The following describes the steps required to configure the Network Device Enrollment Service (NDES) for use with an alias.
The term alias means that the service is not called with the name of the server on which it is installed, but with a generic name independent of this name. The use of an alias allows the service to be moved to another system at a later time without having to inform all participants of the new address.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Implementation
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To configure the Network Device Enrollment Service (NDES) for use with an alias, the following steps are required:
- Create a DNS record for the alias
- Configuring a Service Principal Name (SPN) for the Service Account
- Optional: Apply for an SSL certificate customized to the alias.
- Perform function test
- Communication of the alias to the participants
Details: Creating a DNS record for the alias
The alias must first be created in the Domain Name System (DNS).
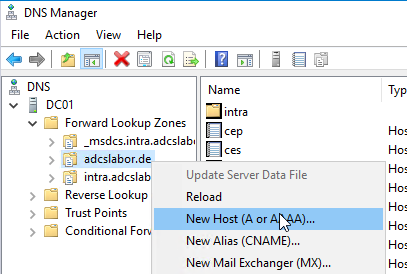
It is essential to use an A redord. When using a CNAME the Kerberos login on the NDES administration web page will fail and you will be asked to login again and again.
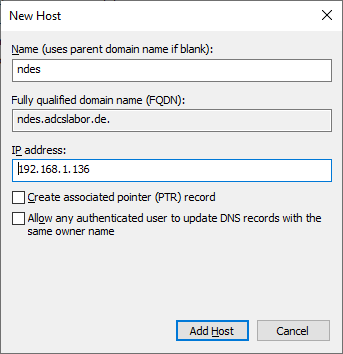
Details: Configuring a Service Principal Name (SPN) for the service account.
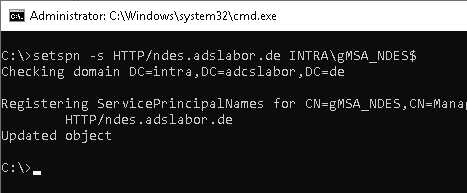
For Kerberos login to the NDES administration website (mscep_admin), a service principal name must be set on the NDES server service account. This is done with the following command line command:
setspn -s HTTP/{alias} {domain}\{service account}
If a Group Managed Service Account (gMSA) is used for NDES, a dollar sign must be included at the end when entering the account name so that the appropriate account can be found.
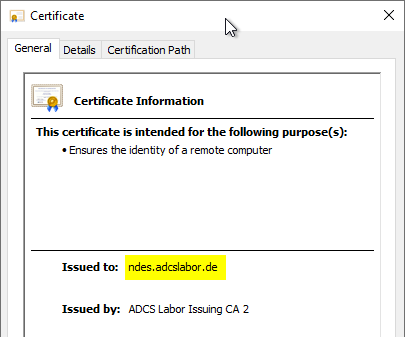
Details: Requesting an SSL certificate customized to the alias.
This step is only required if the NDES Administration web page has been configured with SSL, but it is strongly recommended (see article "Enabling Secure Sockets Layer (SSL) for the Network Device Enrollment Service (NDES).„).
The identity configured in the certificate (DNSName in the Subject Alternative Name field) must match the alias.
The generation of a corresponding certificate request is described in the article "Generating a RFC 2818 compliant certificate request for SSL certificates" described.
The change of the SSL certificate requires none Restart of the web server and thus NDES service.
Details: Perform function test
After each change to an IT service, an extensive functional test should be performed. The procedures for NDES are described in the article "Performing a functional test for the network device registration service (NDES)" described.
Details: communication of the alias to the participants
If the functional test was successful, the participants (for example, Mobile Device Management (MDM) administrators) must be notified of the change so that the new alias can be used.
4 thoughts on “Den Network Device Enrollment Service (NDES) für die Verwendung mit einem Alias konfigurieren”
Comments are closed.