Assume the following scenario:
- Certificates for domain controllers are issued by an Active Directory integrated certificate authority (Enterprise CA)
- The certificate template used for this purpose was created by the user
- The issued certificates contain in the Subject Alternative Name (SAN) only the fully qualified computer name of the respective domain controller, but not the fully qualified name and the NETBIOS name of the domain
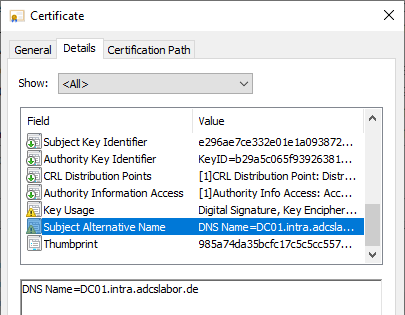
There is also no option in the certificate template to force this information to be entered.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
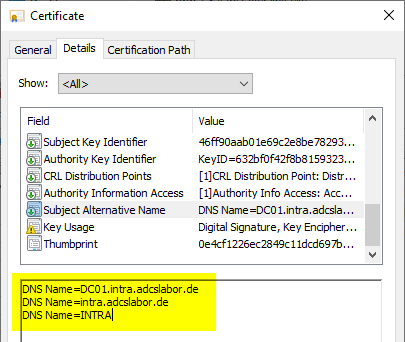
The fully qualified domain name and the NETBIOS name of the domain are determined based on a flag CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS is entered in issued certificates. Whether this flag is set on the certificate template can be checked with the following command line command.
certutil -v -template {name-of-template} | findstr REQUIRE_DOMAIN
The name of the template is the object name, in most cases the name of the template. without spaces to be entered.
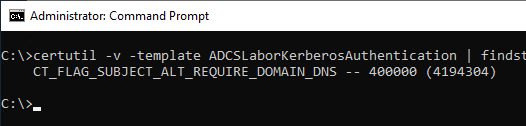
If your own certificate template is used, it should be derived from the standard certificate template "Kerberos Authentication", because only this certificate template uses the flag CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS has been set. The default certificate templates "Domain Controller" and "Domain Controller Authentication" have the flag not set.
The flag can also be set manually via the ADSI editor for the existing certificate template, but this method is not supported by the manufacturer.
If the CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS flag is set, the certification authority must be able to communicate with the requesting computer (i.e., a domain controller in most cases) via TCP port 445 (RPC named pipes). For more details, see the article "Firewall rules required for Active Directory Certificate Services„.
6 thoughts on “Zertifikate für Domänencontroller enthalten nicht den Domänennamen im Subject Alternative Name (SAN)”
Comments are closed.