| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 131 (0x83) |
| Event log: | Application |
| Event type: | Warning |
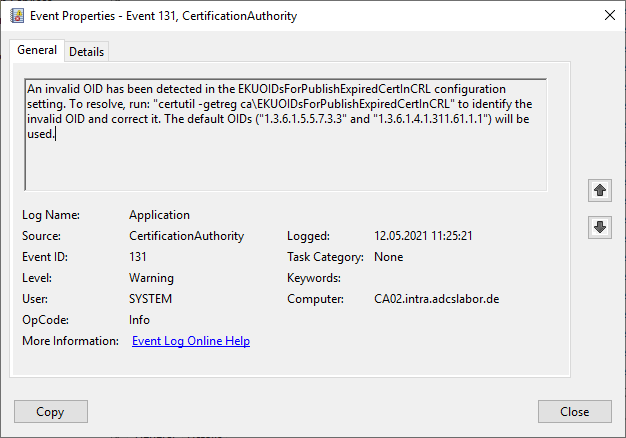
| Event text (English): | An invalid OID has been detected in the EKUOIDsForPublishExpiredCertInCRL configuration setting. To resolve, run: "certutil -getreg ca\EKUOIDsForPublishExpiredCertInCRL" to identify the invalid OID and correct it. The default OIDs ("1.3.6.1.5.5.7.3.3" and "1.3.6.1.4.1.311.61.1.1") will be used. |
| Event text (German): | An invalid OID was detected in the EKUOIDsForPublishExpiredCertInCRL configuration setting. To fix it, run the certutil -getreg ca\EKUOIDsForPublishExpiredCertInCRL command to detect and correct the invalid OID. The default OIDs ("1.3.6.1.5.7.3.3" and "1.3.6.1.4.1.311.61.1.1") are used. |
Example events
An invalid OID has been detected in the EKUOIDsForPublishExpiredCertInCRL configuration setting. To resolve, run: "certutil -getreg ca\EKUOIDsForPublishExpiredCertInCRL" to identify the invalid OID and correct it. The default OIDs ("1.3.6.1.5.5.7.3.3" and "1.3.6.1.4.1.311.61.1.1") will be used.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Occurs when the EKUOIDsForPublishExpiredCertInCRL value in the certification authority registry contains an invalid entry. It is located under the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\{Common-name-of-certification authority}
This value is used to enter the object identifiers for certificates whose serial numbers must continue to be entered in issued revocation lists even after their expiration date.
See also article "Treatment of expired certificates when issuing certificate revocation lists„.
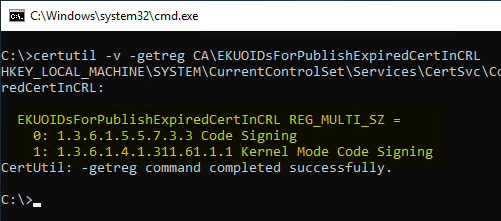
Only valid object identifiers may be entered. See also article "Frequently Used Extended Key Usages and Issuance Policies„.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
As a rule, it is not necessary to change the EKUOIDsForPublishExpiredCertInCRL value. Since the certification authority falls back to the default values in case of misconfigurations, no threat to availability is expected.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
External sources
- Securing Public Key Infrastructure (PKI) (Microsoft)
One thought on “Details zum Ereignis mit ID 131 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.