Below is a guide to configuring a web server template with recommended settings.
This step requires Enterprise Administrator or appropriately delegated rights to create and edit certificate templates.
Certificate template configuration
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The certificate template is configured via the Certificate Template Management Console (certtmpl.msc).
The default certificate template "Web Server" is used as a starting point and a copy of it is created.
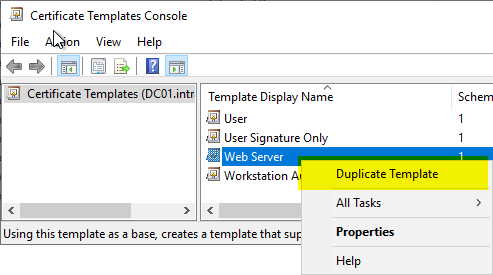
Compatibility" tab
We intend, Key Storage Provider (KSP) to be used. For this, it is necessary to set the compatibility settings for the certificate authority and certificate recipient to "Windows Vista" or "Windows Server 2008".
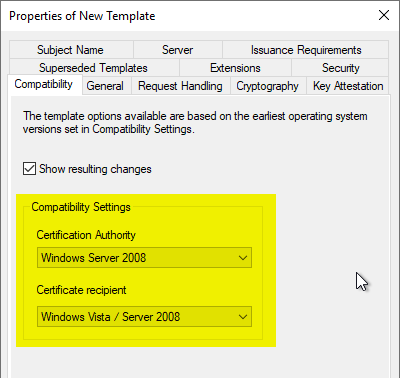
General" tab
A meaningful name is used in the "General" tab. The certificate validity should not be higher than two years.
Apple meanwhile enforcesthat web server certificates are not valid for more than two years (825 days).
Chrome and Safari the certificate validity meanwhile even to only one year. (398 days), but internal Certification Authorities are explicitly excluded from this restriction.
The "Renewal Period" is not relevant, since automatic renewal is not possible with this form of certificate submission.
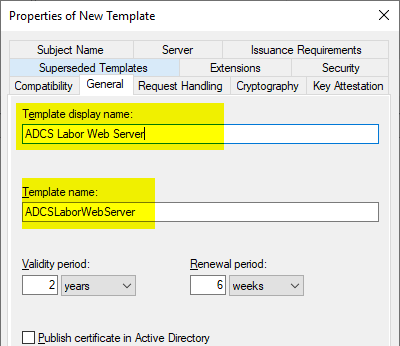
Request Handling" tab
In the "Request Handling" tab, the Purpose must be adapted to the key algorithm to be used. The background to this is that different requirements are placed on the "Key Usage" extension of the certificate depending on the key type (See RFC 5246 and RFC 4492).
| Key algorithm | Value |
|---|---|
| RSA | Signature and Encryption |
| ECDSA | Signature |
| ECDH | Signature and Encryption |
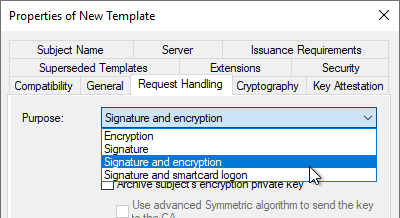
Cryptography" index card
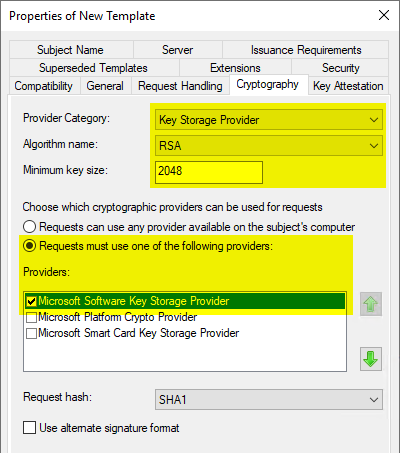
In the "Cryptography" tab, the "Key Storage Provider" category must now be selected and the respective key algorithm.
The Microsoft Software Key Storage Provider should be selected as the provider if it is not intended to store the keys, for example, with a Trusted Platform Module (TPM) to protect
When a Cryptographic Service Provider (CSP) is to be used, the "Microsoft RSA SChannel Cryptographic Provider"must be used. This only supports AT_KEYEXCHANGE, so the Purpose must be set to "Signature and Encryption" in the "Request Handling" tab. In principle, a key storage provider should be preferred if possible.
The choice of provider only affects certificate requests that read the certificate template during the request (i.e., manual or automatic certificate requests via autoenrollment).
Subject Name" tab
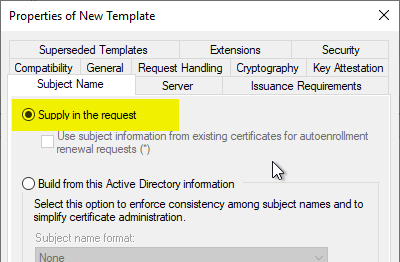
In the "Subject Name" tab, make sure that the "Supply in the request" option is selected (default setting). This causes that the applicant can determine the identity in the certificate. This is necessary because websites often use an alias that cannot be mapped as a Kerberos identity. Accordingly, the identity of the requester and that of the website differ from each other.
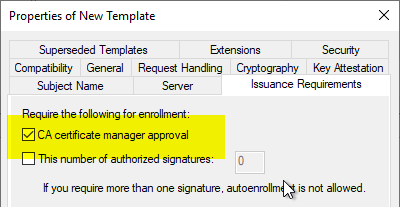
Since the previous setting involves a security risk (the requester could request certificates for any subject names), it is mandatory that the "CA certificae manager approval" option be set in the "Issuance Requirements" tab. This ensures that the certificate request is not issued directly, but instead ends up in the "Pending Requests" folder, where a certificate manager can check them.
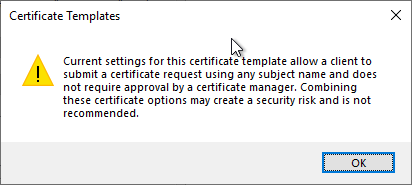
If you uncheck the box for "CA certificate manager approval", a warning message will also appear.
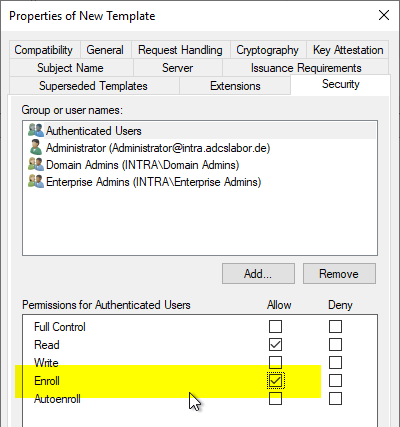
Security" tab
In the "Security" tab, the desired person or user group can now be granted the "Enroll" right.
Since the certificate template is configured so that incoming certificate requests end up in the "Pending Requests" folder and must first be reviewed and approved by a certificate manager, granting the "Enroll" right as in this example is not a security risk.
Further safety hardening
Restricting the requestable certificate content (for example, which domain names can be requested) and ensuring that the correct key algorithm is used can be done with the TameMyCerts Policy Module for the Certification Authority be ensured.
Apply for a web server certificate
The procedure for applying is described in the article "Manually requesting a web server certificate" described.
Related links:
- Manually send a certificate request (CSR) to a certification authority
- Inspect a certificate request (CSR)
- Chrome and Safari limit SSL certificates to one year validity
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
External sources
- Enforce 398-day validity for certificates issued on-or-after 2020-09-01 (Chromium Project)
- About upcoming limits on trusted certificates (Apple)
- Requirements for trusted certificates in iOS 13 and macOS 10.15 (Apple)
- Reducing TLS Certificate Lifespans to 398 Days (Mozilla)
- Limit TLS Certificates to 398 day validity after Aug 31, 2020 (Mozilla)
14 thoughts on “Konfigurieren einer Secure Socket Layer (SSL) Zertifikatvorlage für Web Server”
Comments are closed.