| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 100 (0x64) |
| Event log: | Application |
| Event type: | Error |
| Symbolic Name: | MSG_E_CA_CERT_INVALID |
| Event text (English): | Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. %1 %2. |
| Event text (German): | The Active Directory certificate services were not started: The current certification authority certificate could not be loaded or verified. %1 %2. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CACommonName (win:UnicodeString)
- %2: ErrorCode (win:UnicodeString)
Example events
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 2 Object was not found. 0x80090011 (-2146893807 NTE_NOT_FOUND).
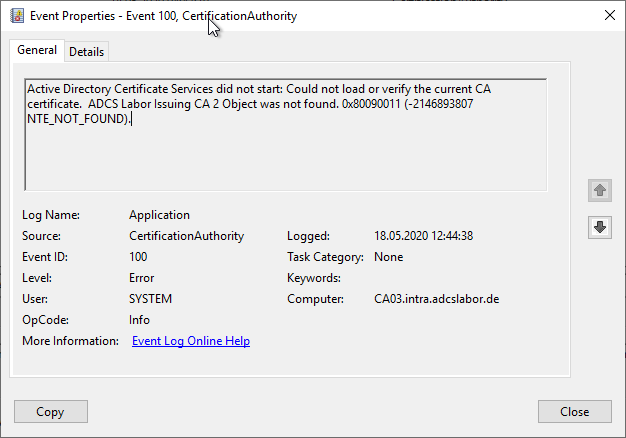
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING).
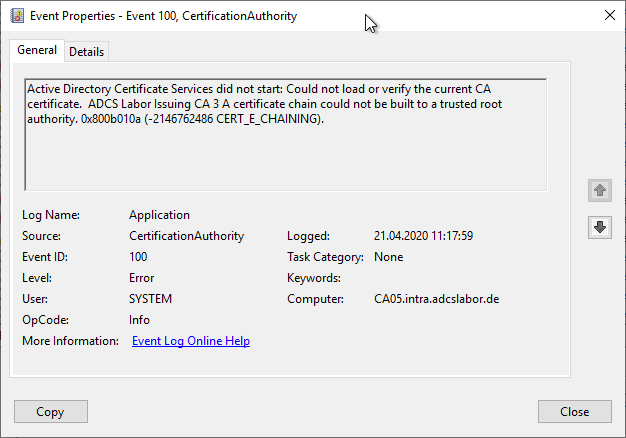
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 The certificate is revoked. 0x80092010 (-2146885616 CRYPT_E_REVOKED).
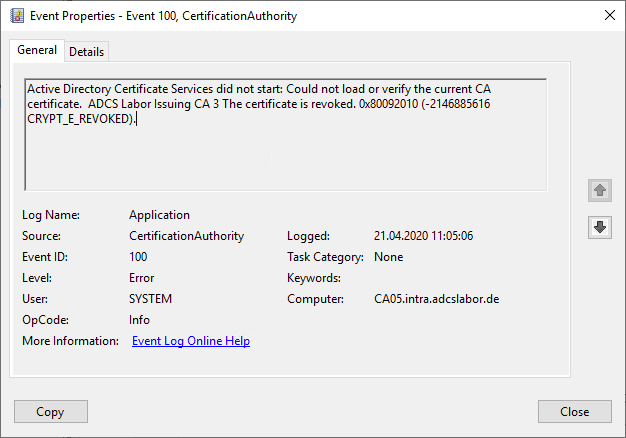
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
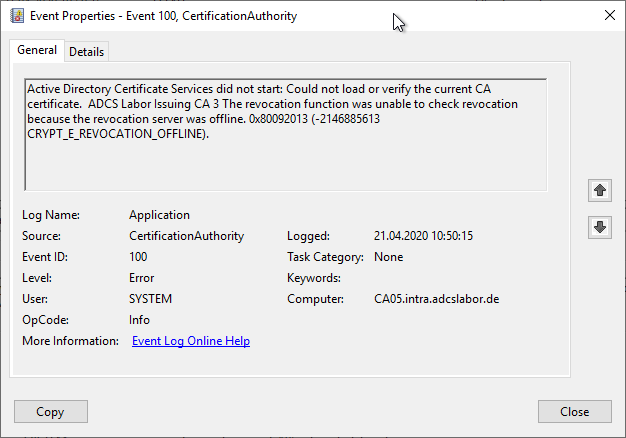
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT).
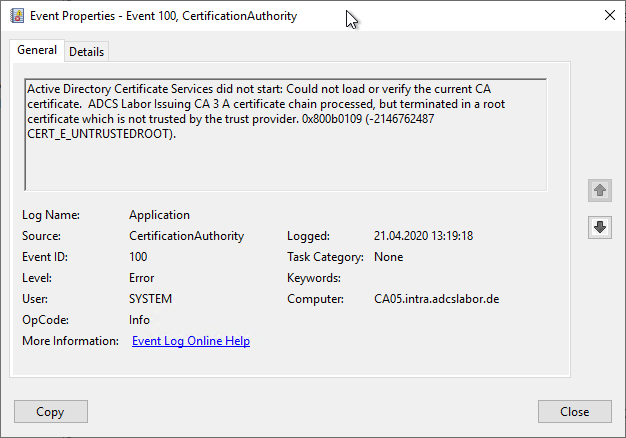
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 2 The device that is required by this cryptographic provider is not ready for use. 0x80090030 (-2146893776 NTE_DEVICE_NOT_READY).
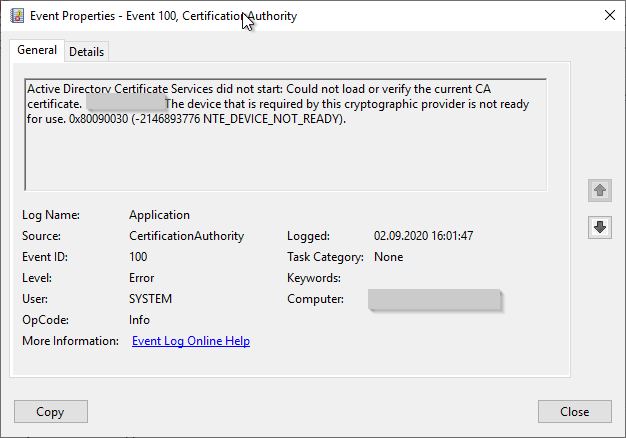
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 2 An internal consistency check failed. 0x8009002d (-2146893779 NTE_INTERNAL_ERROR).
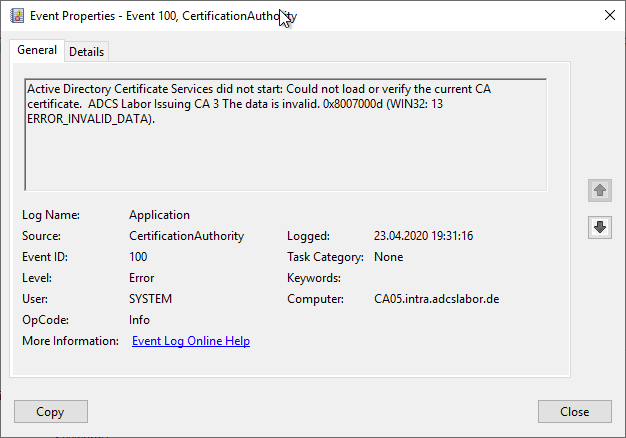
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 The data is invalid. 0x8007000d (WIN32: 13 ERROR_INVALID_DATA).
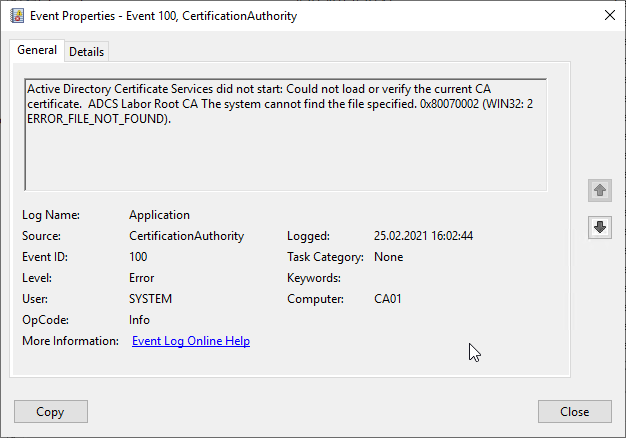
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Root CA The system cannot find the file specified. 0x80070002 (WIN32: 2 ERROR_FILE_NOT_FOUND).
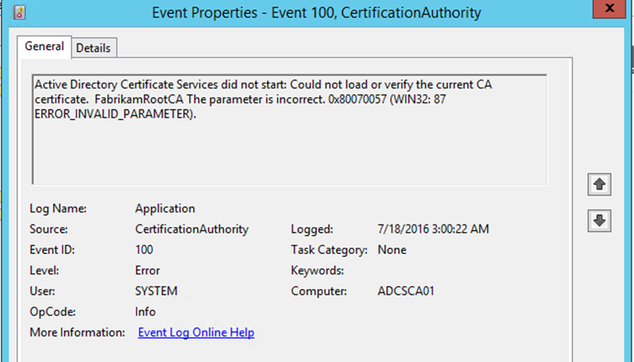
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. FabrikamRootCA The parameter is incorrect. 0x80070057 (WIN32: 87 ERROR_INVALID_PARAMETER).
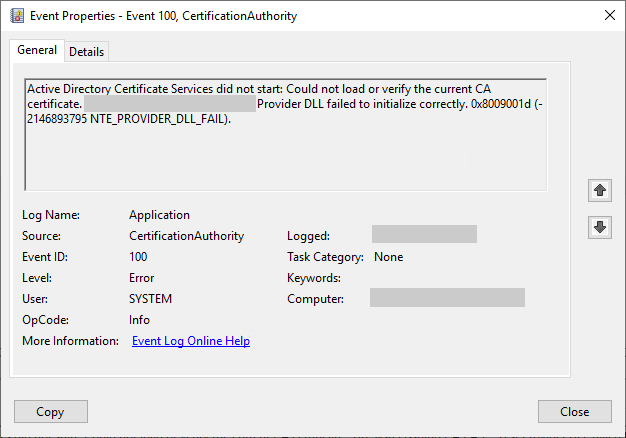
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 2 Provider DLL failed to initialize correctly. 0x8009001d (-2146893795 NTE_PROVIDER_DLL_FAIL).
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 2 An internal error occurred. 0x80090020 (-2146893792).
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs when the certification authority service cannot start because something is wrong with the certification authority certificate. This can have different causes:
Error code NTE_INTERNAL_ERROR
Occurs, among other things, when there is a problem accessing a private key of the certification authority (e.g. in case of problems with a hardware security module, (especially if the Cavium Key Storage Provider of the AWS CloudHSM is used).
Error code NTE_NOT_FOUND
Error code CERT_E_UNTRUSTEDROOT
Error code CERT_E_REVOKED
Error code CERT_E_CHAINING
Error code CERT_E_REVOCATION_OFFLINE
Error code NTE_DEVICE_NOT_READY
Error code ERROR_INVALID_PARAMETER
Error code ERROR_INVALID_DATA
Error code ERROR_FILE_NOT_FOUND
Error code NTE_PROVIDER_DLL_FAIL
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
From an operational point of view, this event is to be considered critical, as the availability of the service is no longer guaranteed. Users cannot apply for certificates.
In the long term, the certification authority's revocation lists will expire, which may lead to the failure of IT services that depend on the certification authority.
An emergency signing of the blacklists should be carried out immediately (see article "Perform emergency signing of certificate revocation lists"). If there is still access to the private key of the certification authority certificate (i.e. if the underlying problem is not due to a hardware security module that may be present), emergency signing of the revocation list can still be performed.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
16 thoughts on “Details zum Ereignis mit ID 100 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.