Certificate extensions were introduced with version 3 of the X.509 standard. The Key Usage extension is an optional certificate extension that can be used in the RFC 5280 is defined and is used to limit the allowed uses for a key.
This is a simple bitmask.
KeyUsage ::= BIT STRING {
digitalSignature (0),
nonRepudiation (1),
keyEncipherment (2),
dataEncipherment (3),
keyAgreement (4),
keyCertSign (5),
cRLSign (6),
encipherOnly (7),
decipherOnly (8)
}
However, the representation of the bit mask is usually in hexadecimal form.
| Bit | Hex | Description | Label |
|---|---|---|---|
| 8 | 0x0 | decipherOnly | Decrypt only, in conjunction with keyAgreement |
| 7 | 0x1 | encipherOnly | Encrypt only, in conjunction with keyAgreement |
| 6 | 0x2 | cRLSign | Signing blacklists |
| 5 | 0x4 | keyCertSign | Signing certificates |
| 4 | 0x8 | keyAgreement | Used, for example, for data encryption with the Diffie-Hellman method |
| 3 | 0x10 | dataEncipherment | Data encryption, directly with the key contained in the certificate |
| 2 | 0x20 | keyEncipherment | Key encryption, i.e. when a symmetric key is used for data encryption and this is encrypted with the key contained in the certificate |
| 1 | 0x40 | nonRepudiation | Non-repudiation |
| 0 | 0x80 | digitalSignature | Digital signature |
Typical examples of common use cases for certificates
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Certification Authority Certificates
Certification authority certificates must have a key usage extension according to RRC 5280. This should be marked as critical. The extension will typically include keyCertSign and keyCrlSign. The Microsoft Certificate Authority will also include digitalSignature, but this should not be done according to RFC 5280.
There is the possibility, configure the Key Usage extension differently when installing a certificate authority.
TLS web server certificates
At TLS web server certificates it depends on which type of key is used (see RFC 5246 and RFC 4492).
| Key algorithm | Value |
|---|---|
| RSA | Signature and Encryption |
| ECDSA | Signature |
| ECDH | Signature and Encryption |
S/MIME certificates
With Secure/Multipurpose Internet Mail Extensions (S/MIME), two operations are basically possible with regard to e-mail messages:
- Signing sent messages or verifying the signatures of received messages
- Encrypt messages sent or decrypt messages received
When configuring the certificates, you have the choice of using a hybrid certificate (which supports both operations) or separate certificates for both operations.
| Type of certificate | Key Usage Extension |
|---|---|
| Encrypt/Decrypt only | keyEncipherment (0x20) |
| Sign/verify only | digitalSignature (0x80) |
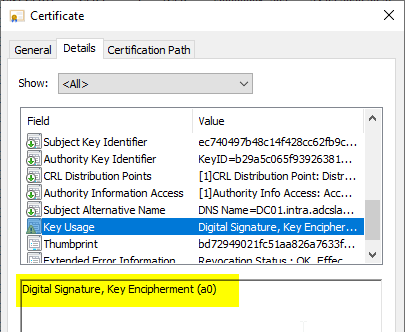
| both operations (hybrid certificate) | digitalSignature, keyEncipherment (0xA0) |
Calculate with the Key Usage extension
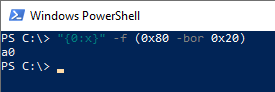
A very simple way to calculate a key usage is possible with Windows PowerShell.
An example: digitalSignature (0x80) and keyEncipherment (0x20) together result in 0xA0.
"{0:x}" -f (0x80 -bor 0x20)
Related links
External sources
- Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile / Key Usage (Internet Engineering Task Force)
- All About Certificate Extensions (Mozilla)
3 thoughts on “Grundlagen: Die Key Usage Zertifikaterweiterung”
Comments are closed.