| Event Source: | Microsoft-Windows-OnlineResponder |
| Event ID: | 34 (0x22) |
| Event log: | Application |
| Event type: | Error |
| Symbolic Name: | MSG_E_CACONFIG_SUBMIT_ENROLLMENT_REQUEST_FAILED |
| Event text (English): | The Online Responder Service encountered an error while submitting the enrollment request for configuration %1 to certification authority %2. The request ID is %3.(%4) |
| Event text (German): | An error occurred in the online responder service while submitting registration requests for configuration %1 to certification authority %2. Request ID: %3.(%4) |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CAConfigurationId (win:UnicodeString)
- %2: CAConfig (win:UnicodeString)
- %3: RequestId (win:UnicodeString)
- %4: ErrorCode (win:UnicodeString)
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
Example events
The Online Responder Service encountered an error while submitting the enrollment request for configuration ADCS Labor Issuing CA 2 (0) to certification authority CA03.intra.adcslabor.de\ADCS Labor Issuing CA 2. The request ID is -1.(The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE))
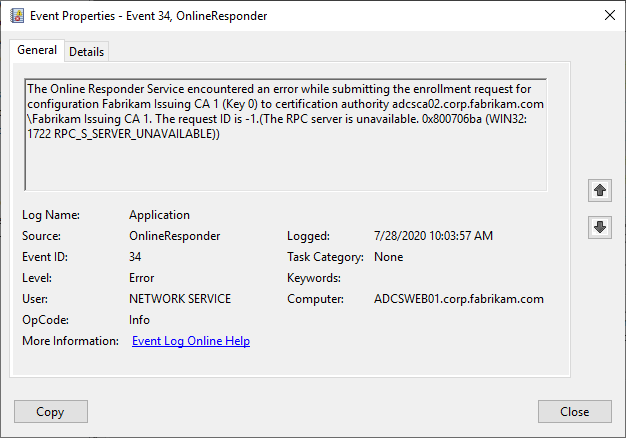
The Online Responder Service encountered an error while submitting the enrollment request for configuration ADCS Labor Issuing CA 1 (Key 0) to certification authority CA02.intra.adcslabor.de\ADCS Labor Issuing CA 1. The request ID is 165.(The permissions on the certificate template do not allow the current user to enroll for this type of certificate. 0x80094012 (-2146877422 CERTSRV_E_TEMPLATE_DENIED))
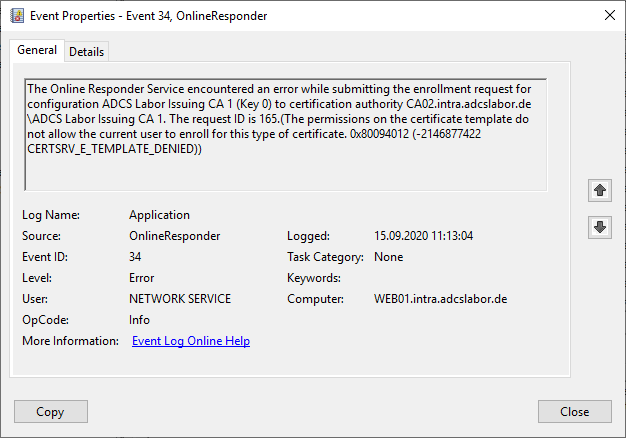
The Online Responder Service encountered an error while submitting the enrollment request for configuration ADCS Labor Issuing CA 2 (0) to certification authority CA03.intra.adcslabor.de\ADCS Labor Issuing CA 2. The request ID is 95.(The encryption type requested is not supported by the KDC. 0x80090342 (-2146892990 SEC_E_KDC_UNKNOWN_ETYPE))
The Online Responder Service encountered an error while submitting the enrollment request for configuration ADCS Labor Issuing CA 2 (0) to certification authority CA03.intra.adcslabor.de\ADCS Labor Issuing CA 2. The request ID is -1.(The directory service encountered an internal failure. 0x800720ee (WIN32: 8430 ERROR_DS_INTERNAL_FAILURE))
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs when the online responder is unable to request a new signing certificate for an online configuration. As a result, the signature certificate currently in use will expire in the foreseeable future and cause the revocation configuration to fail. See also article "Effects of the failure of the online responder (OCSP) on the verification of the revocation status of a certificate„.
The encryption type requested is not supported by the KDC. 0x80090342 (-2146892990 SEC_E_KDC_UNKNOWN_ETYPE)
Means, mutatis mutandis, that no Kerberos authentication is possible at the certificate authority because the encryption algorithm used is not known.
Can be used by the Patch from November 2022 can be triggered. This changed the standard encryption algorithms for domain controllers and forgot to include the Advanced Encryption Standard (AES), making Kerberos authentication no longer possible in hardened environments.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If no new signature certificate can be applied for before the one currently in use expires, the revocation configuration will fail. This endangers the availability of the service.
Related links:
- Overview of Windows events generated by the online responder (OCSP)
- Overview of the audit events generated by the online responder (OCSP)
External sources
- KB5021131: How to manage the Kerberos protocol changes related to CVE-2022-37966 (Microsoft Corporation)
- Decrypting the Selection of Supported Kerberos Encryption Types (Microsoft Corporation)
- Installing, Configuring, and Troubleshooting the Online Responder (Microsoft's OCSP Responder) (archive link)
2 thoughts on “Details zum Ereignis mit ID 34 der Quelle Microsoft-Windows-OnlineResponder”
Comments are closed.