| Event Source: | Microsoft Windows Security Auditing |
| Event ID: | 4880 (0x1310) |
| Event log: | Security |
| Event type: | Information |
| Event text (English): | Certificate Services started. Certificate Database Hash: %1 Private Key Usage Count: %2 CA Certificate Hash: %3 CA Public Key Hash: %4 |
| Event text (German): | The certificate services have been started. Certificate database hash: %1 Private key usage count: %2 Certification authority hash: %3 Certification authority public key hash: %4 |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: CertificateDatabaseHash (win:UnicodeString)
- %2: PrivateKeyUsageCount (win:UnicodeString)
- %3: CACertificateHash (win:UnicodeString)
- %4: CAPublicKeyHash (win:UnicodeString)
In contrast to operational events, which are often understood under the term "monitoring", auditing for the certification authority is the configuration of logging of security-relevant events.
Example events
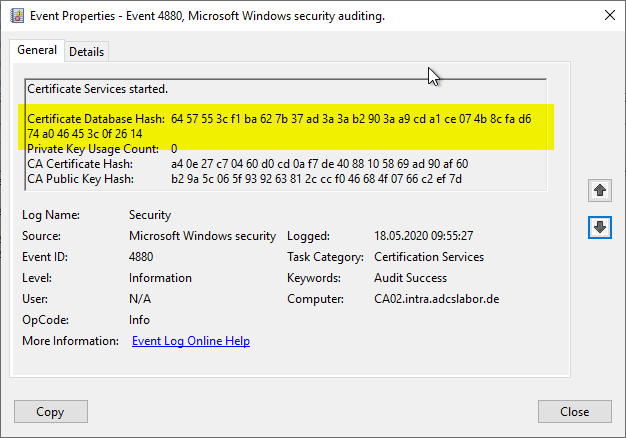
Certificate Services started.
Certificate Database Hash: 47 6d ba 0d f9 50 9c 56 37 8d 1a cf f4 04 82 43 41 35 69 16 d5 3e fe 98 06 e2 31 d4 1b 3a 08
Private Key Usage Count: 0
CA Certificate Hash: a4 0e 27 c7 04 60 d0 cd 0a f7 en 40 88 10 58 69 ad 90 af 60
CA Public Key Hash: b2 9a 5c 06 5f 93 92 63 81 2c cc f0 46 68 4f 07 66 c2 ef 7d
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
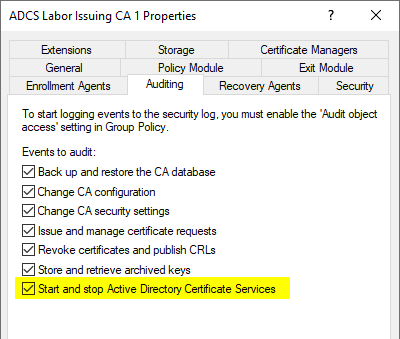
This event is logged if the "Start and stop Active Directory Certificate Services" option is enabled in the Certificate Authority audit settings.
Private Key Counting
If a hardware security module (HSM) is used that supports private key counting, and if this function is supported in the capolicy.inf of the certification authority, the number of corresponding accesses is logged under "Private Key Usage Count". This value can be compared with the value from the last Event no. 4881 to be able to detect possible accesses to the private key of the certification authority away from the certification authority service.
Checksum of the certification authority database
If this option is enabled, a checksum of the certification authority database is generated when the certification authority service is started and stopped. The checksums of these two events can be compared to detect offline tampering with the certification authority database.
However, this can cause performance problems for the certification authority. See article "Performance problems with auditing of "Start and stop Active Directory Certificate Services".„.
If an NDES server is installed and the certification authority has a very large database, the installation may even abort because of this. For this see article "Role configuration for the Network Device Enrollment Service (NDES) fails with error message "Failed to enroll RA certificates. The RPC server is unavailable. 0x800706ba (Win32: 1722 RPC_S_SERVER_UNAVAILABLE)".„.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If the checksum changes between exiting and starting the certification authority database, this may indicate that the certification authority database has been tampered with.
There are also legitimate reasons why the checksum of the certificate authority database has changed between quitting and starting the service, for example if the database has been defragmented. See also article "Compacting (defragmenting) the certification authority database„.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of audit events generated by the Certification Authority
- Overview of the audit events generated by the online responder (OCSP)
External sources
- Securing Public Key Infrastructure (PKI) (Microsoft)
3 thoughts on “Details zum Ereignis mit ID 4880 der Quelle Microsoft-Windows-Security-Auditing”
Comments are closed.