Assume the following scenario:
- An offline root certificate authority has been installed. The server on which the certificate authority is installed is not a domain member.
- This is configured for Active Directory blacklist publications.
- The blacklists are uploaded to the Active Directory using certutil -dspublish.
- The operation fails with the following error message:
certutil -dspublish "ADCS Labor Root CA.crl"
ldap:///CN=ADCS Lab Root CA,CN=ADCS Lab Root CA,CN=cdp,CN=Public Key Services,CN=Services,DC=UnavailableConfigDN?certificateRevocationList?base?objectClass=cRLDistributionPoint?certificateRevocationList
ldap: 0xa: LDAP_REFERRAL: 0000202B: RefErr: DSID-03100835, data 0, 1 access points
ref 1: 'unavailableconfigdn'
CertUtil: -dsPublish command FAILED: 0x8007202b (WIN32: 8235 ERROR_DS_REFERRAL)
CertUtil: A referral was returned from the server.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Sometimes it is necessary for a certificate issued by a certification authority to be withdrawn from circulation even before its expiration date. To make this possible, a certification authority keeps a revocation list. This is a signed file with a relatively short expiration date, which is used in combination with the certificate to check its validity.
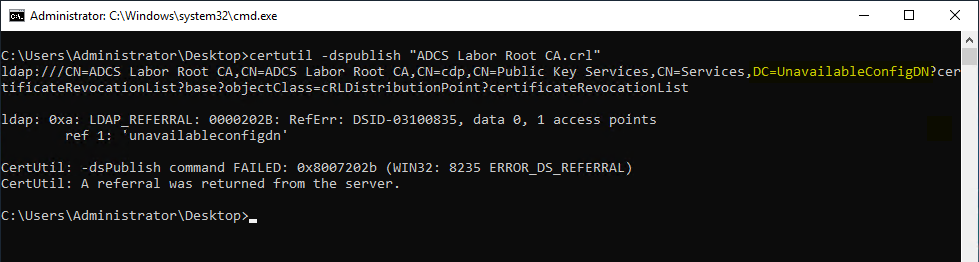
The location of the revocation lists in Active Directory is determined based on the Published CRL Locations extension within the revocation list. This extension is set based on the "Include in all CRLs. Specifies where to publish in the Active Directory when publishing manually." in the Extensions tab of the certificate authority configuration.
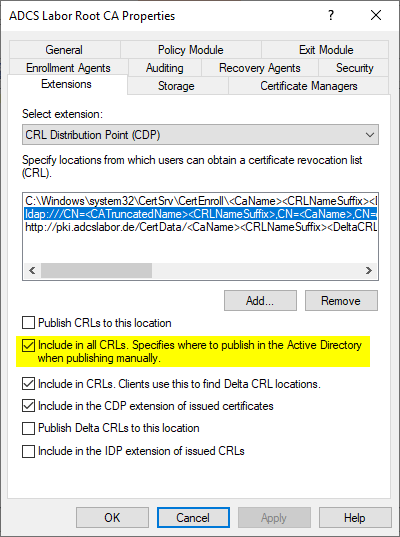
The LDAP path entered here contains a configuration variable {ConfigurationContainer}. This denotes the configuration partition within the Active Directory overall structure under which the Public Key Services objects are located.
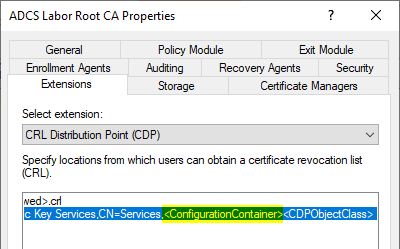
As you can see in this case, the generated brevocation list says "UnavailableConfigDN".
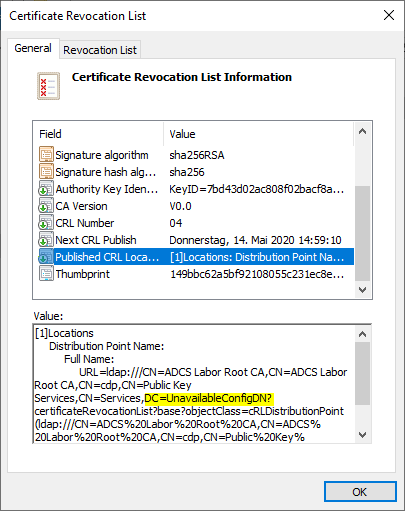
With an Active Directory integrated certification authority, the location of the configuration partition can be determined automatically based on the existing domain membership. This is not possible for an offline certification authority. The information must be determined in the registration of the certification authority service with the value DsConfigDN.
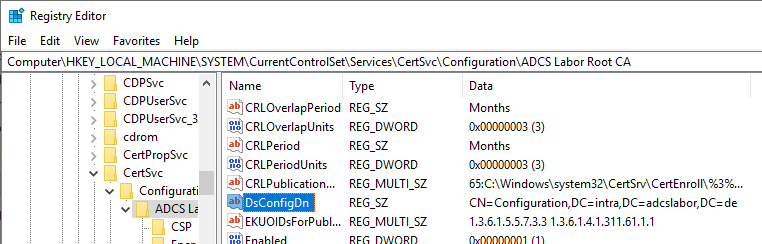
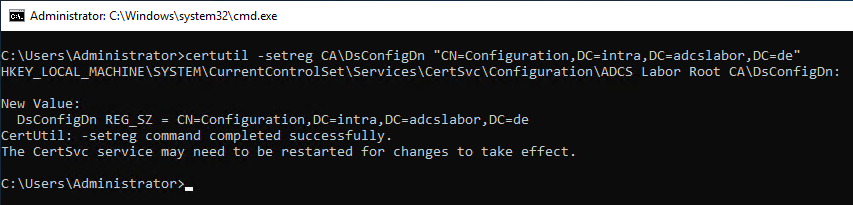
The value can be set either with the registry editor or with the following command line command:
certutil -setreg CA\DsConfigDN {Path to configuration partition}
After that, the certification authority service must be restarted.
net stop certsvc
net start certsvc
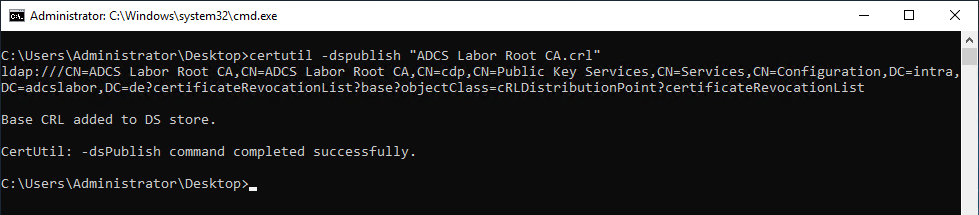
Likewise, a new revocation list still needs to be issued.
certutil -crl
Subsequently, the publication of the certificate revocation list should work.
One thought on “Die manuelle Veröffentlichung einer Zertifikatsperrliste (CRL) ins Active Directory schlägt fehl mit Fehlermeldung 0x8007202b (WIN32: 8235 ERROR_DS_REFERRAL)”
Comments are closed.