Assume the following scenario:
- A user's computer is stolen or infected with malware.
- The integrity of certificates located on the computer can no longer be guaranteed.
- The certificates of the user(s) that were requested on this computer must be revoked.
- However, one would like to avoid revoking all certificates of a user.
- Thus, a connection must be established between the user's certificates and the computer on which they were requested.
If the certificates were issued by Autoenrollment requested, we can take advantage of the fact that a corresponding attribute was part of the original certificate request, and that the certificate request is stored in the certificate authority database along with the certificate.
Sometimes it is necessary for a certificate issued by a certification authority to be withdrawn from circulation even before its expiration date. To make this possible, a certification authority keeps a revocation list. This is a signed file with a relatively short expiration date, which is used in combination with the certificate to check its validity.
The method does not work if Credential Roaming or Roaming User Profiles are configured, since the private keys will migrate to other machines in such a case.
In the Certificate Authority Management Console (certsrv.msc), you first switch to the "Issued Certificates". Then, under "View" - "Filter...", a filtering of the displayed database entries is performed.
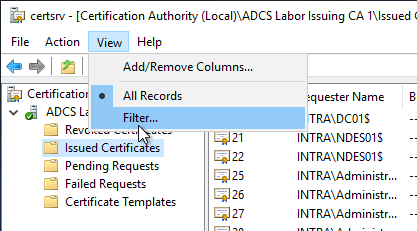
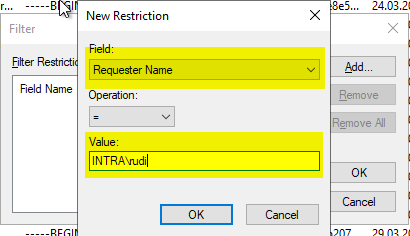
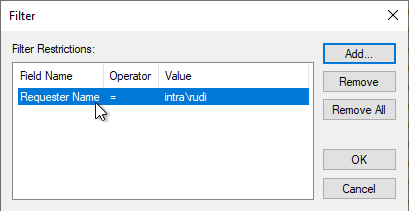
The filter is set to the "Requester Name" field. Only certificates that the relevant user has requested are to be displayed, in the example INTRA\rudi.
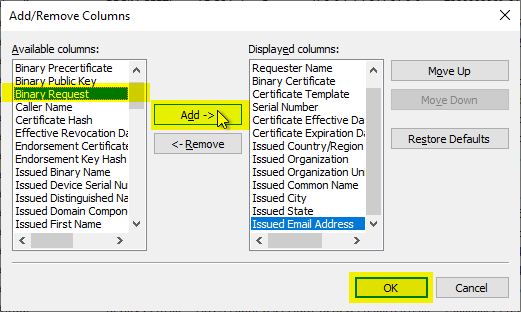
Then click on "View" - "Add/Remove Columns..." to add an additional column to the displayed database entries.
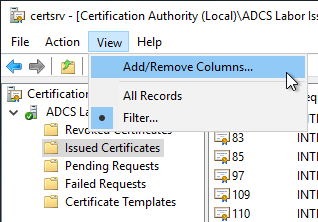
We specify that the "Binary Request" column should be output.
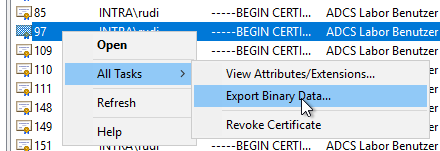
Now we are able to right-click the returned certificates in the result overview and select "All Tasks" - "Export Binary Data...".
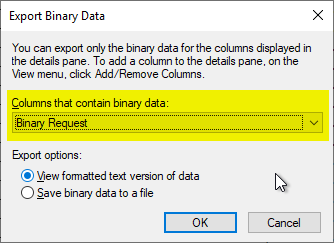
We have the "Binary Request" output in the "formatted text version of data".
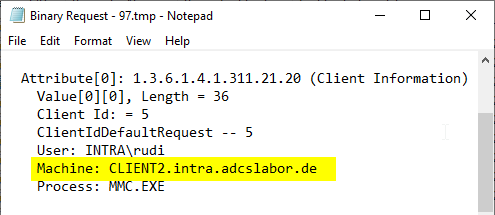
A text editor opens with a prepared output of the certificate request belonging to the certificate. Here you should find an attribute "Client Information" which contains, among other things, the host name of the associated computer.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.