For a function test or during troubleshooting, it can be useful to check whether the private key of a certificate is usable. If the key is secured with a hardware security module (HSM), for example, there are significantly more dependencies and possibilities for errors than with a software key.
Certificate identification
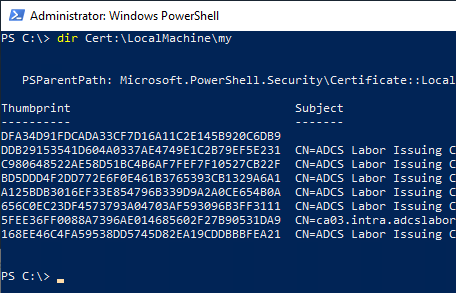
First, the SHA1 fingerprint (thumbprint) of the certificate must be determined. In Windows PowerShell, this is possible with the following command, for example.
For computer certificates
Get-ChildItem -Path Cert:\LocalMachine\My
For user certificates:
Get-ChildItem -Path Cert:\CurrentUser\My
In the computer store certificate management console (certlm.msc), this can be done by selecting the certificate and switching to the "Details" tab. The information is located under "Trhumbprint".
Perform verification
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
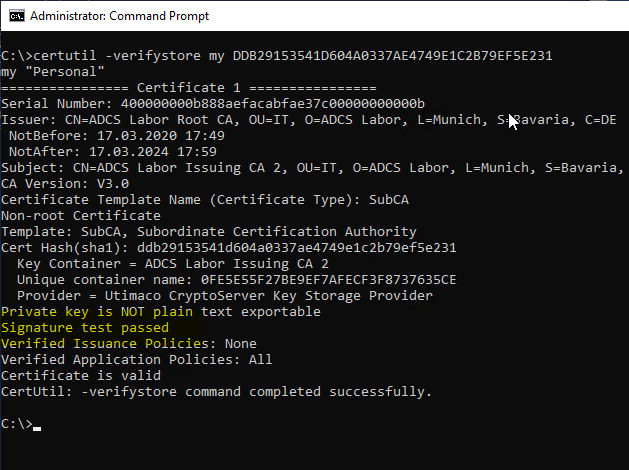
Then the private key verification can be done with the following command.
For computer certificates:
certutil -verifystore my {Thumbprint}
For user certificates:
certutil -user -verifystore my {Thumbprint}
It is necessary that the user verifying the private key is authorized to use the key. Especially when a hardware security module is used, this is not the case with every manufacturer. One account that must always have access to the private key is the SYSTEM account, since it is under its security context that the certificate authority service is run. How to perform a check in this context is described later in the article.
Perform verification (SYSTEM context)
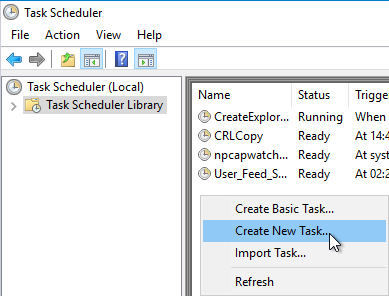
To perform the scan in the SYSTEM context, it is useful to create a scheduled task, since the account under which it will be executed can be specified here. First, a batch file is created that contains the command for the check.
To intercept the command line output, it is redirected to a text file.
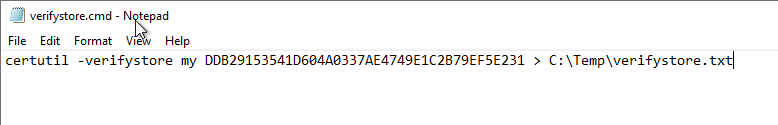
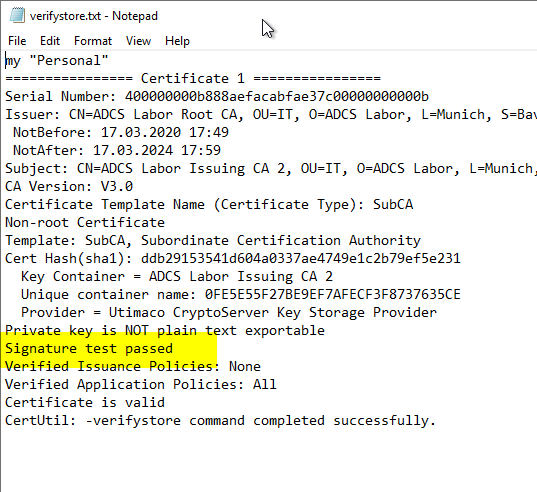
certutil -verifystore my {Thumbprint} > {Path}\{File}.txt
It is essential to specify the absolute path, otherwise the text file will be saved in C:\Windows\System32.
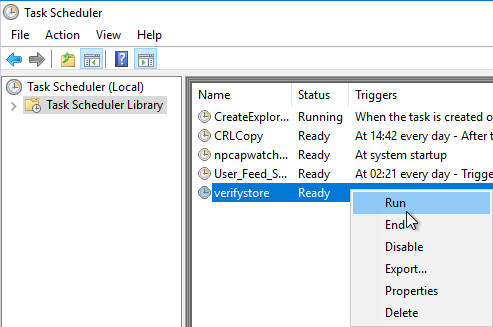
A new task is then created via the task list and .
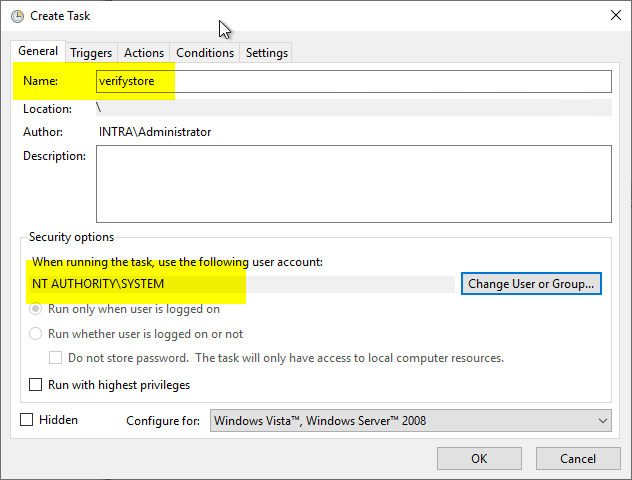
A meaningful name is assigned in the "General" tab. NT-AUTHORITY\SYSTEM is entered as the identity.
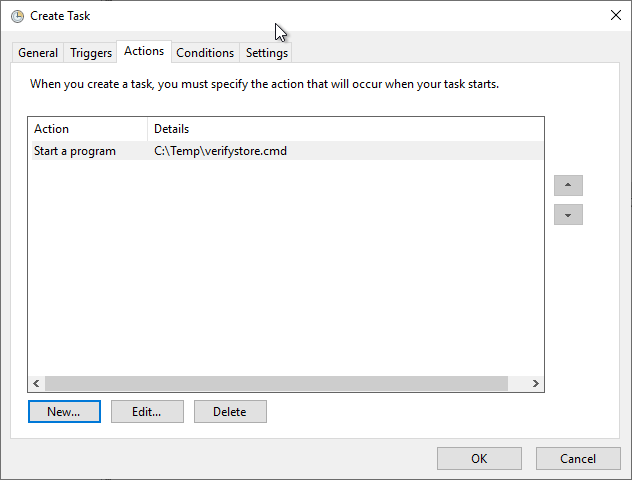
The "Triggers" tab can be skipped because the task is started manually. In the "Actions" tab, a new action "Start a program" is created and the path to the script file is specified.
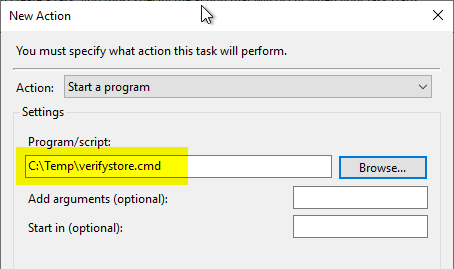
Then the task can be started manually.
Now a text file should be generated containing the result of the check.
One thought on “Überprüfen der Verbindung zum privaten Schlüssel eines Zertifikate (z.B. bei Einsatz eines Hardware Security Moduls)”
Comments are closed.