A useful hardening measure for Certification Authorities is to restrict the Certification Authority certificates so that they are only used for the actually issued extended key usage (Extended Key Usage) becomes familiar.
In the event of a compromise of the certification authority, the damage is then limited to these Extended Key Usages. The smart card logon extended key usage would then only be present in the certification authority certificate of the certification authority that actually issues such certificates.
End entity certificates have an "Extended Key Usage" extension that defines the purposes for which the certificate may be used (e.g., Transport Layer Security (TLS)).
Microsoft uses the term "Enhanced Key Usage", the correct name according to RFC 5280 is "Extended Key Usage"..
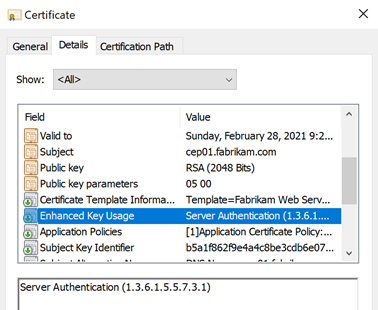
The Extended Key Usage defines for which purposes the certificate may be used. In the Microsoft Windows certificate dialog, this is indicated in the example by "Ensures the Identity of a Remote Computer" displayed.
The Details tab in the Windows certificate dialog shows the result of the policy check of the certificate, not the actual content of the certificate. This can be viewed in the Details tab and may well differ.
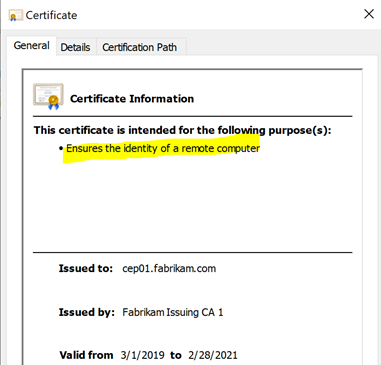
In the default configuration, a CA certificate is not restricted in terms of certificate types. The certificate lacks an Extended Key Usages extension, so the certificate can be used for all purposes. In the Microsoft Windows certificate dialog, this is indicated by "All Application Policies" displayed.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
A certification authority can be restricted in its usability by adding an Extended Key Usages extension. It can then only issue certificates for the defined EKUs.
This procedure is known as qualified subordination or constraints. Before a certification authority is put into operation, it is usually already defined which certificate types it will issue. This means that the corresponding extended key usages can be worked out from these.
The following describes how to restrict imported root certificates in terms of the extended key usages that can be used for them.
For Certification Authority certificates from own Certification Authorities see article "Basics: Restricting Extended Key Usage (EKU) in Certification Authority Certificates„.
The following Extended Key Usages are typical candidates for a corresponding restriction:
| OID | Description |
|---|---|
| 1.3.6.1.4.1.311.20.2.1 | Certificate Request Agent |
| 1.3.6.1.5.5.7.3.2 | Client Authentication |
| 1.3.6.1.5.5.7.3.3 | Code Signing |
| 1.3.6.1.4.1.311.10.3.13 | Lifetime Signing |
| 1.3.6.1.4.1.311.10.3.12 | Document Signing |
| 1.3.6.1.4.1.311.80.1 | Document Encryption |
| 1.3.6.1.4.1.311.10.3.4 | Encrypting file system |
| 1.3.6.1.4.1.311.10.3.4.1 | File Recovery |
| 1.3.6.1.5.5.7.3.5 | IP Security End System |
| 1.3.6.1.5.5.8.2.2 | IP Security IKE Intermediate |
| 1.3.6.1.5.5.7.3.6 | IP Security Tunnel Endpoint |
| 1.3.6.1.5.5.7.3.7 | IP Security User |
| 1.3.6.1.4.1.311.21.6 | Key Recovery Agent |
| 1.3.6.1.4.1.311.10.3.11 | Key Recovery |
| 1.3.6.1.5.2.3.5 | KDC Authentication |
| 1.3.6.1.4.1.311.10.3.1 | Microsoft Trust List Signing |
| 1.3.6.1.4.1.311.10.3.10 | Qualified Subordination |
| 1.3.6.1.4.1.311.10.3.9 | Root List Signer |
| 1.3.6.1.5.5.7.3.4 | Secure E-mail |
| 1.3.6.1.5.5.7.3.1 | Server Authentication |
| 1.3.6.1.4.1.311.20.2.2 | Smartcard Logon |
| 1.3.6.1.5.5.7.3.8 | Time Stamping according to RFC 3161 |
| 1.3.6.1.5.5.7.3.9 | OCSP Signing |
| 1.3.6.1.4.1.311.54.1.2 | Remote Desktop Authentication |
| 1.3.6.1.4.1.311.21.5 | Private Key Archival |
| 2.16.840.1.113741.1.2.3 | Intel Advanced Management Technology (AMT) Provisioning |
To implement the restriction, there are several methods:
- Restrict EKU via Microsoft Management Console (MMC)
- Restrict EKU via group policies
- Restrict EKU via command line (or script)
Restrict EKU via Microsoft Management Console (MMC)
Restricting Extended Key Usages can be done via the Microsoft Management Console (MMC) for certificates on any Windows computer.
The following management consoles are available.
- User certificate store: certmgr.msc
- Computer certificate store: cerlm.msc (administrator permissions required)
In the certificate store for trusted root certification authorities, you can access the properties of each certificate by right-clicking and selecting "Properties".
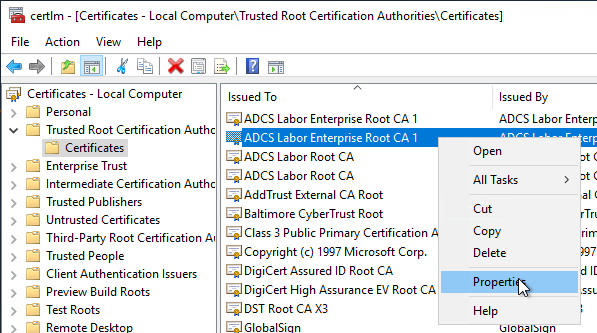
The Extended Key Usages can then be configured in the "General" tab.
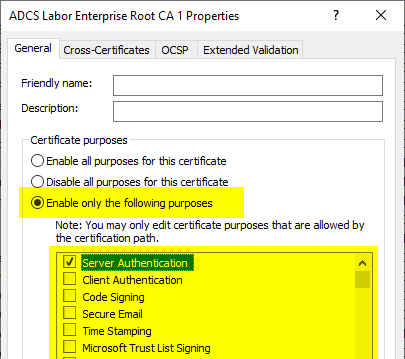
The restriction is then mapped in the properties dialog.
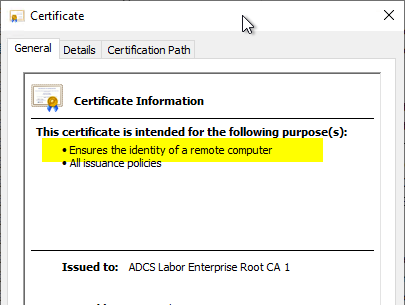
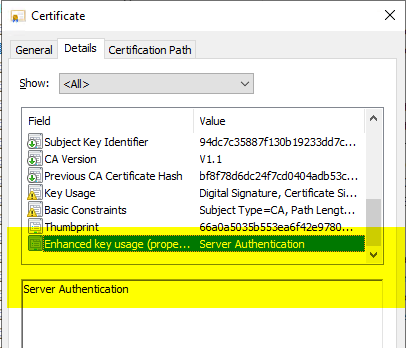
If you look at the details of the certificate, you will notice that the extended key usages (logically, since the actual certificate cannot be changed without damaging its signature) are not mapped as an extension, but via a property.
Restrict EKU via group policies
Restricting Extended Key Usages via the Microsoft Management Console on each computer individually has the disadvantage that this method cannot be used for automation or application to a large number of machines.
For this purpose, the use of a group policy is recommended, which can then be applied centrally to all machines.
However, in order to be able to restrict the EKU via group policies, the certificate must also be distributed via these.
It is essential to check whether the certificate is still distributed to the machines by other means - for example, via the Public Key Services object in Active Directory, otherwise the restrictions may not be effective if an unrestricted version of the certificate is distributed by other means.
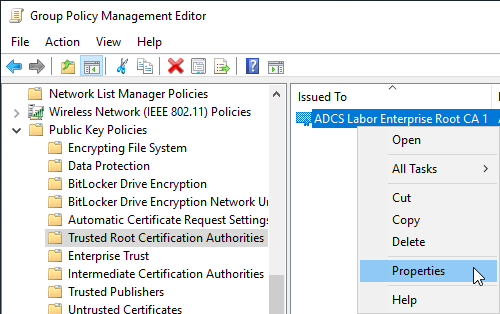
The setting can be found in the group policy configuration under "Computer Configuration" - "Policies" - "Windows Settings" - "Security Settings" - "Public Key Policies" - "Trusted Root Certification Authorities".
First, the certificate in question must be imported.
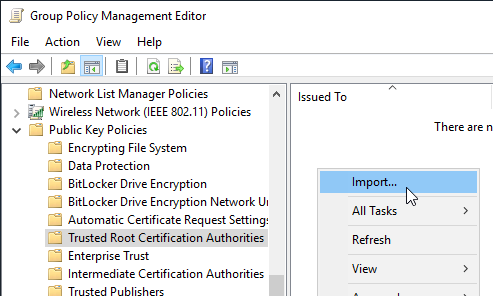
Afterwards, the imported certificate can be right-clicked and the option "Properties" "Properties" can be selected. The configuration then happens analog to the method with the local MMC.
Restrict EKU via command line (or script)
If no group policies are available, or if you do not want to use them for other reasons, you still have the option of configuring via command line or script.
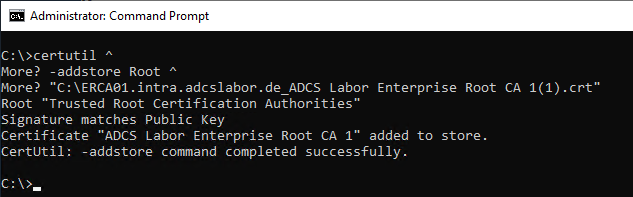
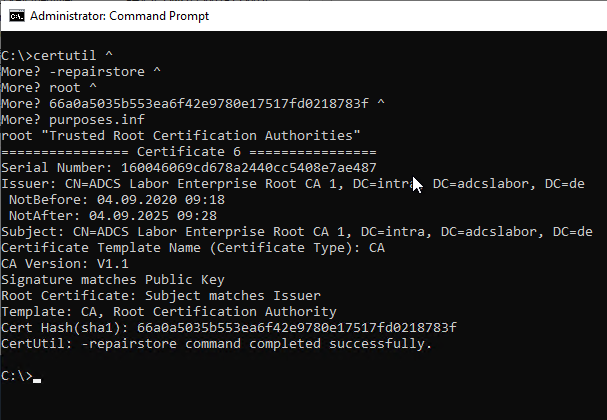
First, the certificate must be imported into the local trusted root certificate authority store using the following command.
certutil -addstore "Root" "{filename-certificate}.crt"
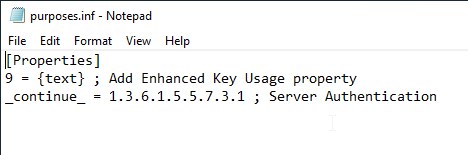
The restriction of the extended key usages is done by a separate command, which applies a configuration file. In the example, a file "purposes.inf" is created.
[Properties]
9 = {text} ; Add Extended Key Usage property
_continue_ = 1.3.6.1.5.5.7.3.1 ; Server Authentication
Further extended key usages can be entered by additional "_continue_" lines. The list of the most common extended key usages can be found at the beginning of this article.
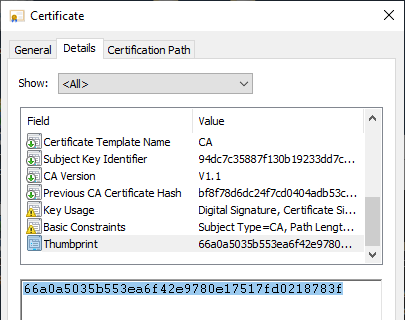
The file is then applied to the imported root certificate authority. For this purpose, it must be identified by its SHA1 thumbprint. The necessary information can be found, for example, in the properties dialog of the certificate.
Afterwards, the file can be applied with the following command line command:
certutil -repairstore root {Thumbprint} "purposes.inf"
3 thoughts on “Die erweiterte Schlüsselverwendung (Extended Key Usage, EKU) für importierte Stammzertifizierungstellen-Zertifikate einschränken”
Comments are closed.