| Event Source: | Microsoft-Windows-CertificateServicesClient-CertEnroll |
| Event ID: | 47 (0x825A002F) |
| Event log: | Application |
| Event type: | Warning |
| Event text (English): | Certificate enrollment for %1 could not enroll for a %2 certificate. A valid certification authority cannot be found to issue this template. |
| Event text (German): | No registration of certificate %2 could be made from the certificate registration for %1. No valid certification authority can be found to issue this template. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: Context (win:UnicodeString)
- %2: TemplateName (win:UnicodeString)
Example events
Certificate enrollment for INTRA\rudi could not enroll for an ADCSLaborBenutzer3 certificate. A valid certification authority cannot be found to issue this template.
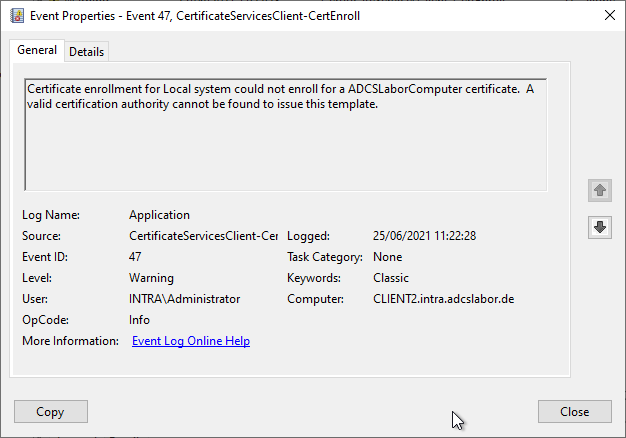
Certificate enrollment for Local system could not enroll for a DomainController certificate. A valid certification authority cannot be found to issue this template.
Certificate enrollment for Local system could not enroll for an ADCSLaborComputer certificate. A valid certification authority cannot be found to issue this template.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Occurs when a certificate request is attempted specifying a certificate template, but no certification authority on the network offers the specified certificate template for issuance.
Also occurs when a certification authority offers the corresponding template, but the requesting client cannot establish a trust status with it. In this case, the Event no. 52 logged.
Automatic certificate request
Domain controllers automatically try to request certificates from the DomainController certificate template. The process will fail if this certificate template is not offered on the network. Thus, it can be ignored because this certificate template should not be used.
See also the following articles:
- Overview of the different generations of domain controller certificates
- Domain Controller Certificate Templates and Smartcard Logon
Manual certificate request
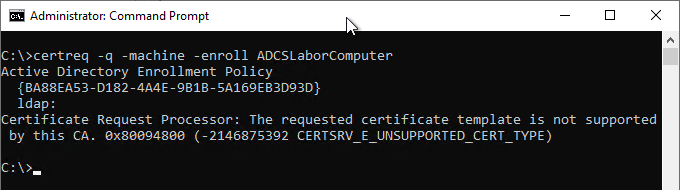
The event can also occur with manual certificate request. Example command for such a type of certificate request:
certreq -q -machine -enroll ADCSLaborComputer
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
No description has been written for this yet.
One thought on “Details zum Ereignis mit ID 47 der Quelle Microsoft-Windows-CertificateServicesClient-CertEnroll”
Comments are closed.