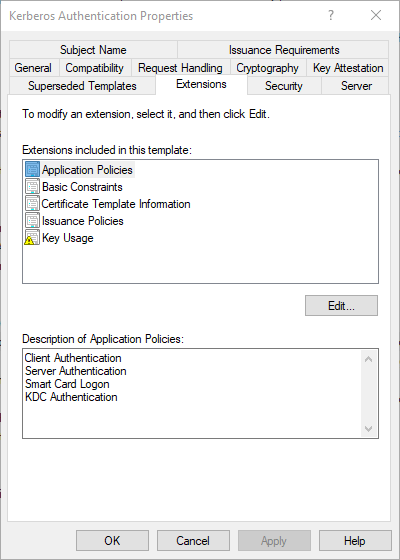
Furthermore, this certificate template introduced the CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS flag, which ensures that the fully qualified domain name and the NETBIOS name of the domain are entered into the Subject Alternative Name (SAN) extension of the domain controller certificate.
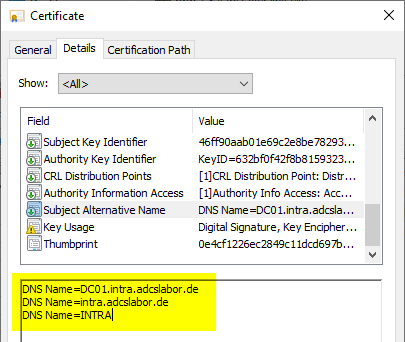
Which certificate template should I use?
Basically, a custom template should be created that originates from the Kerberos Authentication certificate template. Only this contains the CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS flag, which ensures that the fully qualified domain name and the NETBIOS name of the domain are entered in the Subject Alternative Name (SAN) extension of the domain controller certificate.
This should be adjusted as follows:
- If no smart card logon is used in the company, the function can be disabled by removing the extended key usages "Smart Card Logon" as well as "KDC Authentication". Domain controllers can then continue to offer LDAP via SSL connections, but cannot accept smart card logons.
- For better compatibility, it is recommended that the Subject field in the Subject Name tab be populated with the Common Name attribute. Some applications (for example Microsoft Network Policy Service, NPS) cannot determine the identity in the certificate based on the Subject Alternative Name extension in the certificate, but require a Subject. Applications that can evaluate Subject Alternative Names should also prefer to use this and ignore the Subject, so that the Subject can be filled without risk.
Related links:
- Domain Controller Certificate Templates and Smartcard Logon
- Certificates for domain controllers do not contain the domain name in the Subject Alternative Name (SAN)
External sources
- Enabling Strict KDC Validation in Windows Kerberos (Microsoft)
- RFC 2818 - HTTP Over TLS (Internet Engineering Task Force)
9 thoughts on “Übersicht über die verschiedenen Generationen von Domänencontroller-Zertifikaten”
Comments are closed.