| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 66 (0x42) |
| Event log: | Application |
| Event type: | Error |
| Symbolic Name: | MSG_E_DELTA_CRL_PUBLICATION |
| Event text (English): | Active Directory Certificate Services could not publish a Delta CRL for key %1 to the following location: %2. %3.%5%6 |
| Event text (German): | Failed to publish delta certificate revocation list for key %1 at the following location: %2. %3.%5%6 |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CAKeyIdentifier (win:UnicodeString)
- %2: URL (win:UnicodeString)
- %3: ErrorMessageText (win:UnicodeString)
- %4: param4 (win:UnicodeString)
- %5: param5 (win:UnicodeString)
- %6: AdditionalErrorMessage (win:UnicodeString)
Example events
Active Directory Certificate Services could not publish a Delta CRL for key 0 to the following location: ldap:///CN=ADCS Labor Enterprise Root CA,CN=ERCA01,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=de. Operation aborted 0x80004004 (-2147467260 E_ABORT).
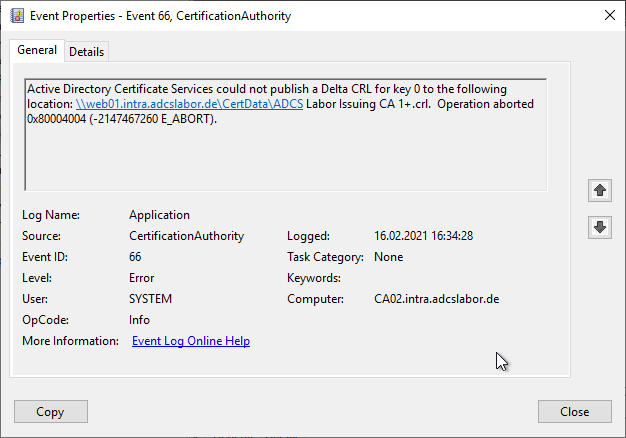
Active Directory Certificate Services could not publish a Delta CRL for key 0 to the following location: file://\web01-intra.adcslabor.de/CertData/ADCS Labor Issuing CA 1+.crl. The user name or password is incorrect. 0x8007052e (WIN32: 1326 ERROR_LOGON_FAILURE).
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs if the certificate revocation list was successfully generated but could not be copied to one of the configured revocation list distribution points. It usually occurs together with the events 65, 74 and 75 on.
This may be due to
- The server on which the revocation list distribution point is set up is unreachable. In the case of an LDAP revocation list distribution point, it may not be possible to contact the domain. See Events 44, 91 and 94.
- The certification authority does not have permissions to the share or LDAP path that has been set up. By default, the server on which the certification authority is installed is a member of the "Cert Publishers" group. Since the group membership is only applied when the account (in the case of the certification authority: SYSTEM) is logged in again, the server on which the certification authority is installed must be restarted once after installation.
- The configured blacklist distribution point contains invalid characters, such as quotation marks (").
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If the certification authority is not able to generate or publish a revocation list, it is highly likely that it will expire on the distribution points in a short time. In this case, there is a threat of failure of the IT services that depend on the PKI. Therefore, this event must be rated as "critical" in terms of availability.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
2 thoughts on “Details zum Ereignis mit ID 66 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.