| Event Source: | Microsoft-Windows-CertificateServicesClient-CertEnroll |
| Event ID: | 10 (0x425A000A) |
| Event log: | Application |
| Event type: | Information |
| Event text (English): | Certificate enrollment for %1 archived or deleted, from the Personal certificate store, certificates that have expired, or been revoked or superseded. |
| Event text (German): | From the certificate enrollment for %1, certificates were archived or deleted from the personal certificate store that had expired or were revoked or superseded. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: Context (win:UnicodeString)
Example events
Certificate enrollment for INTRA\rudi archived or deleted, from the Personal certificate store, certificates that have expired, or been revoked or superseded.
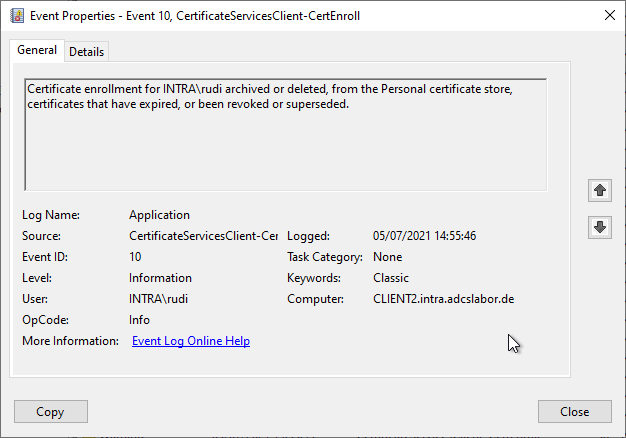
Certificate enrollment for Local system archived or deleted, from the Personal certificate store, certificates that have expired, or been revoked or superseded.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Occurs when certificates in the named user's certificate store were archived when the process was run.
Archiving is performed when Autoenrollment is configured via Group Policy and the option "Renew expired certificates, update pending certificates, and remove revoked certificates" is enabled.
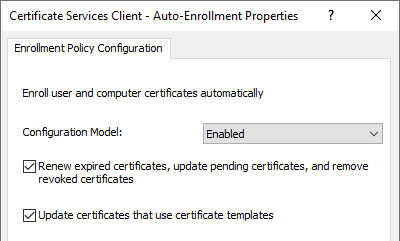
Reasons for archiving can be:
- The certificate was renewed and thus replaced by a newer one.
- The certificate has been revoked (and a new one has been requested).
- The certificate has expired (and a new one has been requested).
- The certificate is from a certificate template that has been replaced by another one (Superseded Templates tab in the certificate template settings).
Automatic archiving or deletion only works for certificates that have been made available via autoenrollment and always requires the reissuance of a certificate, i.e. a pure removal of a certificate without replacement cannot be mapped via this mechanism.
The decision whether to delete or archive a certificate is made using the "Delete revoked or expired certificates (do not archive)" setting in the certificate template. In the default setting, certificates are only archived, i.e. the archive bit is set so that the Certificate Enrollments are no longer offered during certificate selection.
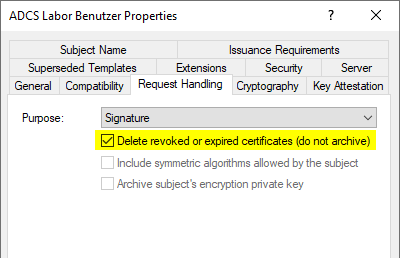
The option is not available if the Purpose option is set to Encryption or Signature and Encryption, in order to still be able to guarantee decryption of any data encrypted with the certificate.
The option enables the CT_FLAG_REMOVE_INVALID_CERTIFICATE_FROM_PERSONAL_STORE flag in the "msPKI enrollment flag" attribute of the certificate template.
Only the certificate is removed from the certificate store, the private key is not deleted. So a deleted certificate can be restored with the -repairstore option of certutil.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
No description has been written for this yet.
One thought on “Details zum Ereignis mit ID 10 der Quelle Microsoft-Windows-CertificateServicesClient-CertEnroll”
Comments are closed.