Certificate revocation lists (CRLs) are used to remove issued certificates from circulation before the end of their validity period.
A CRL is a signed list of the serial numbers of certificates that have been revoked by the certification authority. The revocation list has an expiration date (usually a few days short) and is reissued and signed by the associated certification authority at regular intervals.
Certificate revocation lists can reach a considerable size if the volume of revoked certificates is high (as a rule of thumb, you can expect about 5 megabytes per 100,000 entries). The regular download of large certificate revocation lists by subscribers can generate a large network load. To address this problem, there is the concept of delta revocation lists.
Sometimes it is necessary for a certificate issued by a certification authority to be withdrawn from circulation even before its expiration date. To make this possible, a certification authority keeps a revocation list. This is a signed file with a relatively short expiration date, which is used in combination with the certificate to check its validity.
Functionality
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The idea with delta revocation lists is to extend the publication intervals of the (supposedly large) base revocation list so that it needs to be downloaded less frequently by participants. Changes that have occurred since the last publication of the basic blacklist are written to the delta blacklist, which is published at shorter intervals.
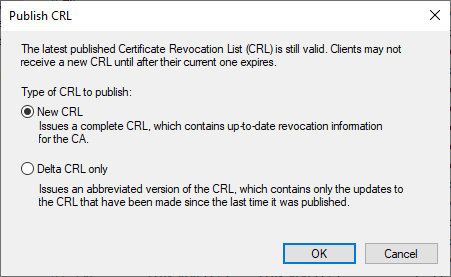
A base revocation list can therefore have several delta revocation lists associated with it. When publishing certificate revocation lists, you have the choice of publishing the base revocation list or a new delta revocation list.
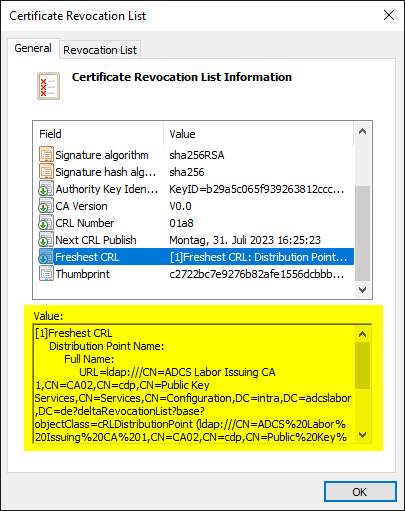
If delta revocation lists are active, the base revocation list has an extension called "Freshest CRL" which contains the URL for downloading the delta revocation list.
If delta revocation lists are activated, a revocation status check is thus only possible if both the basic revocation list and an associated delta revocation list can be retrieved and are time valid.
Mapping in Microsoft Active Directory Certificate Services
Configuration
The configuration of the blacklist validity is mapped in the registry under the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\{name-of-certification authority>
| Registry value | Default value |
|---|---|
| CRLPeriodUnits | 1 |
| CRLPeriod | Weeks |
| CRLOverlapUnits | 0 |
| CRLOverlapPeriod | Hours |
| CRLDeltaPeriodUnits | 1 |
| CRLDeltaPeriod | Days |
| CRLDeltaOverlapUnits | 0 |
| CRLDeltaOverlapPeriod | Minutes |
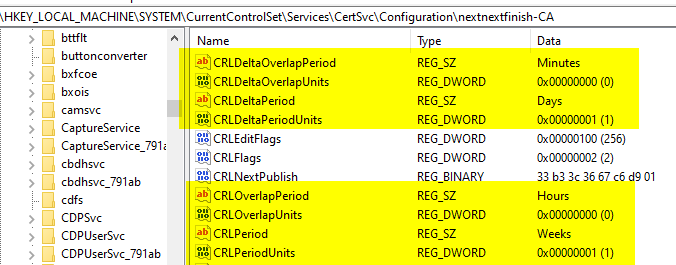
Default values
If you install a Microsoft Certification Authority with default settings, delta revocation lists are automatically enabled with the following settings:
| Brevocation list | Parameter | Explicitly configured value | Effective value |
|---|---|---|---|
| Basic revocation list | Validity | 1 week | 1 week |
| Basic revocation list | Overlap period | 0 hours | 12 hours |
| Delta revocation list | Validity | 1 day | 1 day |
| Delta revocation list | Overlap period | 0 minutes | 12 hours |
As you can see, the values for the overlap periods are set to 0 in each case. However, this does not mean that the blacklist overlap is thus enabled. Rather, the certification authority applies default values of 12 hours. This results in the following validity periods in the default setting:
- The basic blacklist is valid for 180 hours (1 week + 12 hours) and is renewed 12 hours before expiration.
- The delta revocation list is valid for 36 hours (1 day + 12 hours) and is renewed 12 hours before expiration.
The Microsoft Certification Authority sets the issue date of the blacklists 10 minutes into the past in each case. Likewise, the end date is extended by 10 minutes. This procedure is intended to prevent possible problems with time synchronization between the participants.
On the usefulness of delta revocation lists
Most enterprises will never be embarrassed to revoke so many certificates that significant load situations could occur without delta revocation lists. De facto, most companies have not even implemented a resilient certificate revocation process.
The use of delta revocation lists can provide a security advantage (due to their usually very short validity periods), as certificate revocations become effective very quickly.
It should be noted, however, that the time required for emergency measures such as the establishment of an emergency blacklist in the event of a certification authority or hardware security module failure is equally drastically shortened by the use of delta blacklists.
Thus, the decision for or against delta revocation lists ultimately depends on the use cases employed. However, it can be said that the requirement for operability (operational stability) will generally take precedence over any certificate blocking that becomes effective at short notice.
An alternative to delta revocation lists can be the use of an Online Responder (OCSP) . However, this service is only suitable for improving efficiency.
Disable delta revocation lists
In many cases, it may make sense to deactivate the delta revocation lists and instead prefer to work with larger overlap periods of the basic revocation list.
Deactivate via the registry
If you set the "CRLDeltaPeriodUnits" in the registry to the value 0 and then restart the certification authority, it will no longer issue delta revocation lists.
certutil -setreg CA\CRLDeltaPeriodUnits 0 net stop certsvc net start certsvc
It is advisable to issue a new base revocation list directly, which no longer refers to a delta revocation list, i.e. no longer has a "Freshest CRL" extension.
certutil -crl
However, deactivating the delta revocation lists via the registry has the disadvantage that there may be problems with certificate revocation lists cached at the subscribers. They may continue to use the old base revocation list until it expires, but they can no longer access an associated valid delta revocation list because these are no longer issued.
Therefore, it is advisable to always disable delta revocation lists via the Certification Authority Management Console.
Disable via the Certification Authority Management Console
In the Certificate Authority Management Console, delta revocation lists can be configured by right-clicking on the revoked certificates folder.
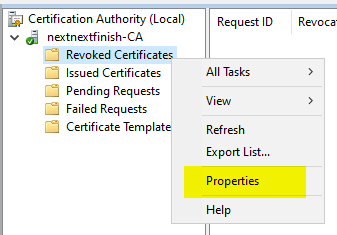
If the "Publish Delta CRLs" checkbox is removed, the certification authority will no longer issue new delta revocation lists.
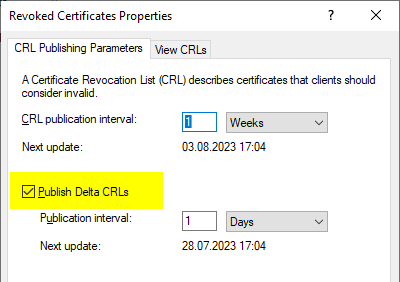
However, something additional is happening behind the scenes. The certification authority immediately issues a new basic revocation list (pictured on the left), which no longer includes a "Freshest CRL" extension. In addition, however, a delta blacklist (pictured right) is issued one last time, which has the same expiration date as the base blacklist.
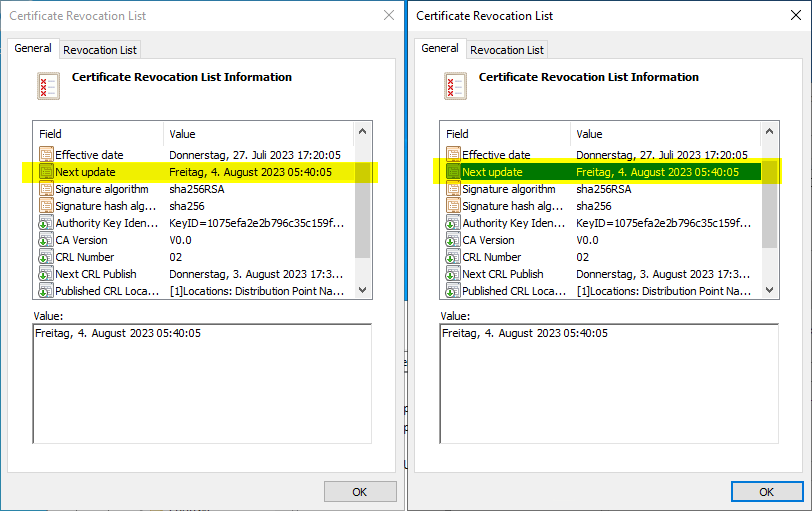
This prevents subscribers from encountering the inconsistent situation described earlier and from being unable to check certificates for their revocation status.
Related links:
- Basics: Checking the revocation status of certificates
- Basics of online responders (Online Certificate Status Protocol, OCSP)
External sources
- Configure CRL and delta CRL overlap period (Microsoft Corporation)
- Can disabling Delta CRL on a CA cause problems? (Tom Aafloen)