| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 93 (0x5D) |
| Event log: | Application |
| Event type: | Warning |
| Symbolic Name: | MSG_CA_CERT_NO_IN_AUTH |
| Event text (English): | The certificate (#%1) of Active Directory Certificate Services %2 does not exist in the certificate store at CN=NTAuthCertificates,CN=Public Key Services,CN=Services in the Active Directory's configuration container. The directory replication may not be completed. |
| Event text (German): | The certificate (#%1) of Active Directory Certificate Services %2 does not exist in the certificate store under "CN=NTAuthCertificates,CN=Public Key Services,CN=Services" in the Active Directory configuration container. Directory replication may not have been completed. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CACertIdentifier (win:UnicodeString)
- %2: CACommonName (win:UnicodeString)
Example events
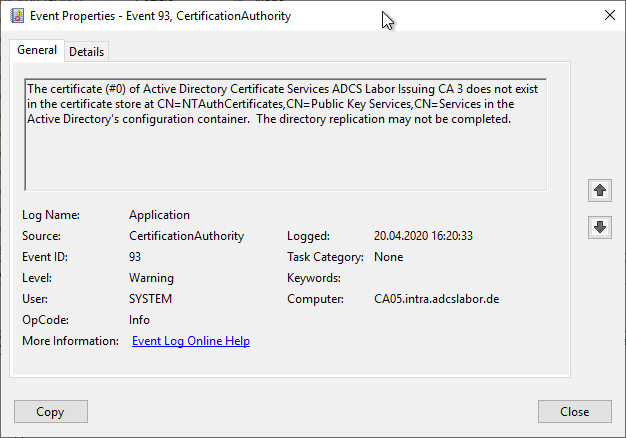
The certificate (#0) of Active Directory Certificate Services ADCS Labor Issuing CA 3 does not exist in the certificate store at CN=NTAuthCertificates,CN=Public Key Services,CN=Services in the Active Directory's configuration container. The directory replication may not be completed.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The certification authority detects that its certification authority certificate is not registered in the NTAuthCertificates object of the Active Directory forest.
The following functions require the certificate authority certificate in the NTAuthCertificates object in the Active Directory forest to process certificates from the relevant certificate authority:
| Function | Description |
|---|---|
| Enroll on Behalf Of (EOBO) | The CA certificate of the certification authority that issues the certificates for the enrollment agents must be located in NTAuthCertificates. |
| Key Recovery / Private Key Archiving | The CA certificate of the certification authority that archives the keys must be located in NTAuthCertificates. |
| Smartcard Logon | The CA certificate of the certification authority that issues the certificates of the domain controllers and logon users must be located in NTAuthCertificates. |
| Windows Hello for Business | Identical to Smartcard Logon. If Windows Hello for Business is used without certificates, only the certification authority for domain controllers must be entered. |
| Network Policy Server (Network Policy Server, NPS) when certificate-based logins are processed (e.g. 802.1x over wireless or wired network, DirectAccess, Always ON VPN). | The CA certificate of the certification authority that issues the certificates of the logging in users or computers must be located in NTAuthCertificates. |
| EFS File Recovery Agents | The CA certificate of the certification authority that issues the certificates of the file recovery agents must be located in NTAuthCertificates. |
| IIS Client Certificate Mapping (against Active Directory) | The CA certificate of the certification authority that issues the certificates of the logging in users must be located in NTAuthCertificates. |
| Network Device Enrollment Service (Network Device Enrollment Service, NDES), Renewal mode only | Only affects renewal mode, i.e. signing a certificate request with an existing certificate. The CA certificate of the certification authority that issued the certificates of the certificates to be renewed must be located in NTAuthCertificates. |
It is entirely possible, and in many cases reasonable, that the certificate authority certificate was intentionally removed from the NTAuthCertificates object (e.g., as part of a security hardening measure). See article "Editing the NTAuthCertificates object in Active Directory„.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If this event occurs, there is usually no breach of confidentiality, but the availability of services dependent on the PKI may be affected.
If one of the previously listed services is used with certificates from the certification authority in question, the service would no longer function. In this case, the event would be considered critical.
If none of the previously listed services are used with certificates from the relevant certification authority, the event can be safely ignored.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
One thought on “Details zum Ereignis mit ID 93 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.