Assume the following scenario:
- For a certificate template, only the object identifier is shown, but not the display name and/or
- Queries against the certificate authority database contain only the object identifier for the certificate template ("CertificateTemplate" field), but not the display name.
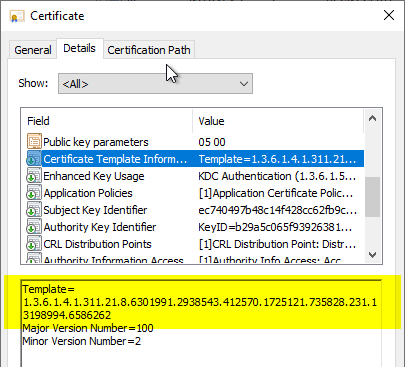
The error may also extend to queries against the certification authority database.
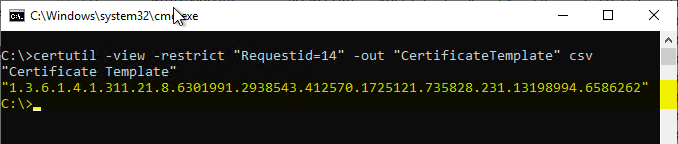
For comparison, a certificate template that correctly displays the display name:
Two cases must be distinguished in this problem:
- The certificate template was created recently
- The certificate template has existed for some time and has already worked
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The certificate template was created recently
If the certificate template was created recently, the corresponding information has probably not been replicated to the computer yet. The certificate template is stored as an Active Directory object. Each computer in the Active Directory forest will obtain the information from Active Directory via the autoenrollment process and cache it locally.
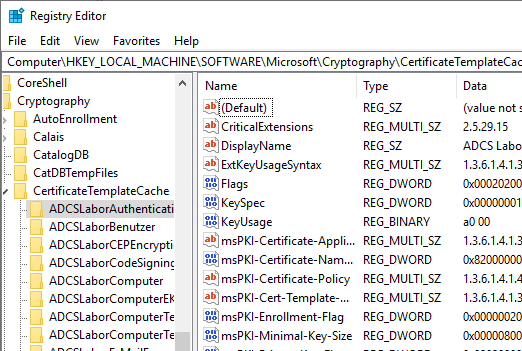
The cache for the currently logged in computer account is located in the following registry path:
HKEY_CURRENT_USER\Software\Microsoft\Cryptography\CertificateTemplateCache
The computer account cache is located in the following registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\CertificateTemplateCache
The process can be started manually with the following command line command:
certutil -pulse
For user accounts:
certutil -pulse -user
For more information see article "Manually running the autoenrollment process„.
The certificate template has existed for some time and has already worked
If the method described above does not lead to success, it should be checked whether a display name is assigned to the object identifiers.
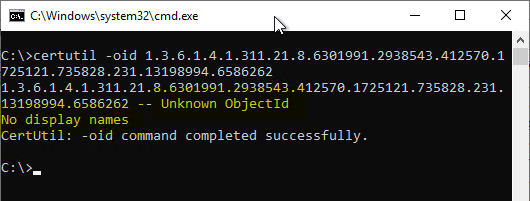
The following command line command can be used for a query against the local buffer:
certutil -oid {oid}
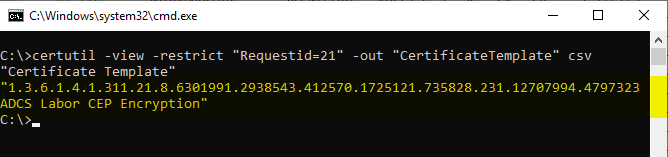
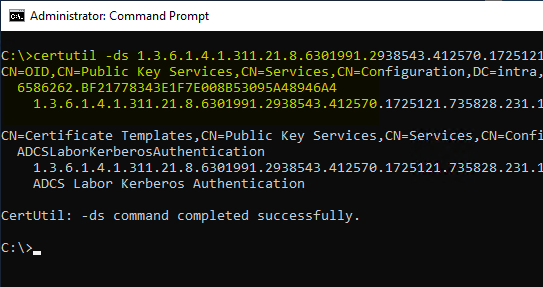
For a direct query against Active Directory, the following command line command can be used analogously:
certutil -ds {oid}
For comparison, a certificate template that correctly displays the display name:
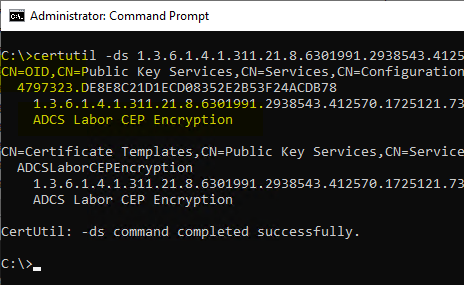
In this case, the "displayName" attribute on the OID object is not set. The OID objects are located in the configuration partition of the Active Directory forest.
CN=OID,CN=Public Key Services,CN=Services,CN=Configuration,{Forest-Root-Domain}
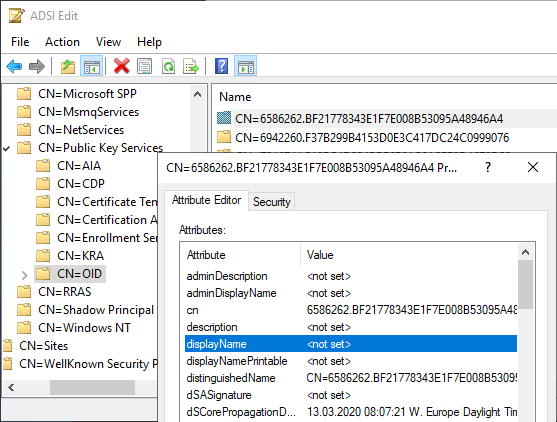
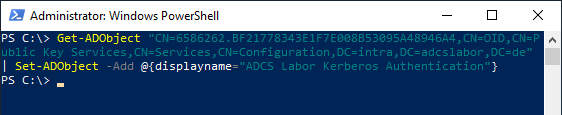
The attribute can be set with the ADSI Editor (adsiedit.msc) or the Windows PowerShell.
Get-ADObject "{LDAP-Path}" | Set-ADObject -Add @{displayname="{displayname}"}