To a Securing a Certification Authority also includes the backup of the private key material. The backup of the private key material is deliberately described separately, since this should be done separately and its backups should also be stored separately from those of the certification authority.
Private keys are the crown jewels of a certificate authority. If they fall into the wrong hands, they can be used to generate certificates that look as if they were legitimately issued by the certification authority, for any identity and application purpose. Such certificates may even be misused to take over the entire Active Directory forest. Accordingly, very great attention must be paid to their protection.
When should private key material be backed up?
Backing up the private key material is only necessary if new keys have been generated, for example when installing a certification authority, or when renewing certification authority certificates if new keys are used in the process.
Procedure
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
If a Hardware Security Module (HSM) is used
A hardware security module (HSM) is a piece of hardware that generates and stores cryptographic keys as securely as possible. The keys are located on the HSM and can be used by authorized clients (such as a certification authority), but cannot be copied.
The protection of the keys of a hardware security module depends on the HSM used and can therefore not be described here. For this purpose, the documentation of the respective hardware security module must be used.
When a software key is used
If no HSM is used, the private keys are stored using a software Key Storage Provider (KSP) stored. They lie, through the Data Protection Application Programming Interface (DPAPI) protected in the file system of the server on which the certificate authority is running.
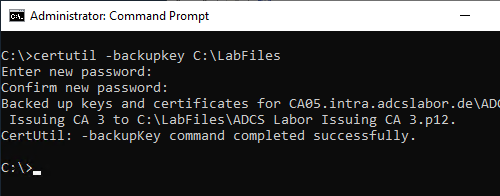
The backup of the private key can be performed with the following command line command:
certutil -backupkey {path-for-backup}
The strongest possible unique password should be used here, which is stored securely.
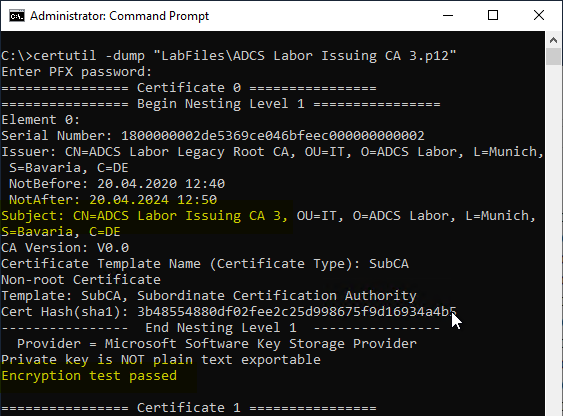
To check if the backup can be decrypted again with the password, the following command line command can be used:
certutil -dump {filename}.p12
In the command line output, it is now possible to check for each of the certificates whether the key was read. For this purpose, the sentence "Encryption Test passed" is searched for.
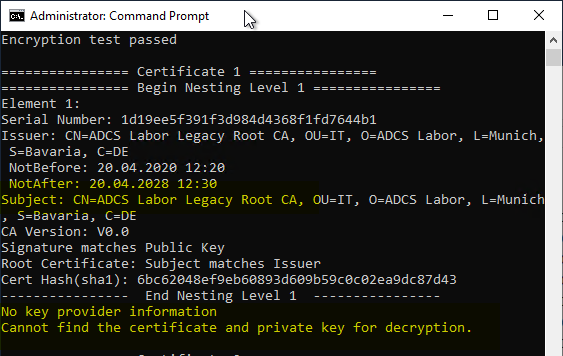
The backup of the certification authority certificates includes the entire certificate chain. Accordingly, the backup also contains the certificates of the higher-level certification authorities, which of course do not contain any private key material, so the test fails here as expected.
If Windows Server 2016 is used, you may see that the test failed. In this case, see article "What does the "Enable Certificate Privacy" option mean when exporting certificates?„.
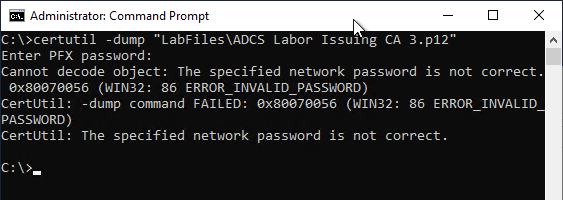
If the wrong password was entered, or if the password was not entered correctly during the backup, a corresponding error message is displayed.
One thought on “Eine Sicherung (Backup) des privaten Schlüssels einer Zertifizierungsstelle erstellen”
Comments are closed.