| Event Source: | Microsoft Windows Kerberos Key Distribution Center |
| Event ID: | 21 (0x80000015) |
| Event log: | System |
| Event type: | Warning |
| Event text (English): | The client certificate for the user %1\%2 is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : %3 |
| Event text (German): | The client certificate for user %1\%2 is not valid. The result was an error during smartcard login. Contact the user for more information about the certificate to be used for the smartcard application. Chain status: %3 |
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: Domain (win:UnicodeString)
- %2: Username (win:UnicodeString)
- %3: Status (win:UnicodeString)
- %4: __binLength (win:UInt32)
- %5: binary (win:Binary)
Example events
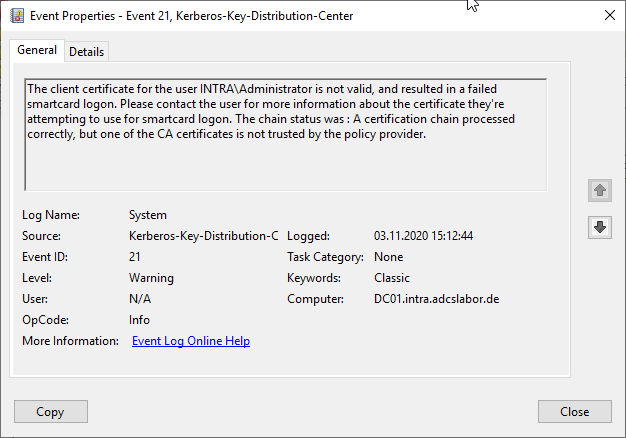
The client certificate for the user INTRA\Administrator is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : The revocation function was unable to check revocation because the revocation server was offline.
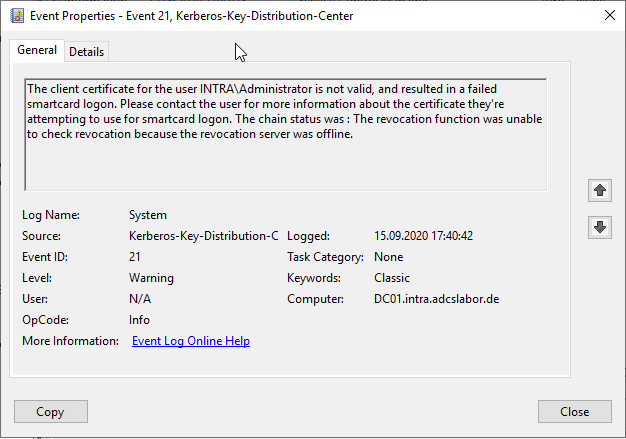
The client certificate for the user INTRA\Administrator is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : The operation completed successfully.
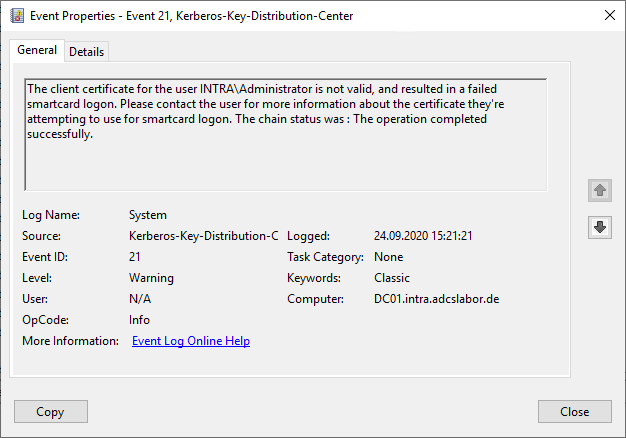
The client certificate for the user INTRA\Administrator is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : The certificate is not valid for the requested usage.
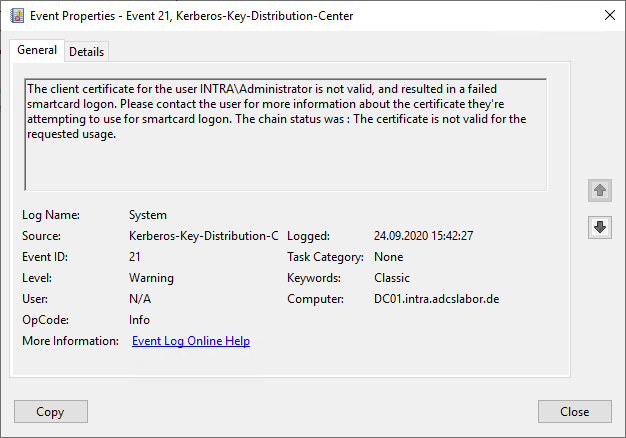
The client certificate for the user INTRA\Administrator is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider.
Description
The revocation function was unable to check revocation because the revocation server was offline.
Occurs when there are problems with the lock infrastructure.
Also occurs when Domain controllers are hard-configured to use OCSP, the online responders (OCSP) are configured for a deterministic good and the returned status is "Unknown".
In this case, both events should be correlated.
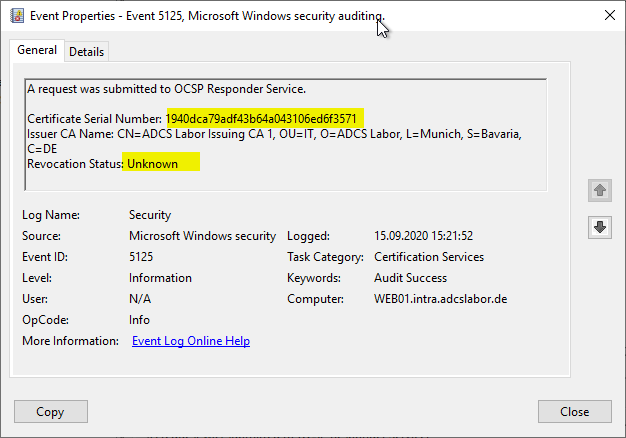
See also article "Details of the event with ID 5125 of the source Microsoft-Windows-Security-Auditing„.
The operation completed successfully.
Occurs when a PKINIT is attempted but the name in the Subject Alternative Name (SAN) does not match for the requested user (KDC_ERR_CLIENT_NAME_MISMATCH).
The certificate is not valid for the requested usage.
Occurs when a PKINIT is attempted with a certificate that does not have the extended key usage (Extended Key Usage) for "Client Authentication" nor for "Smartcard Logon".
A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider.
Occurs when a smartcard enrollment is performed with a certificate from a certification authority that is not listed in the NTAuthCertificates object is registered in the Active Directory.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If the event occurs due to incorrect locking information, the availability is affected and the event is rated as critical.
If the event occurs due to an "Unknown" status returned by the online responder, this may indicate the use of a compromised certificate. In this case, too, the event must be rated as "critical".
The same applies in the event that a logon is attempted with a certificate whose issuing certificate authority is not located in the NTAuthCertificates object in Active Directory.
Related links:
- Overview of Active Directory events relevant for PKI
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
- Configure deterministic "good" for the online responder (OCSP).
- Force domain controller (or other participants) to use an online responder (OCSP)
- Editing the NTAuthCertificates object in Active Directory
External sources
- Event ID 21 - Kerberos Smart Card Authentication (Microsoft)
4 thoughts on “Details zum Ereignis mit ID 21 der Quelle Microsoft-Windows-Kerberos-Key-Distribution-Center”
Comments are closed.