Here's the scenario:
- A user applies for a certificate from an Active Directory integrated certification authority (Enterprise Certification Authority).
- The certificate of the certification authority is trusted, i.e. it is located in the Trusted Root Certification Authorities store.
- The certificate request fails with the following error message:
A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)
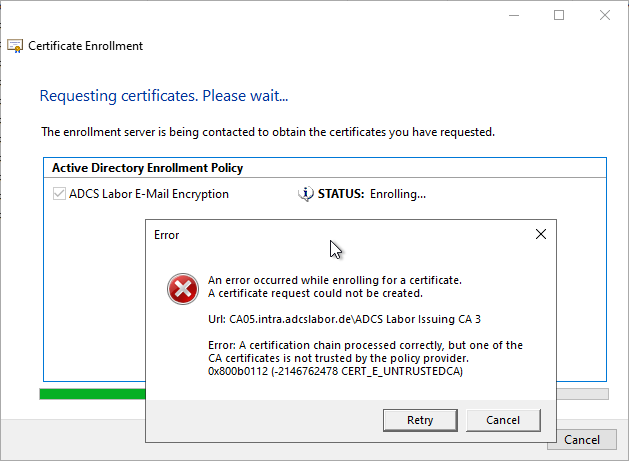
The Certification Authority will use the Event with no. 22 log.
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
In this case, an attempt was made to archive private keys. For this purpose, a key recovery agent (KRA) was configured on the certification authority. However, the certification authority that issued the certificate of the key recovery agent was deleted from the NTAuthCertificates Object removed.
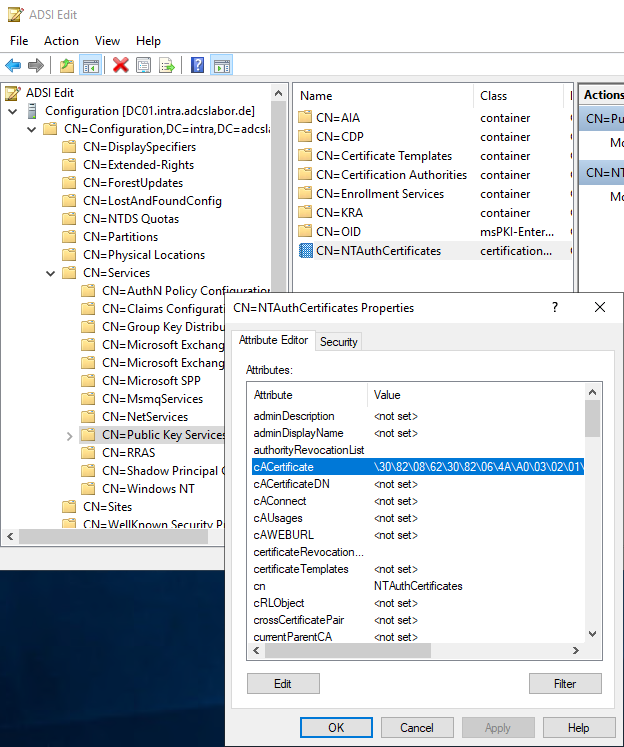
The NTAuthCertificates object is located below the Public Key Services container within the configuration partition of the Active Directory forest. It contains all the certificate authority certificates that can be used for certificate-based logon in the Windows ecosystem.
The full LDAP path is:
CN=NTAuthCertificates,CN=Public Key Services,CN=Services,CN=Configuration,{Forest-Root-Domain}
The following certificate-based functions require the presence of the CA certificate in NTAuthCertificates object:
| Function | Description |
|---|---|
| Enroll on Behalf Of (EOBO) | The CA certificate of the certification authority that issues the certificates for the enrollment agents must be located in NTAuthCertificates. |
| Key Recovery / Private Key Archiving | The CA certificate of the certification authority that archives the keys must be located in NTAuthCertificates. |
| Smartcard Logon | The CA certificate of the certification authority that issues the certificates of the domain controllers and logon users must be located in NTAuthCertificates. |
| Windows Hello for Business | Identical to Smartcard Logon. If Windows Hello for Business is used without certificates, only the certification authority for domain controllers must be entered. |
| Network Policy Server (Network Policy Server, NPS) when certificate-based logins are processed (e.g. 802.1x over wireless or wired network, DirectAccess, Always ON VPN). | The CA certificate of the certification authority that issues the certificates of the logging in users or computers must be located in NTAuthCertificates. |
| EFS File Recovery Agents | The CA certificate of the certification authority that issues the certificates of the file recovery agents must be located in NTAuthCertificates. |
| IIS Client Certificate Mapping (against Active Directory) | The CA certificate of the certification authority that issues the certificates of the logging in users must be located in NTAuthCertificates. |
| Network Device Enrollment Service (Network Device Enrollment Service, NDES), Renewal mode only | Only affects renewal mode, i.e. signing a certificate request with an existing certificate. The CA certificate of the certification authority that issued the certificates of the certificates to be renewed must be located in NTAuthCertificates. |
If an Active Directory integrated certificate authority (Enterprise CA) is newly installed, its CA certificate is automatically copied to the NTAuthCertificates object by the installation routine. In the present case, the CA certificate was subsequently removed from the object.
The object can be inspected with the ADSI Editor (adsiedit.msc), for example, but the CA certificates cannot be viewed directly here because they are stored as a byte array.
However, one can check which certificates are in NTAuthCertificates with the following command line command, for example:
certutil -enterprise -verifystore NTAuth
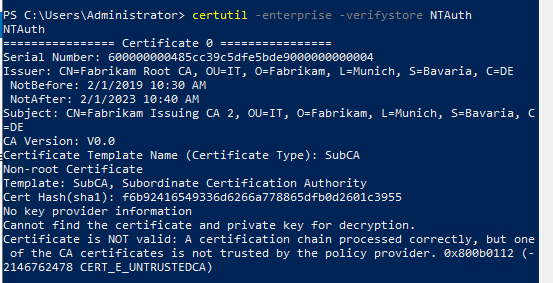
In the image above, you can see that a CERT_E_UNTRUSTEDCA message also appears here, although a certification authority certificate is present. This seems normal, here you should not be irritated by the message.
Likewise, a check is possible with the Enterprise PKI Management Console (pkiview.msc), which is installed together with the Certificate Authority Management tools. Within the tree view on the left, right-click on the top node and select Manage AD Containers...
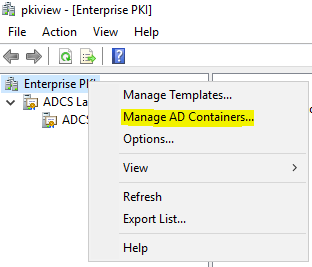
Then the list of certificates can be found in the NTAuthCertificates tab.
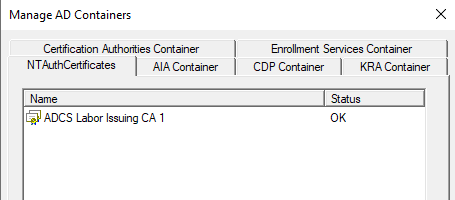
Import CA certificate into the NTAuthCertificates object
If it turns out that the certification authority certificate is not included in NTAuthCertificates, you can add it in the same dialog.
For security reasons, it may well be advisable for a certificate authority certificate not to be in the NTAuthCertificates object. Added CA certificates are considered trusted by all previously listed functions. This can be a security risk, assuming the CA is taken over by an attacker. Before adding new CA certificates to the NTAuthCertificates object, a security assessment should take place. Usually there is a reason that the CA certificate on NTAuthCertificates was removed.
Likewise, it is possible to add a certificate authority certificate with the following command line command.
certutil -dspublish {filename} NTAuthCA
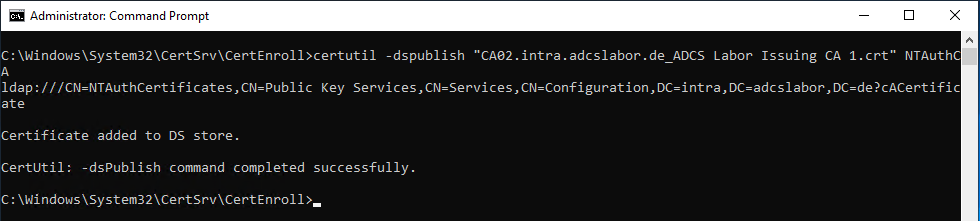
NTAuthCertificate object is not queried "live"
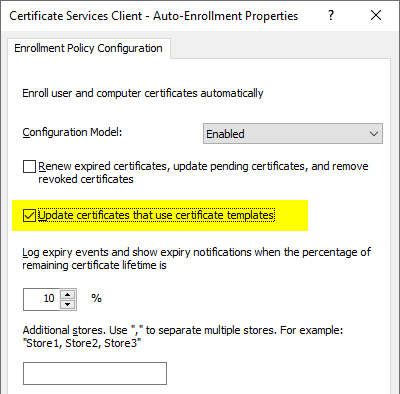
Please note that the information about the content of the NTAuthCertificates object is not evaluated live, but a local replica is created.
For this to happen, at least the "AUTO_ENROLLMENT_ENABLE_TEMPLATE_CHECK" flag must be activated. In the corresponding group policy known as "Update certificates that use certificate templates".
Related links:
- Smartcard login fails with error message "A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)"
- Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM (MS-WCCE)
- Editing the NTAuthCertificates object in Active Directory
- Basics of manual and automatic certificate requests via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM) with the MS-WCCE protocol
3 thoughts on “Die Beantragung eines Zertifikats schlägt fehl mit der Fehlermeldung „A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)“”
Comments are closed.