Assuming a use case is implemented for certificates where users specify the identity contained in the certificate in the certificate request, and this requires manual intervention by the certificate managers, the question arises as to how to proceed when the certificates expire or the certificate template is moved to another certification authority in order to minimize tickets at the help desk and thus the resulting work for the certificate managers.
Both methods also work with a change of the issuing certification authority, i.e. the renewed certificates are issued by a different certification authority than the previous ones. The only requirement is that both certification authorities are members of the same Active Directory forest.
The initial situation
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The certificate template in question is configured in the "Subject Name" tab accordingly to let the requester submit the identity in the certificate request ("Supply in the request").
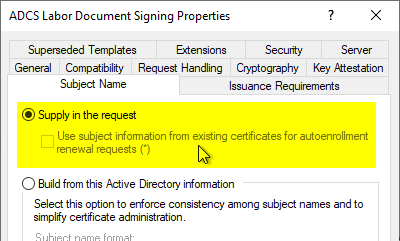
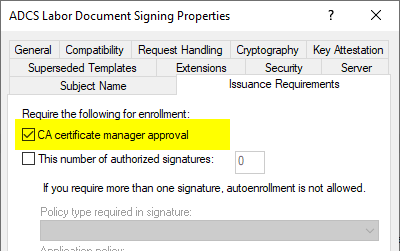
For security reasons, the certificate template in the Issuance Requirements tab requires manual review of incoming certificate requests by a certificate manager.
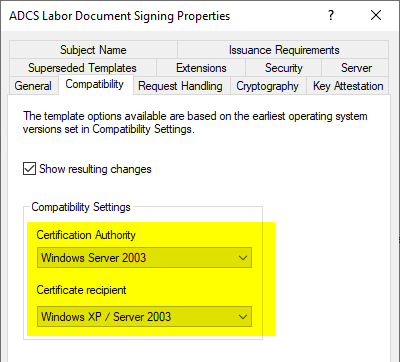
The compatibility options for the certificate template are set to "Windows Server 2003" for the certification authority and "Windows XP" for the certificate recipients. Thus, this is a version 2 certificate template.
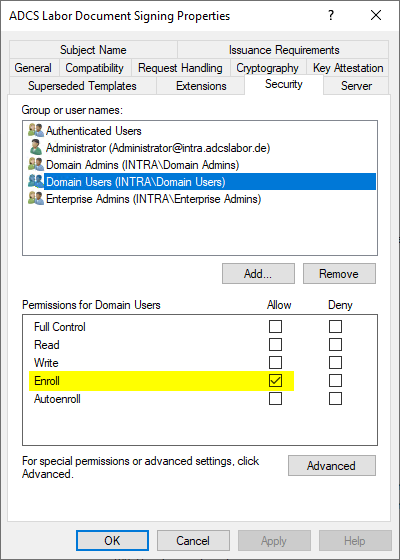
The users in question have the "Enroll" right, but not the "Autoenroll" right. You must therefore trigger the certificate request manually.
When a certificate is about to expire, users are prompted to renew. However, as with a new application, approval by a certificate manager is required.
Semiautomatic renewal
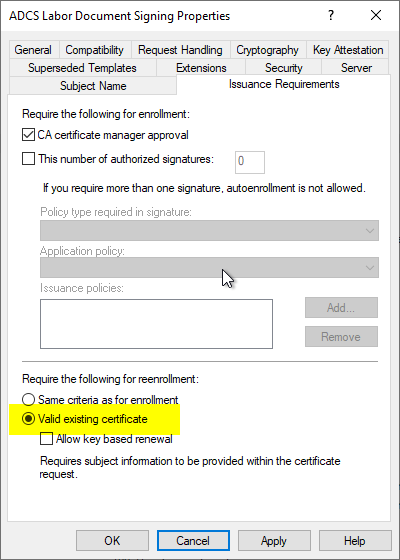
In the "Issuance Requirements" tab, you can activate the "Valid existing certificate" option in the "Require the following for reenrollment" section.
Workflow for the users
If a certificate is now approaching its expiration date, triggered by the autoenrollment process, the user is prompted to perform a certificate renewal. A corresponding notification appears on the desktop.
Please note that - if the user does not open and work through the dialog - the autoenrollment process for the logged-in user will stop and possibly not apply for further certificates either.
At least 80% of the certificate validity period must always have passed before the process is triggered. For more information, see the article "Planning of certificate validity and renewal period of end entity certificates with autoenrollment„.

As long as the process is not completed, a corresponding icon will also appear in the taskbar.
If the user clicks on the notification, a certificate request dialog appears.
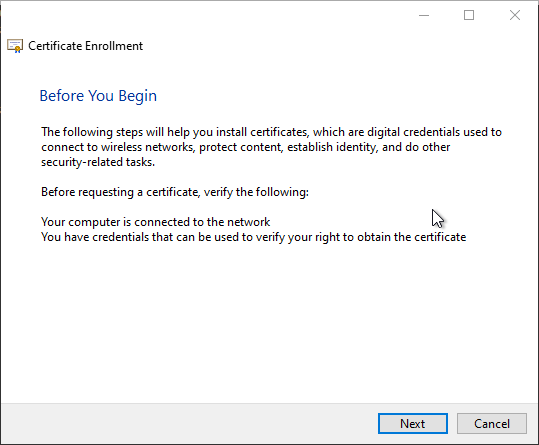
The corresponding certificate template is preselected and requires no further configuration. The identity is taken over on the previous certificate.
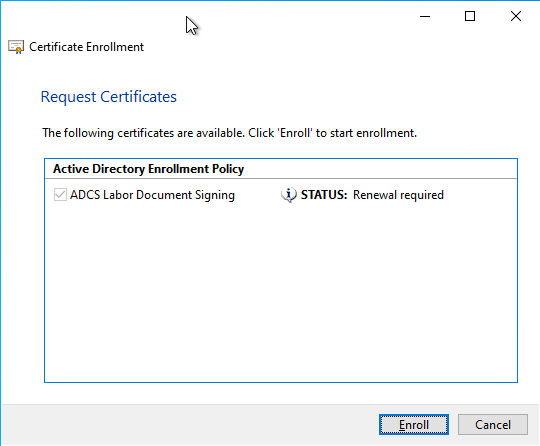
If the certificate request is sent to the certification authority, it issues the certificate directly and returns it to the user.
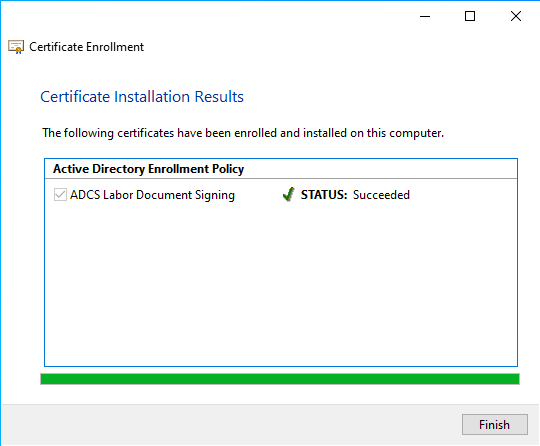
Newly submitted certificate requests will, of course, still require manual approval by a certificate manager.
Fully automatic renewal
If you want to spare the user any interaction, fully automatic renewal is also possible since Windows 8. To do this, the compatibility setting in the "General" tab of the certificate template must be changed to "Windows Server 2012" for the certification authority and "Windows 8" for the certificate recipient.
See also article "Overview of the availability of options when changing the compatibility settings of a certificate template" for an explanation of which compatibility settings enable which options.
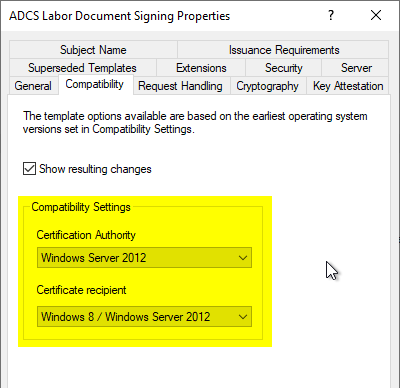
These settings have no effect on the Certificate template version and can thus also be set subsequently on a version 2 certificate template. For more information, see also the article "How are the compatibility settings for certificate templates technically mapped?„.
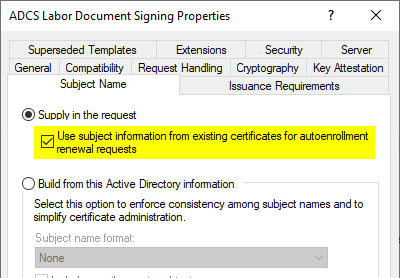
The changed compatibility setting enables a new option "Use subject information from existing certificates for autoenrollment renewal requests" in the Subject Name tab.
Now the "Autoenroll" permission must be assigned to the corresponding user group.
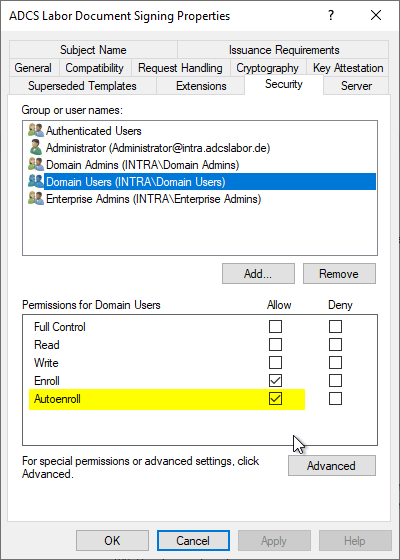
Of course, a corresponding group policy must also be configured for the users, which activates the autoenrollment process accordingly for the users.
Workflow for the users
The certificates are renewed fully automatically. Users are not prompted for certificate renewal and the certification authority will issue the certificates fully automatically.
Newly submitted certificate requests will, of course, still require manual approval by a certificate manager.
Side effects
However, users who have not yet applied for or do not have a certificate are now automatically prompted to apply for a certificate.
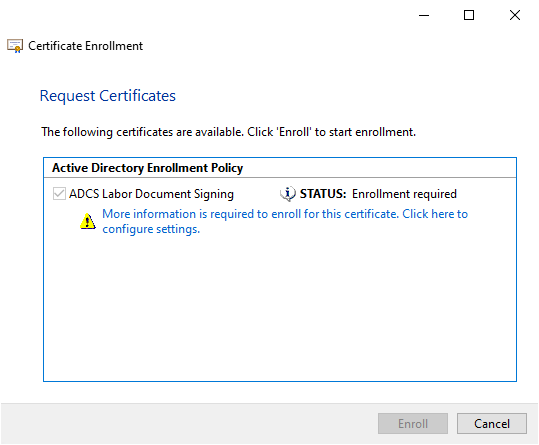
Please note that - if the user does not open and work through the dialog - the autoenrollment process for the logged-in user will stop and possibly not apply for further certificates either.
Safety concerns
When the certificate is renewed, the previous certificate is used to sign the certificate request and the Subject/Subject Alternative Name Information is compared with the new certificate request.
Hereby according to an old Microsoft blog article but not all fields are matched.
- In the case of online certificate templates (subject information is formed from the Active Directory), the initial certificate supposedly must contain a user principal name (UPN) or an e-mail address in the subject alternative name (SAN) for automatic approval to occur.
- With offline certificate templates, only the subject information is compared and the subject alternative name is supposedly ignored completely. Conversely, this would mean that a Subject Alternative Name could possibly be inserted here by means of a renewal request. A test for this is currently still pending.
Related links
External sources
- CA manager approval required for certificate re-enrollment (Microsoft, archive.org)
- Reenrollment using valid existing certificate (Microsoft TechNet Forums)
One thought on “Automatische Erneuerung manuell beantragter Zertifikate ohne Eingriff eines Zertifikatmanagers”
Comments are closed.