| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 103 (0x67) |
| Event log: | Application |
| Event type: | Warning |
| Symbolic Name: | MSG_E_MISSING_POLICY_ROOT |
| Event text (English): | Active Directory Certificate Services added the root certificate of certificate chain %1 to the downloaded Trusted Root Certification Authorities Enterprise store on the CA computer. This store will be updated from the Certification Authorities container in Active Directory the next time Group Policy is applied. To verify that the CA certificate is published correctly in Active Directory, run the following command: certutil -viewstore „%2“ (you must include the quotation marks when you run this command). If the root CA certificate is not present, use the Certificates console on the root CA computer to export the certificate to a file, and then run the following command to publish it to Active Directory: Certutil -dspublish %certificatefilename% Root. |
| Event text (German): | Das Stammzertifikat der Zertifikatkette %1 wurde in den Unternehmensspeicher der vertrauenswürdigen Stammzertifizierungsstellen auf den Zertifizierungsstellencomputer heruntergeladen. Dieser Speicher wird bei der nächsten Anwendung der Gruppenrichtlinie vom Zertifizierungsstellencontainer in Active Directory aktualisiert. Führen Sie folgenden Befehl aus, um sicherzustellen, dass das Stammzertifizierungsstellenzertifikat korrekt in Active Directory veröffentlicht wurde: certutil -viewstore „%2“ (beim Ausführen des Befehls müssen Sie auch die Anführungszeichen eingeben). Wenn das Stammzertifizierungsstellenzertifikat nicht vorhanden ist, verwenden Sie die Zertifikatkonsole auf dem Zertifizierungsstammcomputer, um das Zertifikat in eine Datei zu exportieren. Führen Sie anschließend den folgenden Befehl aus, um das Zertifikat in Active Directory zu veröffentlichen: Certutil -dspublish %certificatefilename% Root. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CACertIdentifier (win:UnicodeString)
- %2: LDAPPath (win:UnicodeString)
Example events
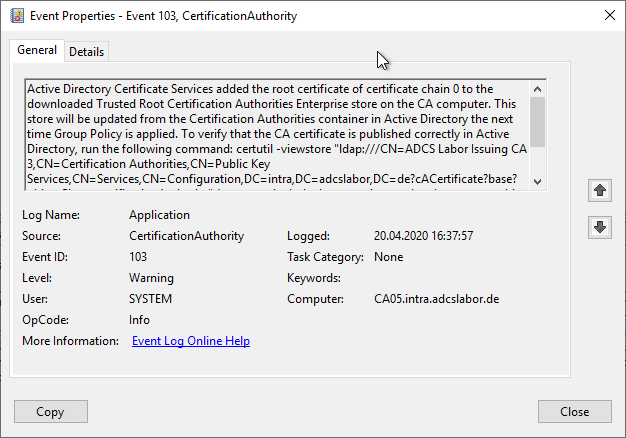
Active Directory Certificate Services added the root certificate of certificate chain 0 to the downloaded Trusted Root Certification Authorities Enterprise store on the CA computer. This store will be updated from the Certification Authorities container in Active Directory the next time Group Policy is applied. To verify that the CA certificate is published correctly in Active Directory, run the following command: certutil -viewstore "ldap:///CN=ADCS Labor Issuing CA 2,CN=Certification Authorities,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=de?cACertificate?base?objectClass=certificationAuthority" (you must include the quotation marks when you run this command). If the root CA certificate is not present, use the Certificates console on the root CA computer to export the certificate to a file, and then run the following command to publish it to Active Directory: Certutil -dspublish %certificatefilename% Root.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs when the certification authority detects that the certification chain of one of its certification authority certificates no longer points to a trusted root certification authority - i.e., the associated root certification authority appears to have had its trust status revoked.
If the LDAP AIA paths are still reachable, the certification authority itself restores the trust status and logs this event in the process.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
Since the certification authority was able to restore the trust status for itself, the event usually has no impact on availability, as the certification authority service continues to operate as usual.
See also article "What impact does the revocation of the trust status of a root certification authority certificate have on the certification authority?„.
However, it should be investigated whether the withdrawal of the certification authority's trust status has an impact on the PKI's participants, as they will most likely no longer trust the certification authority certificate.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
One thought on “Details zum Ereignis mit ID 103 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.