In order for domain controllers to process smart card logins, they need certificates that provide this function.
One of the following conditions must be met by the Domain controller certificate must be fulfilled for it to be usable for smartcard registration:
- The string "DomainController" in the certificate template name extension (This extension is only available in certificate templates version 1).
- The smartcard logon (1.3.6.1.4.1.311.20.2.2) OID in the Extended Key Usages extension.
- The KDC Authentication (1.3.6.1.5.2.3.5) OID in the Extended Key Usages extension.
Microsoft uses the term "Enhanced Key Usage", the correct name according to RFC 5280 is "Extended Key Usage"..
The extension "certificate template name" is included only in version 1 certificate templates from Windows 2000 times. The only certificate template that has this extension filled with the string "DomainController" is the version 1 template with the same name. These certificate templates do not yet support AutoEnrollment, so until today's Windows Server 2019, there is code in the KDC that ensures that these certificates are requested by domain controllers if there is a certificate authority on the network that offers them.
The Extended Key Usage "Smartcard Logon" was introduced with the "Domain Controller Authentication" certificate template with Windows Server 2003. It was used both on client side (user certificate) and on server side (domain controller certificate).
The Extended Key Usage "KDC Authentication" was introduced with the "Kerberos Authentication" certificate template with Windows Server 2008. It allowed a separation between the server part (KDC Authentication in the domain controller certificate) and the client part (Smartcard Logon in the user certificate).
Below are some examples of how the KDC process behaves in conjunction with the different certificate types.
Default Domain Controller Certificate Template
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This certificate template is characterized by the fact that the resulting certificate contains the following Extended Key Usages:
- Server Authentication
- Client Authentication
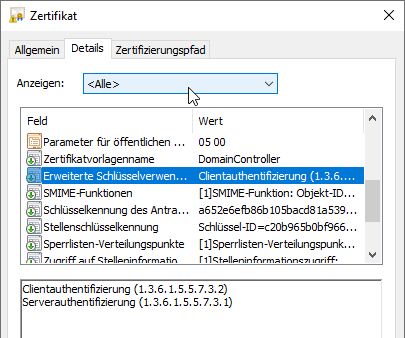
In addition, since it is a schema version 1 certificate template, it also includes a "Certificate Template Name" extension which includes the value "DomainController".
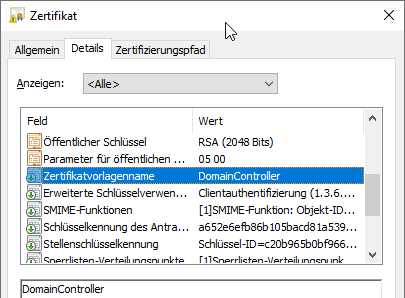
Smartcard enrollment works with this certificate, but it will use the Event no. 32 is logged in the event viewer of the domain controller, which indicates that the certificate does not include the "KDC Authentication" Extended Key Usage and thus compatibility problems may occur.
Default Domain Controller Authentication Certificate Template
This certificate template is characterized by the fact that the resulting certificate contains the following Extended Key Usages:
- Server Authentication
- Client Authentication
- Smartcard Logon
Since this is a schema version 2 certificate template, there is no "certificate template name" extension included.
Smartcard enrollment works with this certificate, but it will use the Event no. 32 is logged in the event viewer of the domain controller, which indicates that the certificate does not include the "KDC Authentication" Extended Key Usage and thus compatibility problems may occur.

Standard certificate template "Kerberos Authentication
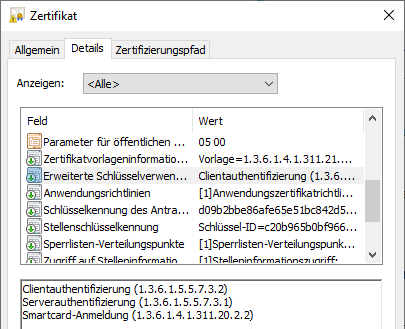
This certificate template is characterized by the fact that the resulting certificate contains the following Extended Key Usages:
- Server Authentication
- Client Authentication
- Smartcard Logon
- KDC Authentication
Since this is a schema version 2 certificate template, there is no "certificate template name" extension included.
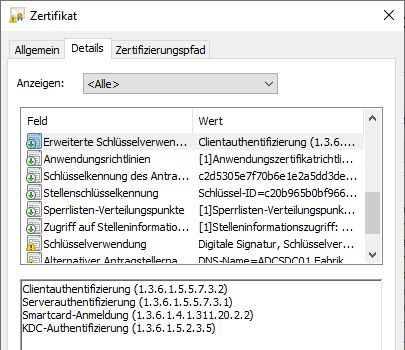
Smartcard enrollment works with this certificate, and no warnings are logged in the domain controller event viewer.
Customized certificate template based on "Kerberos Authentication", but without the Smartcard Logon Extended Key Usage
This certificate template is characterized by the fact that the resulting certificate contains the following Extended Key Usages:
- Server Authentication
- Client Authentication
- KDC Authentication
Since this is a schema version 2 certificate template, there is no "certificate template name" extension included.
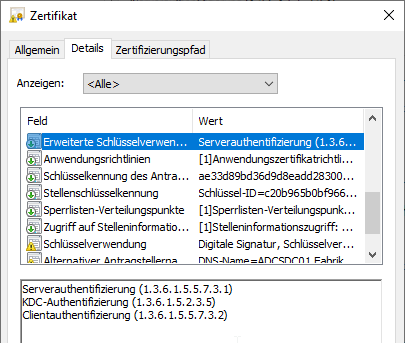
Smartcard logon works with this certificate, and no warnings are logged in the event display of the domain controller. This certificate template thus meets all the minimum requirements for error-free processing of smartcard logons.
Customized Certificate Template Based on Domain Controller
This certificate template is characterized by the fact that the resulting certificate contains the following Extended Key Usages:
- Server Authentication
- Client Authentication
Unlike the original certificate template, however, it does not include a "certificate template name" extension, since it is a schema version 2 certificate template that is identified by OID rather than name.
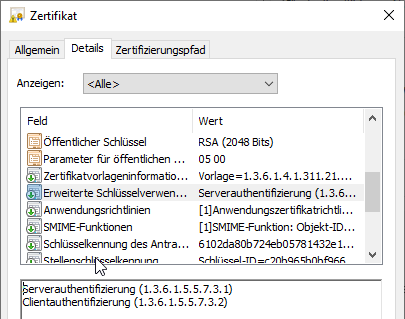
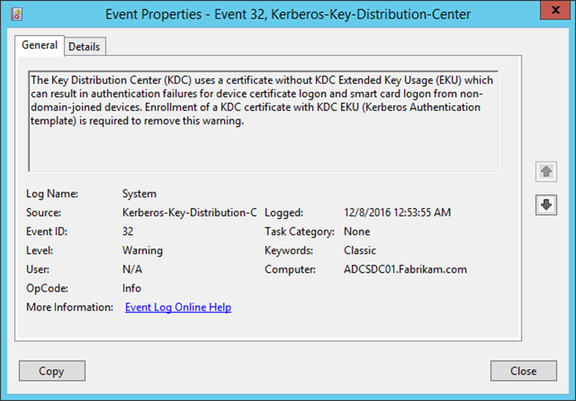
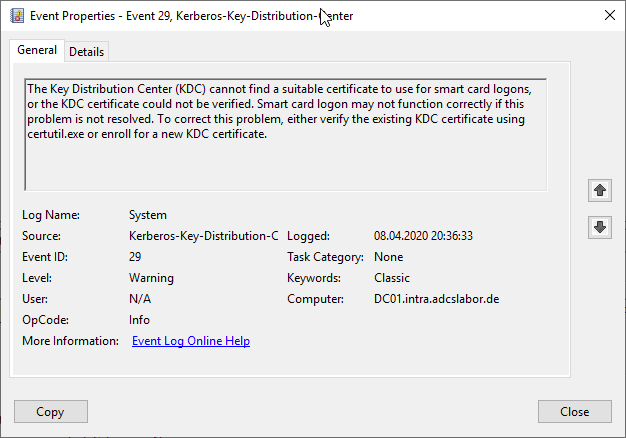
This certificate template cannot be used by the KDC for Smartcard Logon. The events no. 19 and 29 logged in the domain controller event log when a user tries to log in by smart card:
This event indicates an attempt was made to use smartcard logon, but the KDC is unable to use the PKINIT protocol because it is missing a suitable certificate.
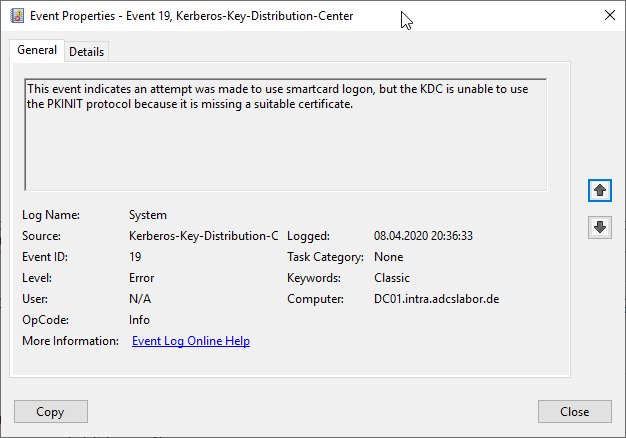
The Key Distribution Center (KDC) cannot find a suitable certificate to use for smart card logons, or the KDC certificate could not be verified. Smart card logon may not function correctly if this problem is not resolved. To correct this problem, either verify the existing KDC certificate using certutil.exe or enroll for a new KDC certificate.
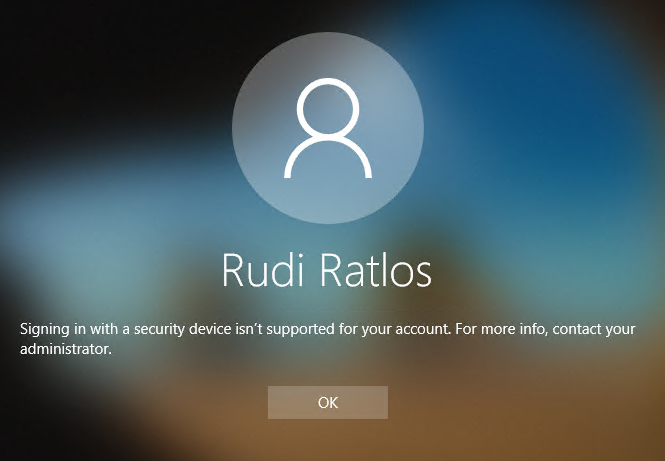
For a user logging in, the error manifests itself with the error message: "Signing in with a security device isn't supported for your account. For more info, contact your administrator.„
So which certificate template should be used for domain controllers?
Basically, a custom template should be created from the Kerberos Authentication certificate template.
Although not directly relevant to smartcard enrollment, only the "Kerberos Authentication" certificate template includes the CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS flag, which ensures that the fully qualified domain name and NETBIOS name of the domain are entered into the Subject Alternative Name (SAN) extension of the domain controller certificate.
The following changes can be made.
- If you want to prevent the domain controllers from accepting smartcard logons, this can be achieved by removing the two extended key usages for "Smartcard Logon" and "KDC Authentication".
- Also, if the domain controllers are to process smartcard logons, the "Smartcard Logon" Extended Key Usage can be removed, since the server-side part of the smartcard logon is mapped by the "KDC Authentication" Extended Key Usage.
Related links:
- Overview of the different generations of domain controller certificates
- What requirements must be met on the infrastructure side for smartcard logins to be possible?
- Signing in via smart card fails with error message "Signing in with a security device isn't supported for your account."
- Certificates for domain controllers do not contain the domain name in the Subject Alternative Name (SAN)
19 thoughts on “Domänencontroller-Zertifikatvorlagen und Smartcard Anmeldung”
Comments are closed.