The Microsoft Certification Authority always signs certificates using the key associated with the most recent Certification Authority Certificate. The signing certificate for an OCSP response should be in accordance with RFC 6960 but signed by the same key as the certificate to be verified:
The CA SHOULD use the same issuing key to issue a delegation certificate as that used to sign the certificate being checked for revocation.
https://tools.ietf.org/html/rfc6960#section-4.2.2.2
However, if the certification authority certificate is renewed and a new key pair is used in the process, it is necessary for the online responder to continue to maintain valid signature certificates for the certificates issued with the previous certification authority certificate, since these are ultimately still valid and must be checked for revocation.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
To ensure this, it is therefore necessary for the online responder to maintain a corresponding revocation configuration for each certification authority key for which there are issued, time-valid certificates and to request signature certificates.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To ensure that the requested signature certificate is signed by the certification authority with the appropriate key, the respective certificate request contains an extension called "Authority Key Identifier" (AKI), through which the signature with this key can be requested by the certification authority.
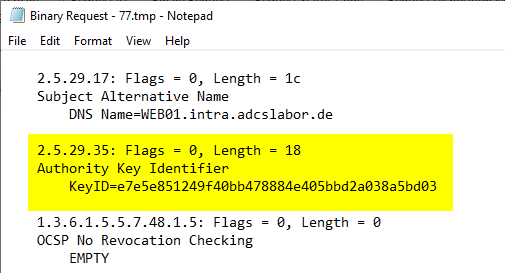
However, by default, the Microsoft Certification Authority will ignore the AKI extension and sign the certificate request with the most recent key.
In order to get the certification authority to consider the AKI extension, the following command line command must be executed on the certification authority:
certutil -setreg CA\UseDefinedCACertInRequest 1
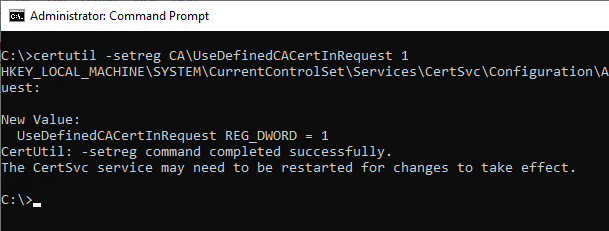
Afterwards, the Certification Authority service must be restarted for the changes to the configuration to be applied.
Related links:
- Certificate request fails with error message "The system cannot find the file specified. 0x80070002 (WIN32: 2 ERROR_FILE_NOT_FOUND)".
- Inspect a certificate request (CSR)
External sources
- RFC 6969 - X.509 Internet Public Key Infrastructure - Online Certificate Status Protocol - OCSP (Internet Engineering Task Force)
4 thoughts on “Die Beantragung eines bestimmten Signaturschlüssels auf einer Zertifizierungsstelle erlauben”
Comments are closed.