The Network Device Enrollment Service (NDES), because it implements the web-based Simple Certificate Enrollment Protocol (SCEP), is mapped as a web application in Microsoft Internet Information Service (IIS). Here, the service runs in an application pool called "SCEP". In many cases it is sufficient to use the integrated application pool identity for it.
However, there are cases where you want to use a domain account. An example of this is the Certificate Connector for Microsoft Intune, which requires this.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Configuring NDES with a domain account requires the following steps:
- Service Principal Name (SPN) register for Kerberos authentication.
- "Enroll" authorization for the domain account to the NDES Device Template put
- "Read" permissions on private keys of the Registration Authority Certificates (Note: This is also possible by default setting of the certificate template. Full access is not necessary).
- Configure membership in the local IIS_IUSRS group on the NDES server for the domain account.
- Impersonate a Client after Authentication (SeImpersonatePrivilege, given by membership in IIS_IUSRS by default) on the NDES server for the domain account.
- Configure Log on as a Batch Job (SeBatchLogonRight, given by membership in IIS_IUSRS by default) on the NDES server for the domain account.
- Entering the domain account as the identity of the "SCEP" application pool.
Details: Register service principal names
setspn -s http/{DNS name-NDES server} {domain name}\{name-NDES service account}
Details: Entering the identity of the application pool
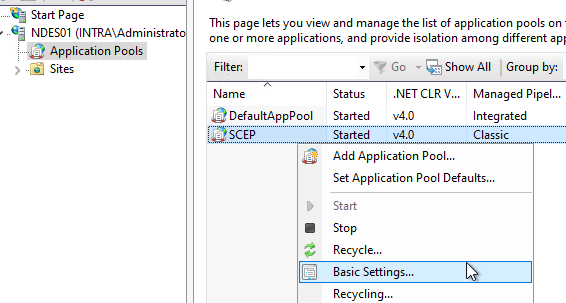
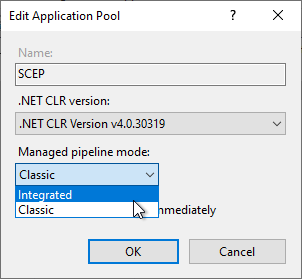
Related links:
- Required Windows security permissions for the Network Device Enrollment Service (NDES)
- The Certificate Connector for Microsoft Intune throws the error message "ArgumentException: String cannot be of zero length" during configuration.
- Selecting the identity for the IIS Network Device Enrollment Service (NDES) application pool.
External sources
- Configure infrastructure to support SCEP with Intune (Microsoft Corporation)
2 thoughts on “Den Registrierungsdienst für Netzwerkgeräte (NDES) für den Betrieb mit einem Domänenkonto konfigurieren”
Comments are closed.