After configuring a certificate template for the distribution of Remote Desktop certificates (see the article "Configuring a Certificate Template for Remote Desktop (RDP) Certificates"), a group policy is still required that instructs the participating computers to also use the certificates originating from the template.
Implementation
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
First, a new Group Policy Object (GPO) is created and edited via the Group Policy Management Console (gpmc.msc).
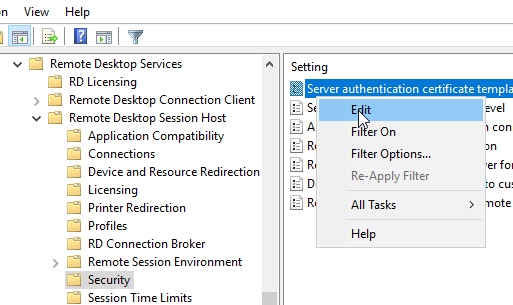
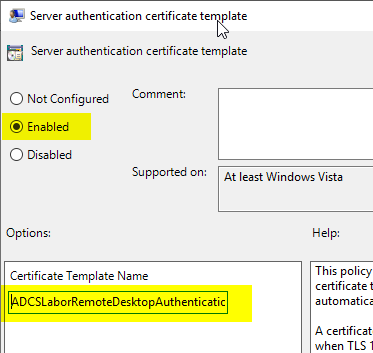
Navigate to "Computer Configuration" - "Windows Components" - "Remote Desktop Services" - "Remote Desktop Session Host" - "Security". There you select the option "Server authentication certificate template" and edit it.
Set the setting to "Enabled" and specify the object name (the name without spaces) of the certificate template.
The group policy can now be distributed to the participating machines.
Client side behavior
To better understand the client-side behavior, it helps to have a look at the description within the configuration dialog:
If no certificate can be found that was created with the specified certificate template, the RD Session Host server will issue a certificate enrollment request and will use the current certificate until the request is completed. If more than one certificate is found that was created with the specified certificate template, the certificate that will expire latest and that matches the current name of the RD Session Host server will be selected.
This means that the client will behave as follows:
- Is there already a (valid) certificate issued by the configured certificate template (for example, because it was distributed in advance via autoenrollment), it is used and bound on the remote desktop session host.
- If no certificate is available, the remote desktop session host requests one, even if the certificate template is not configured for autoenrollment (indicated by the Event with ID 1063 of source Terminalservices-RemoteConnectionManager).
- If there is only one certificate that will expire in less than two days, a new one will be requested by the remote desktop session host (also recognizable by the Event with ID 1063 of source Terminalservices-RemoteConnectionManager).
Thus, the configuration will work even if the certificate template for Remote Desktop certificates has not been configured for autoenrollment. However, due to better management, it is recommended to use Autoenrollment.
For example, vulnerability scanners such as Qualys will report a finding if remote desktop certificates are not renewed until two days before expiration.
Next steps
How to verify that the clients are actually using the Remote Desktop certificates is described in the article "Identify the active Remote Desktop (RDP) certificate" described.
Related links:
- Configuring a Certificate Template for Remote Desktop (RDP) Certificates
- Identify the active Remote Desktop (RDP) certificate
External sources
- Configuring Remote Desktop certificates (Microsoft, archive.org)
8 thoughts on “Konfigurieren einer Gruppenrichtlinie (GPO) für Remotedesktop (RDP) Zertifikate”
Comments are closed.